- (Topic 6)
An organization plans to set up a secure connector for Power Apps. The App will capture tweets from Twitters about the organization’s upcoming product for sales follow-up.
You need to configure security for the app. Which authentication method should you use?
Correct Answer:
A
Configure OAuth2 provider settings for portals.
The OAuth 2.0 based external identity providers involve registering an "application" with a third-party service to obtain a "client ID" and "client secret" pair.
The supported providers are:
✑ Microsoft Account
✑ Twitter
✑ Facebook
✑ Google
✑ LinkedIn
✑ Yahoo
Reference:
https://docs.microsoft.com/en-us/powerapps/maker/portals/configure/configure-oauth2- settings
DRAG DROP - (Topic 3)
You need to assign the minimum environmental security role to the appropriate users.
Which security roles should you use? To answer, drag the appropriate security roles to the correct users. Each security role may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.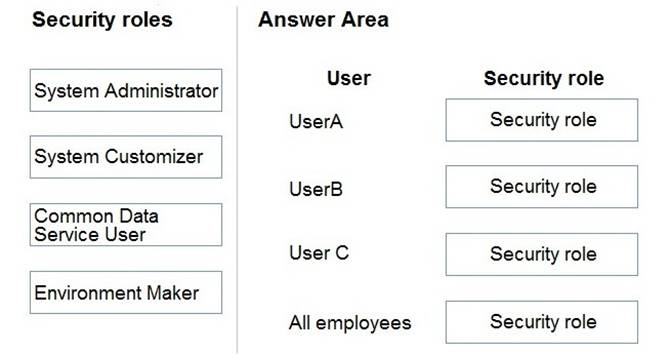
Solution:
Box 1: Environment Maker
UserA must be able to create and publish Power Apps apps.
The Environment Maker role can create resources within an environment including apps, connections, custom connectors, gateways, and flows using Power Automate.
Box 2: System Administrator
UserB must be the owner of all the systems and be able to provide permissions and create all new environments.
The System Administrator has full permission to customize the system. Can view all data in the system.
Box 3: System Customizer
UserC must be able to create apps connected to the systems and update the security roles and entities.
The System Customizer has full permission to customize the system. Can only view rows for system tables that they create.
The difference between the System Administrator and System Customizer security roles is that a system administrator has read privileges on most rows in the system and can see everything. Assign the System Customizer role to someone who needs to perform customization tasks but shouldn’t see any data in the system tables.
Box 4: Common Data Service User
To stay consistent with our product rebranding effort, the security role Common Data Service User is being changed to Basic User.
The Basic User security role primarily contains Basic privileges for core entities where the user can write, update, and delete records that they created or owned.
Does this meet the goal?
Correct Answer:
A
HOTSPOT - (Topic 6)
Fabrikam, Inc, has two divisions as shown in the Business Unit exhibit. (Click the Business Unit tab.)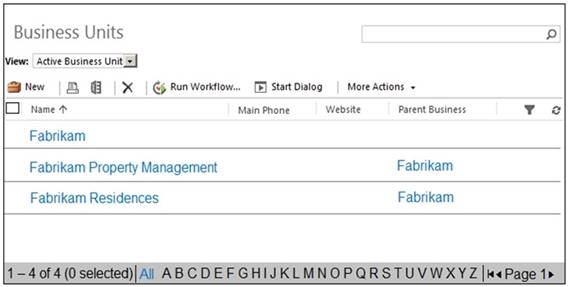
✑ Fabrikam Residences rents units short term to clients.
✑ Fabrikam Property Management deals with the maintenance of the units and manages the contractors who perform the maintenance.
✑ Clients and contractors are both stored in the Contact entity.
