- (Exam Topic 3)
You are planning the security requirements for Azure Cosmos DB Core (SQL) API accounts. You need to recommend a solution to audit all users that access the data in the Azure Cosmos DB accounts. Which two configurations should you include in the recommendation? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
Correct Answer:
BC
https://docs.microsoft.com/en-us/azure/cosmos-db/audit-control-plane-logs
- (Exam Topic 3)
You have a customer that has a Microsoft 365 subscription and uses the Free edition of Azure Active Directory (Azure AD)
The customer plans to obtain an Azure subscription and provision several Azure resources. You need to evaluate the customer's security environment.
What will necessitate an upgrade from the Azure AD Free edition to the Premium edition?
Correct Answer:
D
(https://docs.microsoft.com/en-us/azure/active-directory/privileged-identity-management/pim-configure) https://www.microsoft.com/en-us/security/business/identity-access/azure-active-directory-pricing?rtc=1
- (Exam Topic 3)
Your company is migrating data to Azure. The data contains Personally Identifiable Information (Pll). The
company plans to use Microsoft Information Protection for the Pll data store in Azure. You need to recommend a solution to discover Pll data at risk in the Azure resources.
What should you include in the recommendation? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.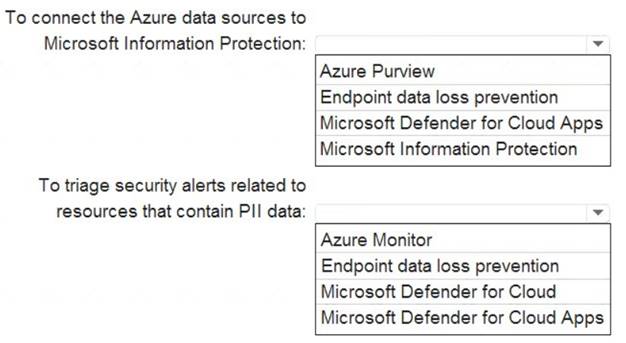
Solution:
Graphical user interface, text, application Description automatically generated
Prioritize security actions by data sensitivity,
https://docs.microsoft.com/en-us/azure/defender-for-cloud/information-protection. As to Azure SQL Database Azure SQL Managed Instance Azure Synapse Analytics (Azure resources as well): https://docs.microsoft.com/en-us/azure/azure-sql/database/data-discovery-and-classification-overview?view=azu
Does this meet the goal?
Correct Answer:
A
- (Exam Topic 3)
You have an Azure subscription.
You have a DNS domain named contoso.com that is hosted by a third-party DNS registrar. Developers use Azure DevOps to deploy web apps to App Service Environments- When a new app is
deployed, a CNAME record for the app is registered in contoso.com.
You need to recommend a solution to secure the DNS record tor each web app. The solution must meet the following requirements:
• Ensure that when an app is deleted, the CNAME record for the app is removed also
• Minimize administrative effort.
What should you include in the recommendation?
Correct Answer:
C
- (Exam Topic 3)
You have the following on-premises servers that run Windows Server:
• Two domain controllers in an Active Directory Domain Services (AD DS) domain
• Two application servers named Server1 and Server2 that run ASP.NET web apps
• A VPN server named Server3 that authenticates by using RADIUS and AD DS End users use a VPN to access the web apps over the internet.
You need to redesign a user access solution to increase the security of the connections to the web apps. The solution must minimize the attack surface and follow the Zero Trust principles of the Microsoft Cybersecurity Reference Architectures (MCRA).
What should you include in the recommendation?
Correct Answer:
C

