- (Exam Topic 3)
A user enters a password to log in to a workstation and is then prompted to enter an authentication code Which of the following MFA factors or attributes are being utilized in the authentication process? {Select two).
Correct Answer:
AB
MFA (Multi-Factor Authentication) is a method of verifying a user’s identity by requiring two or more factors or attributes that belong to different categories. The categories are something you know (such as a password or a PIN), something you have (such as a token or a smart card), something you are (such as a fingerprint or an iris scan), something you do (such as a gesture or a voice command), and somewhere you are (such as a location or an IP address). In this case, the user enters a password (something you know) and then receives an authentication code (something you have) to log in to a workstation.
- (Exam Topic 3)
A manufacturing company has several one-off legacy information systems that cannot be migrated to a newer OS due to software compatibility issues. The OSs are still supported by the vendor but the industrial software is no longer supported The Chief Information Security Officer has created a resiliency plan for these systems that will allow OS patches to be installed in a non-production environment, white also creating backups of the systems for recovery. Which of the following resiliency techniques will provide these capabilities?
Correct Answer:
D
Virtual machines are software-based simulations of physical computers that run on a host system and share its resources. They can provide resiliency for legacy information systems that cannot be migrated to a newer OS due to software compatibility issues by allowing OS patches to be installed in a non-production environment without affecting the production environment. They can also create backups of the systems for recovery by taking snapshots or copies of the virtual machine files.
- (Exam Topic 3)
Which of the following security concepts should an e-commerce organization apply for protection against erroneous purchases?
Correct Answer:
C
Integrity is a security concept that ensures that data is accurate, complete and consistent, and that it has not been tampered with or modified in an unauthorized or unintended way. Integrity is important for e-commerce organizations to protect against erroneous purchases, as it can prevent data corruption, duplication, loss or manipulation that could affect the transactions or the records of the customers. Integrity can be achieved by using methods such as hashing, digital signatures, checksums, encryption and access control. Verified References: Security+ (Plus) Certification | CompTIA IT Certifications https://www.comptia.org/certifications/security (See What Skills Will You Learn?)
Security+ (Plus) Certification | CompTIA IT Certifications https://www.comptia.org/certifications/security (See What Skills Will You Learn?) CompTIA Security+ 601 - Infosec
CompTIA Security+ 601 - Infosec
https://www.infosecinstitute.com/wp-content/uploads/2021/03/CompTIA-Security-eBook.pdf (See Security+: 5 in-demand cybersecurity skills) CompTIA Security+ SY0-601 Certification Study Guide https://www.comptia.org/training/books/security-sy0-601-study-guide (See Chapter 1: Threats, Attacks and Vulnerabilities, Section 1.4: Cryptography and PKI)
CompTIA Security+ SY0-601 Certification Study Guide https://www.comptia.org/training/books/security-sy0-601-study-guide (See Chapter 1: Threats, Attacks and Vulnerabilities, Section 1.4: Cryptography and PKI)
- (Exam Topic 1)
During an incident a company CIRT determine it is necessary to observe the continued network-based transaction between a callback domain and the malware running on an enterprise PC. Which of the following techniques would be BEST to enable this activity while reducing the risk of lateral spread and the risk that the adversary would notice any changes?
Correct Answer:
C
To observe the continued network-based transaction between a callback domain and the malware running on an enterprise PC while reducing the risk of lateral spread and the risk that the adversary would notice any changes, the best technique to use is to emulate the malware in a heavily monitored DMZ segment. This is a secure environment that is isolated from the rest of the network and can be heavily monitored to detect any suspicious activity. By emulating the malware in this environment, the activity can be observed without the risk of lateral spread or detection by the adversary. References:
https://www.sans.org/blog/incident-response-fundamentals-why-is-the-dmz-so-important/
- (Exam Topic 2)
A company recently added a DR site and is redesigning the network. Users at the DR site are having issues browsing websites.
INSTRUCTIONS
Click on each firewall to do the following:
* 1. Deny cleartext web traffic
* 2. Ensure secure management protocols are used.
* 3. Resolve issues at the DR site.
The ruleset order cannot be modified due to outside constraints.
Hat any time you would like to bring back the initial state of the simulation, please dick the Reset All button.


Solution:
In Firewall 1, HTTP inbound Action should be DENY. As shown below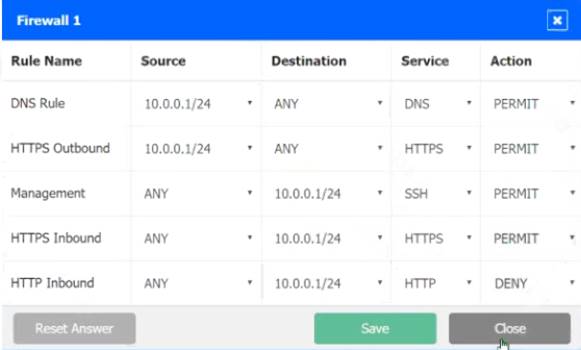
In Firewall 2, Management Service should be DNS, As shown below.
In Firewall 3, HTTP Inbound Action should be DENY, as shown below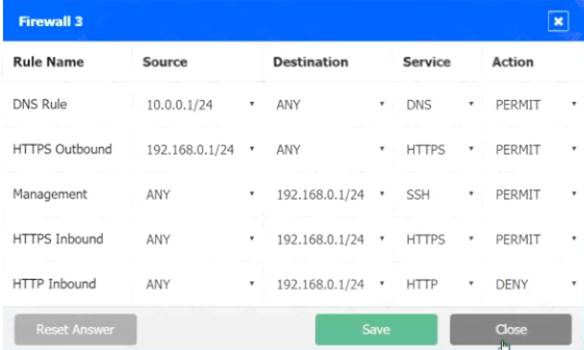
Does this meet the goal?
Correct Answer:
A

