A project team has just experienced an unexpected event and implemented a work-around. Which of the following documents should be used to record the event? (Select TWO).
Correct Answer:
CE
Issue log and change log are documents that should be used to record the event where the project team has just experienced an unexpected event and implemented a work-around. An issue log is a document that tracks and records any issues or problems that arise during a project and how they are resolved. An issue log can help to monitor and control the project performance and quality and prevent any negative impacts on the project objectives and deliverables. A change log is a document that tracks and records any changes or modifications that are made to the project scope, schedule, cost, quality, or resources during a project. A change log can help to document the change request, approval, implementation, and impact of each change and ensure traceability and transparency.
A project manager is monitoring team performance by comparing committed versus completed work. The project manager creates the following: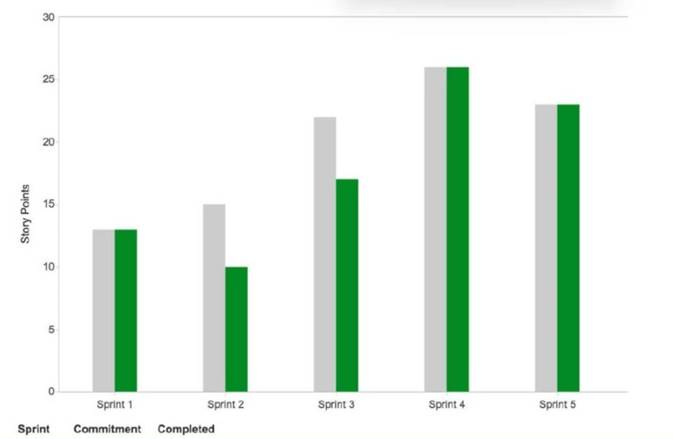

Which of the following most likely represents the number of items in the backlog?
Correct Answer:
A
The number of items in the backlog can be determined by looking at the “Commitment” column for each sprint in the provided chart. For Sprint 5, there is a commitment of completing 23 items, which is the highest among all sprints. This indicates that there are at least 23 items in the backlog to be worked on. This is consistent with the concept of agile project management, which allows for changes and additions to the project scope based on customer feedback and changing requirements. References = CompTIA Project+ PK0-005 Certification Study Guide, Chapter 14: Agile Project Management, page 321. CompTIA Project+ Cert Guide: Exam PK0-004, Chapter 9: Agile Project Management, page 287
Which of the following would be the NEXT document a project manager should update once the need to procure goods and/or services is identified?
Correct Answer:
B
The statement of work (SOW) would be the next document that a project manager should update once the need to procure goods and/or services is identified. A SOW is a document that defines the scope, deliverables, schedule, and terms and conditions of a project or contract. A SOW typically includes information such as purpose, scope of work, location of work, period of performance, deliverables schedule, applicable standards, acceptance criteria, special requirements, and payment schedule. A SOW can help to establish a common understanding and agreement between the client and the service provider on what needs to be done and how it will be done.
A PM is responsible for implementing a new customer relationship management system and has learned that the sales organization is reluctant to utilize the new system. The organization's reluctance could jeopardize the success of the project. Which of the following steps should be taken to understand the adoption issues and gain organizational acceptance of the initiative? (Select TWO).
Correct Answer:
CD
The project manager should hold sessions to understand user challenges and track system usage and report user activity. These steps will help the project manager to identify the root causes of the adoption issues and monitor the progress of the system utilization. They will also help to communicate with the sales organization and provide feedback and support12
Which of the following should be the PRIMARY basis for establishing metrics that measure the effectiveness of an information security program?
Correct Answer:
D
Control objectives are the desired outcomes or goals of implementing security controls to mitigate risks and protect information assets. Control objectives should be the primary basis for establishing metrics that measure the effectiveness of an information security program, as they align with the business objectives, requirements, and expectations of the organization and its stakeholders. Metrics based on control objectives can help to evaluate the performance, efficiency, and maturity of the security program, and to identify gaps, issues, and areas for improvement. The other options are not correct because:
✑ Residual risk is the remaining risk after applying security controls. Residual risk is not a basis for establishing metrics, but rather a result of measuring the effectiveness of security controls. Residual risk should be monitored and reported, but it does not define the desired outcomes or goals of the security program.
✑ Regulatory requirements are the external standards, laws, and regulations that the organization must comply with to avoid legal or financial penalties. Regulatory requirements are not a basis for establishing metrics, but rather a constraint or a driver for the security program. Metrics based on regulatory requirements can help to demonstrate compliance, but they may not reflect the actual effectiveness or efficiency of the security program.
✑ Risk tolerance is the level of risk that the organization is willing to accept or bear.
Risk tolerance is not a basis for establishing metrics, but rather a factor or an input for the security program. Metrics based on risk tolerance can help to prioritize and allocate resources, but they may not measure the actual outcomes or goals of the security program. References = Key Performance Indicators for Security Governance, Part 1; 14 Cybersecurity Metrics + KPIs You Must Track in 2023; KPIs in Information Security: The 10 Most Important Security Metrics; Why metrics are crucial to proving cybersecurity programs’ value; Implementing and Maintaining Security Program Metrics