The manager of the Property Management business unit is a member of a Fabrikam business unit, which has the root security role as shown in the Security Role exhibit. (Click the Security Role tab.)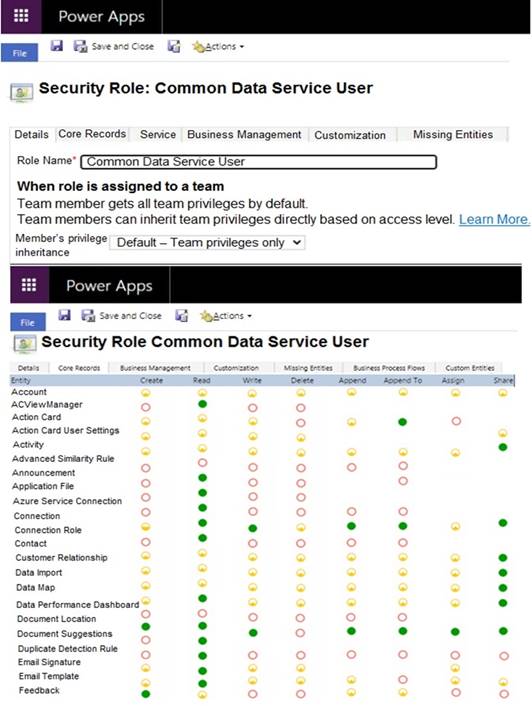
The manager cannot see the contact record shown in the Contact exhibit. (Click the
Contact tab.)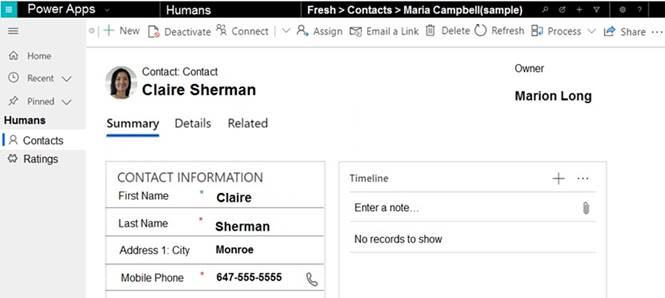
You need to ensure that the manager can view contact records owned by someone in the Residences business unit.
For each of the following statements, select Yes if the statement achieves the goal. Otherwise, select No.
Solution:
Box 1: Yes
Change it to Direct User/Basic access level and Team privileges. This creates a security role with team member's privilege inheritance.
Note: For roles assigned to teams with Basic-level access user privilege, the role's inheritance configuration also comes into play. If the team has the Member's privilege inheritance set to Team privileges only, then the user will only be able make use of that privilege for records owned by the team.¨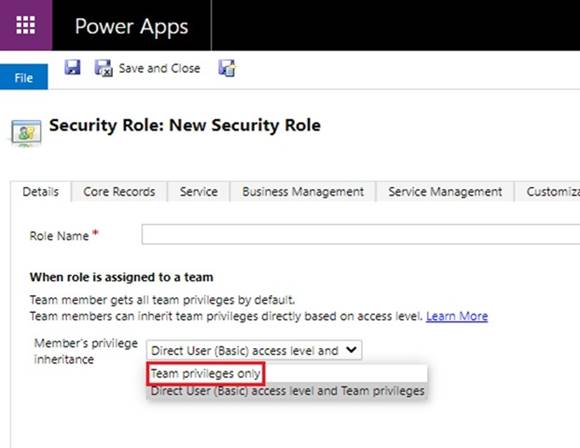
Box 2: No
The manager of the Property Management business unit is already a member of a Fabrikam business unit, which has the root security role
Box 3: Yes
Does this meet the goal?
Correct Answer:
A
HOTSPOT - (Topic 6)
You are creating a model-driven app to track the time that employees spend on individual projects.
You need to configure the app according to the company’s requirements.
Which components should you configure? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.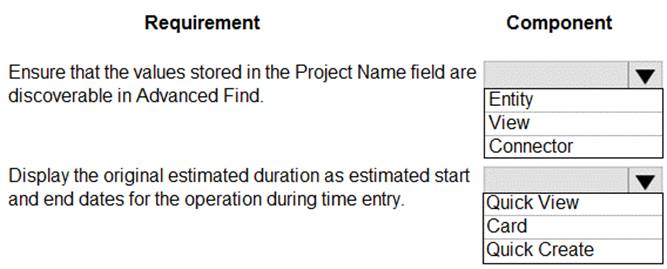
Solution:
Box 1: View
Box 2: Quick Create
With quick create forms, your app can have a streamlined data entry experience with full support for logic defined by form scripts and business rules.
By default only these system tables have quick create forms: account, campaign response, 1case, competitor, contact, lead, opportunity.
Does this meet the goal?
Correct Answer:
A
DRAG DROP - (Topic 6)
You are creating a canvas app for a company. A security role has been created for sales representatives and a second security role has been created for sales managers.
The canvas app has the following requirements:
✑ Sales managers must be able to view the records of the salespeople in their business unit.
✑ Sales managers must be the only people who can view sales probability data in
opportunity records.
✑ Sales representatives and new hires assigned to the same territory share access to sales records.
You need to assign permissions for the app.
Which security options should you use? To answer, drag the appropriate security options to the correct scenarios. Each security option may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
Solution:
Box 1: Role-based security
Dataverse uses role-based security to group together a collection of privileges. These security roles can be associated directly to users, or they can be associated with Dataverse teams and business units.
Box 2: Field-level security
Sometimes record-level control of access is not adequate for some business scenarios. Dataverse has a field-level security feature to allow more granular control of security at the field level. Field-level security can be enabled on all custom fields and most system fields.
Box 3: Record-level security
Does this meet the goal?
Correct Answer:
A

