Given the following code: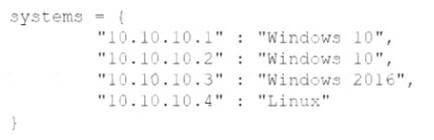
Which of the following data structures is systems?
Correct Answer:
D
A dictionary is a data structure in Python that stores key-value pairs, where each key is associated with a value. A dictionary is created by enclosing the key-value pairs in curly braces and separating them by commas. A dictionary can be accessed by using the keys as indexes or by using methods such as keys(), values(), or items(). In the code, systems is a dictionary that has four key-value pairs, each representing an IP address and its corresponding operating system. A tuple is a data structure in Python that stores an ordered sequence of immutable values, enclosed in parentheses and separated by commas. A tree is a data structure that consists of nodes connected by edges, forming a hierarchical structure with a root node and leaf nodes. An array is a data structure that stores a collection of elements of the same type in a contiguous memory location.
A penetration tester needs to perform a test on a finance system that is PCI DSS v3.2.1 compliant. Which of the following is the MINIMUM frequency to complete the scan of the system?
Correct Answer:
C
Quarterly is the minimum frequency to complete the scan of the system that is PCI DSS v3.2.1 compliant, according to Requirement 11.2.2 of the standard1. PCI DSS (Payment Card Industry Data Security Standard) is a set of security standards that applies to any organization that processes, stores, or transmits credit card information. Requirement 11.2.2 states that organizations must perform internal vulnerability scans at least quarterly and after any significant change in the network.
https://www.pcicomplianceguide.org/faq/#25
PCI DSS requires quarterly vulnerability/penetration tests, not weekly.
Which of the following situations would require a penetration tester to notify the emergency contact for the engagement?
Correct Answer:
D
A penetration tester who is performing a physical assessment of a company’s security practices notices the company does not have any shredders inside the office building. Which of the following techniques would be BEST to use to gain confidential information?
Correct Answer:
B
During an assessment, a penetration tester inspected a log and found a series of thousands of requests coming from a single IP address to the same URL. A few of the requests are listed below.
Which of the following vulnerabilities was the attacker trying to exploit?
Correct Answer:
C
The vulnerability that the attacker was trying to exploit is SQL injection, which is a type of attack that exploits a vulnerability in a web application that allows an attacker to execute malicious SQL statements on a database server. SQL injection can allow an attacker to perform various actions on the database, such as reading, modifying, deleting, or creating data, or executing commands on the underlying OS. The log shows that the attacker was sending thousands of requests to the same URL with different parameters, such as id=1’ OR 1=1;–, id=1’ AND 1=2;–, or id=1’ UNION SELECT * FROM users;–. These parameters are examples of SQL injection payloads, which are crafted SQL statements that are designed to manipulate or bypass the intended SQL query. For example, id=1’ OR 1=1;-- is a payload that terminates the original query with a single quote and a semicolon, appends an OR condition that is always true (1=1), and comments out the rest of the query with two dashes (–). This payload can cause the web application to return all records from the database table instead of just one record with id=1. The other options are not vulnerabilities that match the log entries. Session hijacking is a type of attack that exploits a vulnerability in a web application that allows an attacker to take over an active session of another user by stealing or guessing their session identifier or cookie. URL manipulation is a type of attack that exploits a vulnerability in a web application that allows an attacker to modify parameters or values in the URL to access unauthorized resources or functions. Insecure direct object reference is a type of attack that exploits a vulnerability in a web application that allows an attacker to access objects or resources directly by modifying their identifiers or references in the URL or request.

