- (Exam Topic 3)
Which of the following is a primary security concern for a company setting up a BYOD program?
Correct Answer:
D
Jailbreaking is a process of bypassing or removing the manufacturer-imposed restrictions on a mobile device’s operating system, allowing users to install unauthorized applications, modify settings, etc. It is a primary security concern for setting up a BYOD program because it can expose the device and its data to malware, vulnerabilities, unauthorized access, etc.
- (Exam Topic 4)
Security analysts are conducting an investigation of an attack that occurred inside the organization's network. An attacker was able to coiled network traffic between workstations throughout the network The analysts review the following logs: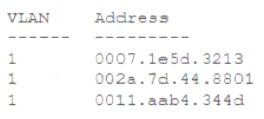
The Layer 2 address table has hundreds of entries similar to the ones above Which of the following attacks has most likely occurred?
Correct Answer:
C
- (Exam Topic 1)
A security analyst must enforce policies to harden an MDM infrastructure. The requirements are as follows:
* Ensure mobile devices can be tracked and wiped.
* Confirm mobile devices are encrypted.
Which of the following should the analyst enable on all the devices to meet these requirements?
Correct Answer:
A
Geofencing is a technology used in mobile device management (MDM) to allow administrators to define geographical boundaries within which mobile devices can operate. This can be used to enforce location-based policies, such as ensuring that devices can be tracked and wiped if lost or stolen. Additionally, encryption can be enforced on the devices to ensure the protection of sensitive data in the event of theft or loss. References: CompTIA Security+ Study Guide, Exam SY0-601, 4th Edition, Chapter 7
CompTIA Security+ Study Guide, Exam SY0-601, 4th Edition, Chapter 7
- (Exam Topic 2)
An attacker is targeting a company. The attacker notices that the company’s employees frequently access a particular website. The attacker decides to infect the website with malware and hopes the employees’ devices will also become infected. Which of the following techniques is the attacker using?
Correct Answer:
A
a watering hole attack is a form of cyberattack that targets a specific group of users by infecting websites that they commonly visit123. The attacker seeks to compromise the user’s computer and gain access to the network at the user’s workplace or personal data123. The attacker observes the websites often visited by the victim or the group and infects those sites with malware14. The attacker may also lure the user to a malicious 4site. A watering hole attack is difficult to diagnose and poses a significant threat to websites and users2 .
- (Exam Topic 2)
A network-connected magnetic resonance imaging (MRI) scanner at a hospital is controlled and operated by an outdated and unsupported specialized Windows OS. Which of the following
is most likely preventing the IT manager at the hospital from upgrading the specialized OS?
Correct Answer:
B
This option is the most likely reason for preventing the IT manager at the hospital from upgrading the specialized OS. The MRI scanner is a complex and sensitive device that requires a specific OS to control and operate it. The MRI vendor may not have developed or tested newer versions of the OS for compatibility and functionality with the scanner. Upgrading the OS without the vendor’s support may cause the scanner to malfunction or stop working altogether.

