Refer to the exhibit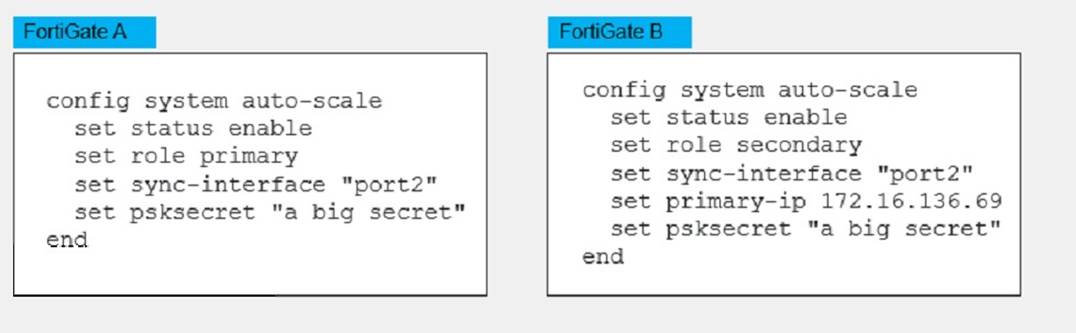
An administrator deployed an HA active-active load balance sandwich in Microsoft Azure. The setup requires configuration synchronization between devices-
What are two outcomes from the configured settings? (Choose two.)
Correct Answer:
BD
* B. FortiGate A and FortiGate B are two independent devices. This means that they are not part of a cluster or a high availability group, and they do not share the same configuration or state information. They are configured as standalone FortiGates with standalone configuration synchronization enabled1. This feature allows them to synchronize most of their configuration settings with each other, except for some settings that identify the FortiGate to the network, such as the hostname1. D. It does not synchronize the FortiGate hostname. This is one of the settings that are excluded from the standalone configuration synchronization, as mentioned above. The hostname is a unique identifier for each FortiGate device, and it should not be changed by the synchronization process1.
The other options are incorrect because:
✑ FortiGate-VM instances are not scaled out automatically according to predefined workload levels. This is a feature of the auto scaling solution for FortiGate-VM on Azure, which requires a different deployment and configuration than the one shown in the exhibit2. The exhibit shows a static deployment of two FortiGate-VM instances behind an Azure load balancer, which does not support auto scaling.
✑ By default, FortiGate does not use FGCP. FGCP stands for FortiGate Clustering Protocol, which is used to synchronize configuration and state information between FortiGate devices in a cluster or a high availability group3. However, the exhibit shows that the FortiGates are not in a cluster or a high availability group, and they use standalone configuration synchronization instead of FGCP.
You must allow an SSH traffic rule in an Amazon Web Services (AWS) network access list (NACL) to allow SSH traffic to travel to a subnet for temporary testing purposes. When you review the current inbound network ACL rules, you notice that rule number 5 demes SSH and telnet traffic to the subnet
What can you do to allow SSH traffic?
Correct Answer:
B
Network ACLs are stateless, and they evaluate each packet separately based on the rules that you define. The rules are processed in order, starting with the lowest numbered rule1. If the traffic matches a rule, the rule is applied and no further rules are evaluated1. Therefore, if you want to allow SSH traffic to a subnet, you must create a new allow SSH rule above rule number 5, which denies SSH and telnet traffic. Otherwise, the deny rule will take precedence and block the SSH traffic.
The other options are incorrect because:
✑ Creating a new allow SSH rule below rule number 5 will not allow SSH traffic, because the deny rule will be evaluated first and block the traffic.
✑ Creating a new allow SSH rule anywhere in the network ACL rule base will not guarantee that SSH traffic will be allowed, because it depends on the order of the rules. If the allow SSH rule is below the deny rule, it will not be effective.
✑ You cannot rely on the default security group rule to allow SSH traffic to the subnet, because network ACLs act as an additional layer of security for your VPC. Even if your security group allows SSH traffic, your network ACL must also allow it. Otherwise, the traffic will be blocked at the subnet level.
