The password upload utility must run from the CPM server
Correct Answer:
A
According to the CyberArk documentation1, the Password Upload utility must run from the Central Policy Manager (CPM) server. This utility works by uploading passwords and their properties into the Password Vault from a pre-prepared file, creating the required environment, when necessary. It is run from a command line whenever a password upload is required1.
DRAG DROP
Match each automatic remediation to the correct PTA security event.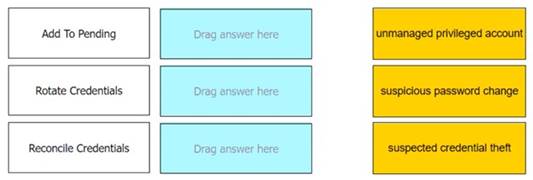
Solution:
In CyberArk’s Privileged Threat Analytics (PTA), automatic remediations are actions that can be configured to respond to specific security events. For the event of an unmanaged privileged account, the remediation “Add To Pending” is used to add the account to the pending accounts queue. When there is a suspected credential theft, “Rotate Credentials” is the remediation that initiates a password change. Lastly, for a suspicious password change event, “Reconcile Credentials” is the remediation that ensures the credentials are correct and valid1.
References:
✑ CyberArk Docs: Configure security events
Does this meet the goal?
Correct Answer:
A
Which usage can be added as a service account platform?
Correct Answer:
B
A service account platform is a type of platform that defines how CyberArk manages passwords for service accounts, which are accounts that run applications or services on remote machines. A usage is a configuration that allows CyberArk to manage passwords for files, such as XML or INI files, that are stored on remote machines. A usage is associated with a parent account, which is the account that has access to the file. A usage can be added as a service account platform if the file contains the password of a service account. For example, IIS Application Pools is a usage that can be added as a service account platform, because it manages the passwords of the application pools that run on IIS servers. The other options, Kerberos Tokens, PowerShell Libraries, and Loosely Connected Devices, are not usages that can be added as service account platforms, because they do not manage passwords for service accounts. References: Usages, Service Account Platforms
You are onboarding an account that is not supported out of the box. What should you do first to obtain a platform to import?
Correct Answer:
D
The CyberArk marketplace is a platform that simplifies delivery of privileged access security solutions, such as CyberArk Privileged Account Security Solution. It features the industry’s broadest and deepest portfolio of technology integrations, including platforms for various types of accounts. Customers can find and deploy integrations with CyberArk Marketplace in as little as four clicks. If there is no platform that meets the customer’s needs, they can request a custom platform from CyberArk or create their own using the Platform Development Kit (PDK). References: CyberArk Marketplace, Platform Development Kit
When running a “Privileged Accounts Inventory” Report through the Reports page in PVWA on a specific safe, which permission/s are required on that safe to show complete account inventory information?
Correct Answer:
A
The Privileged Accounts Inventory Report provides information about all the privileged accounts in the system, based on different filters, such as safe, platform, policy, and owner. To run this report through the Reports page in PVWA on a specific safe, the user needs to have the following permissions on that safe:
✑ List Accounts: This permission allows the user to view the accounts in the safe and their properties, such as name, address, platform, and policy.
✑ View Safe Members: This permission allows the user to view the members of the safe and their authorizations, such as owners, users, and groups.
These permissions are required to show complete account inventory information for the specific safe. Other permissions, such as Manage Safe Owners, Access Safe without confirmation, Manage Safe, and View Audit, are not relevant for this report. References: Reports and Audits - CyberArk, Safe Member Authorizations

