A company obtained permission for a vulnerability scan from its cloud service provider and now wants to test the security of its hosted data.
Which of the following should the tester verify FIRST to assess this risk?
Correct Answer:
A
A new security firm is onboarding its first client. The client only allowed testing over the weekend and needed the results Monday morning. However, the assessment team was not able to access the environment as expected until Monday. Which of the following should the security company have acquired BEFORE the start of the assessment?
Correct Answer:
A
According to the CompTIA PenTest+ Study Guide, Exam PT0-0021, a statement of work (SOW) is a document that defines the scope, objectives, deliverables, and terms of a penetration testing project. It is a formal agreement between the service provider and the client that specifies what is expected from both parties, including the timeline, budget, resources, and responsibilities. A SOW is essential for any penetration testing engagement, as it helps to avoid misunderstandings, conflicts, and legal issues.
The CompTIA PenTest+ Study Guide also provides an example of a SOW template that covers the following sections1: Project overview: A brief summary of the project’s purpose, scope, objectives, and deliverables.
Project overview: A brief summary of the project’s purpose, scope, objectives, and deliverables. Project scope: A detailed description of the target system, network, or application that will be tested, including the boundaries, exclusions, and assumptions.
Project scope: A detailed description of the target system, network, or application that will be tested, including the boundaries, exclusions, and assumptions. Project objectives: A clear statement of the expected outcomes and benefits of the project, such as identifying vulnerabilities, improving security posture, or complying with regulations.
Project objectives: A clear statement of the expected outcomes and benefits of the project, such as identifying vulnerabilities, improving security posture, or complying with regulations. Project deliverables: A list of the tangible products or services that will be provided by the service provider to the client, such as reports, recommendations, or remediation plans.
Project deliverables: A list of the tangible products or services that will be provided by the service provider to the client, such as reports, recommendations, or remediation plans. Project timeline: A schedule of the project’s milestones and deadlines, such as kickoff meeting, testing phase, reporting phase, or closure meeting.
Project timeline: A schedule of the project’s milestones and deadlines, such as kickoff meeting, testing phase, reporting phase, or closure meeting. Project budget: A breakdown of the project’s costs and expenses, such as labor hours, travel expenses, tools, or licenses.
Project budget: A breakdown of the project’s costs and expenses, such as labor hours, travel expenses, tools, or licenses. Project resources: A specification of the project’s human and technical resources, such as team members, roles, responsibilities, skills, or equipment.
Project resources: A specification of the project’s human and technical resources, such as team members, roles, responsibilities, skills, or equipment. Project terms and conditions: A statement of the project’s legal and contractual aspects, such as confidentiality, liability, warranty, or dispute resolution.
Project terms and conditions: A statement of the project’s legal and contractual aspects, such as confidentiality, liability, warranty, or dispute resolution.
The CompTIA PenTest+ Study Guide also explains why having a SOW is important before starting an assessment1: It establishes a clear and mutual understanding of the project’s scope and expectations between the service provider and the client.
It establishes a clear and mutual understanding of the project’s scope and expectations between the service provider and the client. It provides a basis for measuring the project’s progress and performance against the agreed-upon objectives and deliverables.
It provides a basis for measuring the project’s progress and performance against the agreed-upon objectives and deliverables. It protects both parties from potential risks or disputes that may arise during or after the project.
It protects both parties from potential risks or disputes that may arise during or after the project.
Which of the following is a regulatory compliance standard that focuses on user privacy by implementing the right to be forgotten?
Correct Answer:
C
GDPR is a regulatory compliance standard that focuses on user privacy by implementing the right to be forgotten. GDPR stands for General Data Protection Regulation, and it is a law that applies to the European Union and the United Kingdom. GDPR gives individuals the right to request their personal data be deleted by data controllers and processors under certain circumstances, such as when the data is no longer necessary, when the consent is withdrawn, or when the data was unlawfully processed. GDPR also imposes other obligations and rights related to data protection, such as data minimization, data portability, data breach notification, and consent management. The other options are not regulatory compliance standards that focus on user privacy by implementing the right to be forgotten. NIST SP 800-53 is a set of security and privacy controls for federal information systems and organizations in the United States. ISO 27001 is an international standard that specifies the requirements for an information security management system.
A company is concerned that its cloud VM is vulnerable to a cyberattack and proprietary data may be stolen. A penetration tester determines a vulnerability does exist and exploits the vulnerability by adding a fake VM instance to the IaaS component of the client's VM. Which of the following cloud attacks did the penetration tester MOST likely implement?
Correct Answer:
C
Malware injection is the most likely cloud attack that the penetration tester implemented, as it involves adding a fake VM instance to the IaaS component of the client’s VM. Malware injection is a type of attack that exploits vulnerabilities in cloud services or applications to inject malicious code or data into them. The injected malware can then compromise or control the cloud resources or data.
A penetration tester was brute forcing an internal web server and ran a command that produced the following output: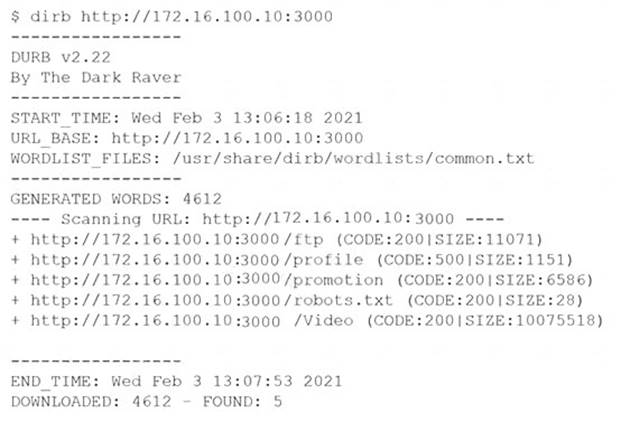
However, when the penetration tester tried to browse the URL http://172.16.100.10:3000/profile, a blank page was displayed.
Which of the following is the MOST likely reason for the lack of output?
Correct Answer:
A