Refer to the exhibit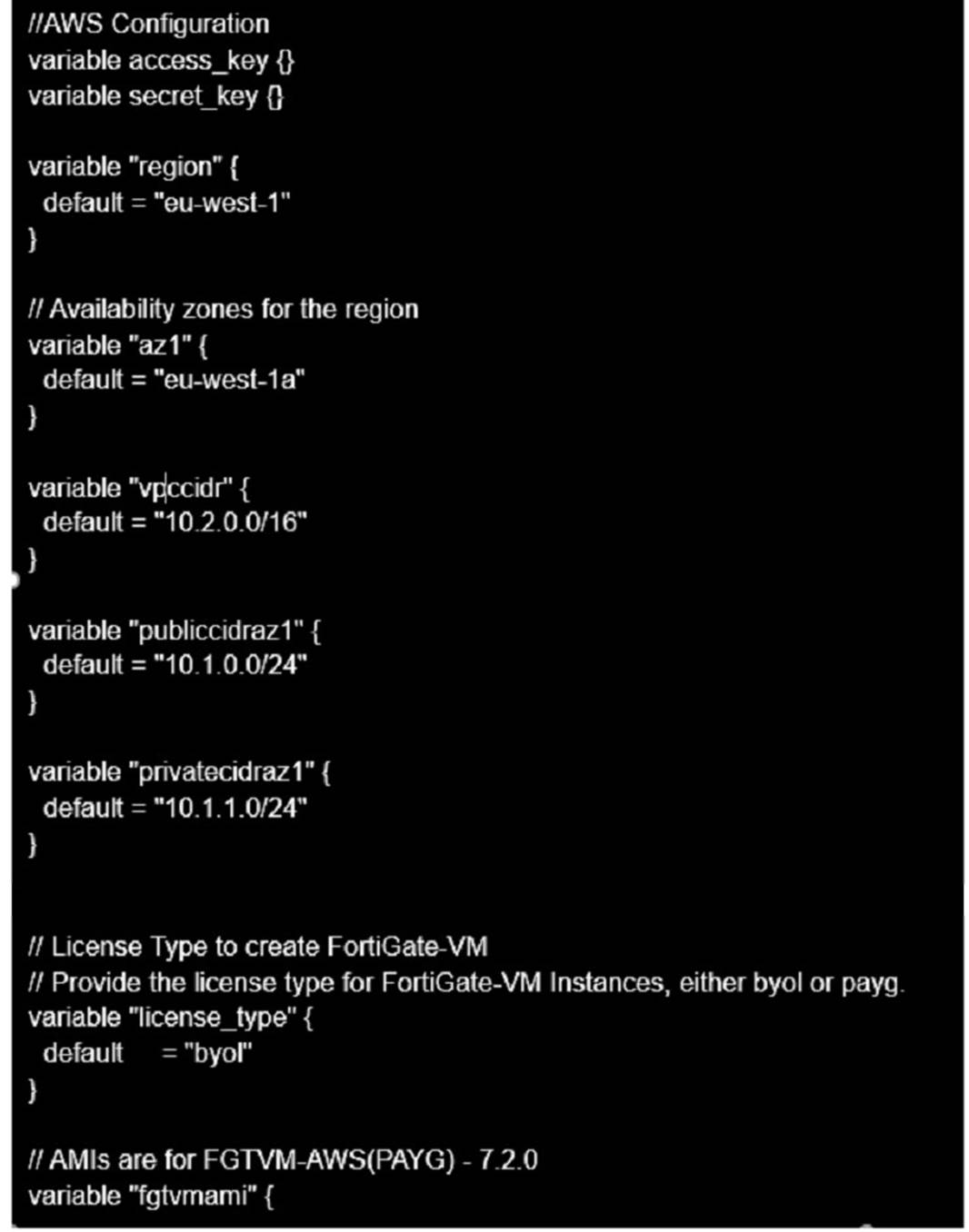
You are tasked to deploy a FortiGate VM with private and public subnets in Amazon Web Services (AWS).
You examined the variables.tf file.
What will be the final result after running the terraform init and terraform apply commands?
Correct Answer:
B
The variables.tf file shows that the FortiGate VM will be deployed in the eu-West-Ia region with private and public subnets. The region variable is set to ??eu-west-1?? and the availability_zone variable is set to ??eu-west-1a??. The vpc_id variable is set to ??vpc- 0e9d6a6f?? and the subnets variable is set to a list of two subnet IDs: ??subnet-0f9d6a6f?? and ??subnet-1f9d6a6f??. The license_type variable is set to ??on-demand?? and the ami_id variable is set to ??ami-0e9d6a6f??.
References: https://docs.fortinet.com/document/fortigate/6.4.0/aws- cookbook/236478/deploying-fortigate-vm-on-aws-using-terraform
You are troubleshooting an Azure SDN connectivity issue with your FortiGate VM
Which two queries does that SDN connector use to interact with the Azure management API? (Choose two.)
