- (Exam Topic 3)
A security analyst is looking for a solution to help communicate to the leadership team the seventy levels of the organization's vulnerabilities. Which of the following would best meet this need?
Correct Answer:
D
CVSS (Common Vulnerability Scoring System) is a framework and a metric that provides a standardized and consistent way of assessing and communicating the severity levels of vulnerabilities. It assigns a numerical score and a vector string to each vulnerability based on various factors, such as exploitability, impact, scope, etc. It can help communicate to the leadership team the severity levels of the organization’s vulnerabilities by providing a quantitative and qualitative measure of the risks and the potential impacts.
- (Exam Topic 1)
A systems engineer is building a new system for production. Which of the following is the FINAL step to be performed prior to promoting to production?
Correct Answer:
C
Running a vulnerability scan is the final step to be performed prior to promoting a system to production. This allows any remaining security issues to be identified and resolved before the system is put into production. References: CompTIA Security+ Study Guide, Exam SY0-601, 4th Edition, Chapter 3
- (Exam Topic 4)
A systems administrator set up an automated process that checks for vulnerabilities across the entire
environment every morning. Which of the following activities is the systems administrator conducting?
Correct Answer:
A
Scanning is the activity of checking for vulnerabilities across the network, systems, or applications. It can be done manually or automatically using tools such as vulnerability scanners, port scanners, or network mappers. Scanning can help identify and remediate potential security issues before they are exploited.
- (Exam Topic 2)
A security analyst is investigating a report from a penetration test. During the penetration test, consultants were able to download sensitive data from a back-end server. The back-end server was exposing an API that should have only been available from the company’s mobile application. After reviewing the back-end server logs, the security analyst finds the following entries: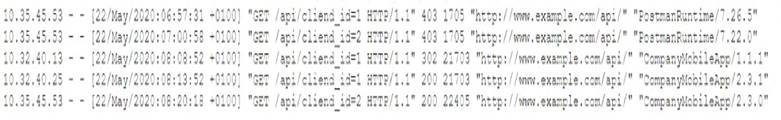
Which of the following is the most likely cause of the security control bypass?
Correct Answer:
B
User-agent spoofing is a technique that involves changing the user-agent string of a web browser or other client to impersonate another browser or device. The user-agent string is a piece of information that identifies the client to the web server and can contain details such as the browser name, version, operating system, and device type. User-agent spoofing can be used to bypass security controls that rely on the user-agent string to determine the legitimacy of a request. In this scenario, the consultants were able to spoof the user-agent string of the company’s mobile application and access the API that should have been restricted to it.
- (Exam Topic 2)
A junior human resources administrator was gathering data about employees to submit to a new company awards program The employee data included job title business phone number location first initial with last name and race Which of the following best describes this type of information?
Correct Answer:
B
Non-PII stands for non-personally identifiable information, which is any data that does not directly identify a specific individual. Non-PII can include information such as job title, business phone number, location, first initial with last name, and race. Non-PII can be used for various purposes, such as statistical analysis, marketing, or research. However, non-PII may still pose some privacy risks if it is combined or linked with other data that can reveal an individual’s identity.
References: https://www.comptia.org/certifications/security#examdetails
https://www.comptia.org/content/guides/comptia-security-sy0-601-exam-objectives https://www.investopedia.com/terms/n/non-personally-identifiable-information-npii.asp

