- (Exam Topic 2)
A network administrator needs to determine Ihe sequence of a server farm's logs. Which of the following should the administrator consider? (Select TWO).
Correct Answer:
DF
A server farm’s logs are records of events that occur on a group of servers that provide the same service or function. Logs can contain information such as date, time, source, destination, message, error code, and severity level. Logs can help administrators monitor the performance, security, and availability of the servers and troubleshoot any issues.
To determine the sequence of a server farm’s logs, the administrator should consider the following factors: Time stamps: Time stamps are indicators of when an event occurred on a server. Time stamps can help administrators sort and correlate events across different servers based on chronological order. However, time stamps alone may not be sufficient to determine the sequence of events if the servers have different time zones or clock settings.
Time stamps: Time stamps are indicators of when an event occurred on a server. Time stamps can help administrators sort and correlate events across different servers based on chronological order. However, time stamps alone may not be sufficient to determine the sequence of events if the servers have different time zones or clock settings. Time offset: Time offset is the difference between the local time of a server and a reference time, such as Coordinated Universal Time (UTC) or Greenwich Mean Time (GMT). Time offset can help administrators adjust and synchronize the time stamps of different servers to a common reference time and eliminate any discrepancies caused by time zones or clock settings.
Time offset: Time offset is the difference between the local time of a server and a reference time, such as Coordinated Universal Time (UTC) or Greenwich Mean Time (GMT). Time offset can help administrators adjust and synchronize the time stamps of different servers to a common reference time and eliminate any discrepancies caused by time zones or clock settings.
References: https://www.comptia.org/certifications/security#examdetails https://www.comptia.org/content/guides/comptia-security-sy0-601-exam-objectives https://docs.microsoft.com/en-us/windows-server/administration/server-manager/view-event-logs
- (Exam Topic 1)
A junior security analyst is reviewing web server logs and identifies the following pattern in the log file: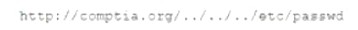
Which ol the following types of attacks is being attempted and how can it be mitigated?
Correct Answer:
C
Detailed explanation
The attack being attempted is directory traversal, which is a web application attack that allows an attacker to access files and directories outside of the web root directory. A WAF can help mitigate this attack by detecting and blocking attempts to access files outside of the web root directory.
References: CompTIA Security+ Study Guide: Exam SY0-601, Chapter 4: Securing Application Development and Deployment, p. 191
- (Exam Topic 3)
A security engineer is setting up passwordless authentication for the first time. INSTRUCTIONS
Use the minimum set of commands to set this up and verify that it works. Commands cannot be reused.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.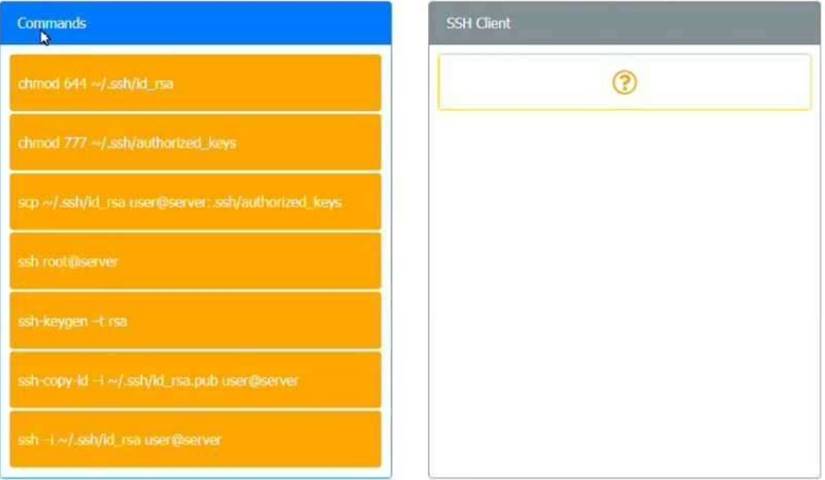
Solution:
A screenshot of a computer Description automatically generated with medium confidence
Does this meet the goal?
Correct Answer:
A
- (Exam Topic 2)
A company is concerned about individuals driving a car into the building to gain access. Which of the following security controls would work BEST to prevent this from happening?
Correct Answer:
A
Bollards are posts designed to prevent vehicles from entering an area. They are usually made of steel or concrete and are placed close together to make it difficult for vehicles to pass through. In addition to preventing vehicles from entering an area, bollards can also be used to protect buildings and pedestrians from ramming attacks. They are an effective and cost-efficient way to protect buildings and pedestrians from unauthorized access.
- (Exam Topic 2)
Which of the following can be used to detect a hacker who is stealing company data over port 80?
Correct Answer:
D
 Using a SIEM tool to monitor network traffic in real-time and detect any anomalies or malicious activities
Using a SIEM tool to monitor network traffic in real-time and detect any anomalies or malicious activities Monitoring all network protocols and ports to detect suspicious volumes of traffic or connections to uncommon IP addresses
Monitoring all network protocols and ports to detect suspicious volumes of traffic or connections to uncommon IP addresses Monitoring for outbound traffic patterns that indicate malware communication with command and control servers, such as beaconing or DNS tunneling
Monitoring for outbound traffic patterns that indicate malware communication with command and control servers, such as beaconing or DNS tunneling Using a CASB tool to control access to cloud resources and prevent data leaks or downloads
Using a CASB tool to control access to cloud resources and prevent data leaks or downloads Encrypting data at rest and in transit and enforcing strong authentication and authorization policies
Encrypting data at rest and in transit and enforcing strong authentication and authorization policies

