- (Exam Topic 3)
A company is implementing MFA for all applications that store sensitive data. The IT manager wants MFA to be non-disruptive and user friendly Which of the following technologies should the IT manager use when implementing MFA?
Correct Answer:
C
Push notifications are a type of technology that allows an application or a service to send messages or alerts to a user’s device without requiring the user to open the application or the service. They can be used for multi-factor authentication (MFA) by sending a prompt or a code to the user’s device that the user has to approve or enter to verify their identity. They can be non-disruptive and user friendly because they do not require the user to remember or type anything, and they can be delivered instantly and securely.
- (Exam Topic 1)
During an investigation, the incident response team discovers that multiple administrator accounts were suspected of being compromised. The host audit logs indicate a repeated brute-force attack on a single administrator account followed by suspicious logins from unfamiliar geographic locations. Which of the following data sources would be BEST to use to assess the accounts impacted by this attack?
Correct Answer:
A
User behavior analytics (UBA) would be the best data source to assess the accounts impacted by the attack, as it can identify abnormal activity, such as repeated brute-force attacks and logins from unfamiliar geographic locations, and provide insights into the behavior of the impacted accounts. References: CompTIA Security+ Study Guide, Exam SY0-601, 4th Edition, Chapter 7: Incident Response, pp. 338-341
- (Exam Topic 4)
A cybersecurity analyst reviews the log files from a web server end sees a series of files that indicate a directory traversal attack has occurred Which of the following is the analyst most likely seeing?
Correct Answer:
C
The log files show that the attacker was able to access files and directories that were not intended to be accessible by web users, such as “/etc/passwd” and “/var/log”. This indicates that the attacker was able to exploit a vulnerability in the web server or application that allowed them to manipulate the file path and access arbitrary files on the server. This is a type of attack known as directory traversal, which can lead to information disclosure, privilege escalation, or remote code execution3.
- (Exam Topic 1)
A security analyst is investigating multiple hosts that are communicating to external IP addresses during the hours of 2:00 a.m - 4:00 am. The malware has evaded detection by traditional antivirus software. Which of the following types of malware is MOST likely infecting the hosts?
Correct Answer:
A
Based on the given information, the most likely type of malware infecting the hosts is a RAT (Remote Access Trojan). RATs are often used for stealthy unauthorized access to a victim's computer, and they can evade traditional antivirus software through various sophisticated techniques. In particular, the fact that the malware is communicating with external IP addresses during specific hours suggests that it may be under the control of an attacker who is issuing commands from a remote location. Ransomware, polymorphic malware, and worms are also possible culprits, but the context of the question suggests that a RAT is the most likely answer.
- (Exam Topic 2)
Leveraging the information supplied below, complete the CSR for the server to set up TLS (HTTPS)
• Hostname: ws01
• Domain: comptia.org
• IPv4: 10.1.9.50
• IPV4: 10.2.10.50
• Root: home.aspx
• DNS CNAME:homesite. Instructions:
Drag the various data points to the correct locations within the CSR. Extension criteria belong in the let hand column and values belong in the corresponding row in the right hand column.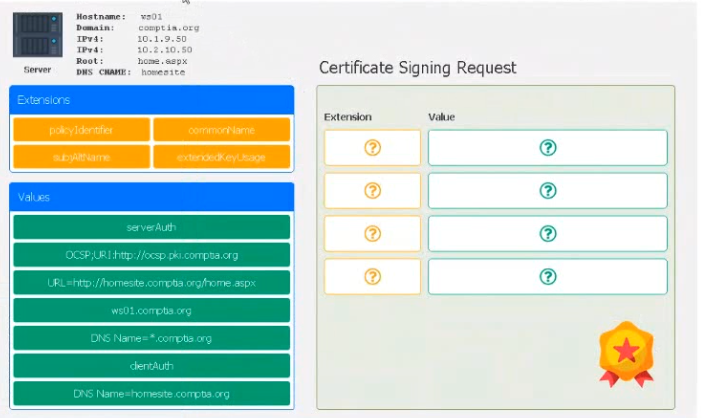
Solution:
Graphical user interface, application Description automatically generated
Does this meet the goal?
Correct Answer:
A

