- (Exam Topic 2)
An organization recently released a software assurance policy that requires developers to run code scans each night on the repository. After the first night, the security team alerted the developers that more than 2,000 findings were reported and need to be addressed. Which of the following is the MOST likely cause for the high number of findings?
Correct Answer:
A
The most likely cause for the high number of findings is that the vulnerability scanner was not properly configured and generated a high number of false positives. False positive results occur when a vulnerability scanner incorrectly identifies a non-vulnerable system or application as being vulnerable. This can happen due to incorrect configuration, over-sensitive rule sets, or outdated scan databases.
https://www.professormesser.com/security-plus/sy0-601/sy0-601-video/sy0-601-comptia-security-plus-course/
- (Exam Topic 4)
An organization's Chief Security Officer (CSO) wants to validate the business's involvement in the incident response plan to ensure its validity and thoroughness. Which of the following will the CSO most likely use?
Correct Answer:
C
A tabletop exercise is a type of simulation exercise that involves discussing hypothetical scenarios and testing the incident response plan in a low-stress environment. A tabletop exercise can help the CSO to validate the business’s involvement in the incident response plan by involving key stakeholders, such as senior management, business units, legal department, etc., in the discussion and evaluation of the plan.
- (Exam Topic 2)
An employee's laptop was stolen last month. This morning, the was returned by the A cyberrsecurity analyst retrieved laptop and has since cybersecurity incident checklist Four incident handlers are responsible for executing the checklist. Which of the following best describes the process for evidence collection assurance?
Correct Answer:
B
Chain of custody is a process that documents the chronological and logical sequence of custody, control, transfer, analysis, and disposition of materials, including physical or electronic evidence. Chain of custody is important to ensure the integrity and admissibility of evidence in legal proceedings. Chain of custody can help evidence collection assurance by providing proof that the evidence has been handled properly and has not been tampered with or contaminated.
References: https://www.comptia.org/certifications/security#examdetails https://www.comptia.org/content/guides/comptia-security-sy0-601-exam-objectives https://www.thoughtco.com/chain-of-custody-4589132
- (Exam Topic 4)
A security administrator received an alert for a user account with the following log activity: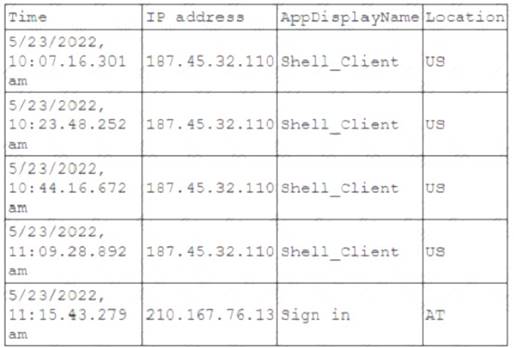
Which of the following best describes the trigger for the alert the administrator received?
Correct Answer:
C
Impossible travel time is an anomaly detection that indicates a possible compromise of a user account. It occurs when the same user connects from two different countries and the time between those connections is shorter than the time it would take to travel from the first location to the second by conventional means. This suggests that a different user is using the same credentials or that a proxy or VPN is being used to mask the true location. The log activity shows that the user connected from two different IP addresses in different countries (US and Brazil) within a span of 37 minutes, which is impossible to achieve by normal
travel. References: Detecting and Remediating Impossible Travel - Microsoft Community Hub; Anomaly
detection policies - Microsoft Defender for Cloud Apps; Understanding Microsoft 365 Impossible Travel Rules | Blumira
- (Exam Topic 3)
A customer called a company's security team to report that all invoices the customer has received over the last five days from the company appear to have fraudulent banking details. An investigation into the matter reveals the following
• The manager of the accounts payable department is using the same password across multiple external websites and the corporate account
• One of the websites the manager used recently experienced a data breach.
• The manager's corporate email account was successfully accessed in the last five days by an IP address located in a foreign country.
Which of the following attacks has most likely been used to compromise the manager's corporate account?
Correct Answer:
D
Credential stuffing is a type of attack that involves using stolen or leaked usernames and passwords from one website or service to gain unauthorized access to other websites or services that use the same credentials. It can exploit the common practice of reusing passwords across multiple accounts. It is the most likely attack tha has been used to compromise the manager’s corporate account, given that the manager is using the same password across multiple external websites and the corporate account, and one of the websites recently experienced a data breach.

