- (Exam Topic 4)
You have a Microsoft 365 tenant.
All users must use the Microsoft Authenticator app for multi-factor authentication (MFA) when accessing Microsoft 365 services.
Some users report that they received an MFA prompt on their Microsoft Authenticator app without initiating a sign-in request.
You need to block the users automatically when they report an MFA request that they did not Initiate. Solution: From the Azure portal, you configure the Fraud alert settings for multi-factor authentication (MFA). Does this meet the goal?
Correct Answer:
A
The fraud alert feature lets users report fraudulent attempts to access their resources. When an unknown and suspicious MFA prompt is received, users can report the fraud attempt using the Microsoft Authenticator app or through their phone.
The following fraud alert configuration options are available:  Automatically block users who report fraud.
Automatically block users who report fraud. Code to report fraud during initial greeting. Reference:
Code to report fraud during initial greeting. Reference:
https://docs.microsoft.com/en-us/azure/active-directory/authentication/howto-mfa-mfasettings
- (Exam Topic 4)
You have a Microsoft 365 tenant.
The Azure Active Directory (Azure AD) tenant syncs to an on-premises Active Directory domain.
Users connect to the internet by using a hardware firewall at your company. The users authenticate to the firewall by using their Active Directory credentials.
You plan to manage access to external applications by using Azure AD.
You need to use the firewall logs to create a list of unmanaged external applications and the users who access them.
What should you use to gather the information?
Correct Answer:
C
Reference:
https://docs.microsoft.com/en-us/cloud-app-security/create-snapshot-cloud-discovery-reports#using-traffic-logs
- (Exam Topic 4)
You have an Azure Active Directory (Azure AD) tenant that syncs to an Active Directory forest. The tenant-uses through authentication.
A corporate security policy states the following: Domain controllers must never communicate directly to the internet.
Domain controllers must never communicate directly to the internet.  Only required software must be- installed on servers.
Only required software must be- installed on servers.
The Active Directory domain contains the on-premises servers shown in the following table.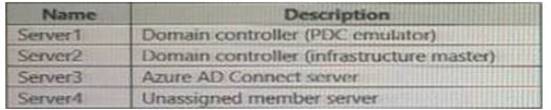
You need to ensure that users can authenticate to Azure AD if a server fails.
On which server should you install an additional pass-through authentication agent?
Correct Answer:
C
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/hybrid/how-to-connect-pta-quick-start
- (Exam Topic 4)
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. as a result, these questions will not appear in the review screen.
You have an Amazon Web Services (AWS) account a Google Workspace subscription, and a GitHub account You deploy an Azure subscription and enable Microsoft 365 Defender.
You need to ensure that you can monitor OAuth authentication requests by using Microsoft Defender for Cloud Apps.
Solution: From the Microsoft 365 Defender portal, you add the GitHub app connector Does this meet the goal?
Correct Answer:
B
- (Exam Topic 4)
You have a Microsoft 365 E5 subscription that uses Microsoft Defender for Cloud Apps.
You need to identify which users access Facebook from their devices and browsers. The solution must minimize administrative effort.
What should you do first?
Correct Answer:
C