Correct Answer:
AD
The Azure SDN connector uses two types of queries to interact with the Azure management API. The first query is targeted to a special IP address to get a token. This token is used to authenticate the subsequent queries. The second type of query is used to retrieve information about the Azure resources, such as virtual machines, network interfaces, network security groups, and public IP addresses. Some queries are made to manage public IP addresses, such as assigning or releasing them from the FortiGate VM. References: Configuring an SDN connector in Azure, Azure SDN connector using service principal, Troubleshooting Azure SDN connector
Refer to the exhibit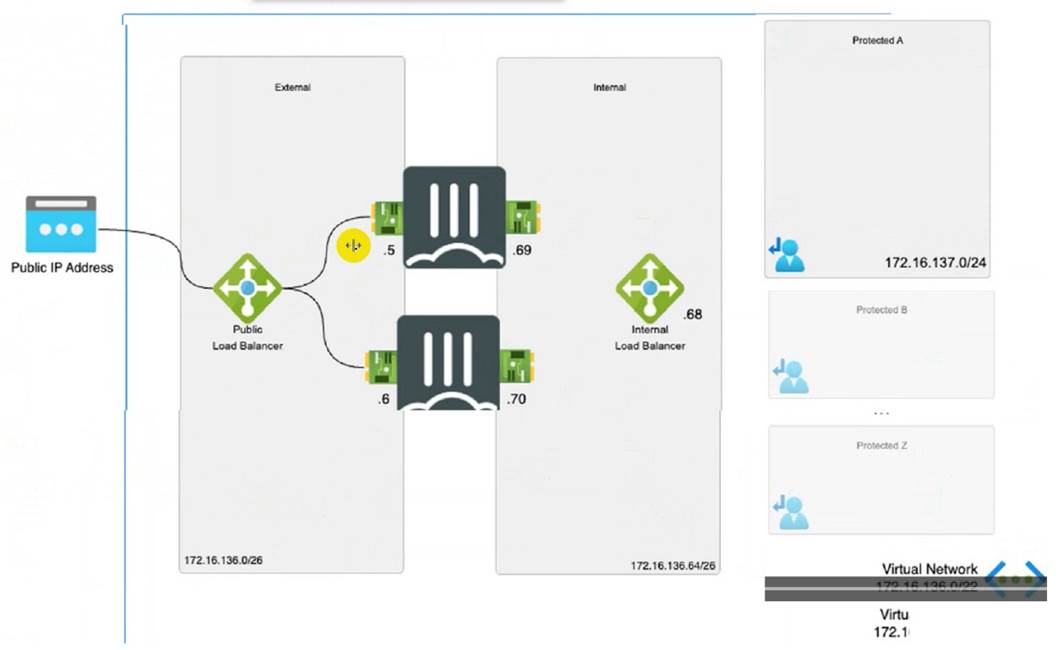
Consider the active-active load balance sandwich scenario in Microsoft Azure.
What are two important facts in the active-active load balance sandwich scenario? (Choose two )
Correct Answer:
BD
* B. It is recommended to enable NAT on FortiGate policies. This is because the Azure load balancer uses a hash-based algorithm to distribute traffic to the FortiGate instances, and it relies on the source and destination IP addresses and ports of the packets1. If NAT is not enabled, the source IP address of the packets will be the same as the load balancer??s frontend IP address, which will result in uneven distribution of traffic and possible asymmetric routing issues1. Therefore, it is recommended to enable NAT on the FortiGate policies to preserve the original source IP address of the packets and ensure optimal load balancing and routing1. D. It supports session synchronization for handling asynchronous traffic. This means that the FortiGate instances can synchronize their session tables with each other, so that they can handle traffic that does not follow the same path as the initial packet of a session2. For example, if a TCP SYN packet is sent to FortiGate A, but the TCP SYN-ACK packet is sent to FortiGate B, FortiGate B can forward the packet to FortiGate A by looking up the session table2. This feature allows the FortiGate instances to handle asymmetric traffic that may occur due to the Azure load balancer??s hash-based algorithm or other factors.
The other options are incorrect because:
✑ It does not use the vdom-exception command to exclude the configuration from being synced. The vdom-exception command is used to exclude certain configuration settings from being synchronized between FortiGate devices in a cluster or a high availability group3. However, in this scenario, the FortiGate devices are not in a cluster or a high availability group, but they are standalone devices with standalone configuration synchronization enabled. This feature allows them to synchronize most of their configuration settings with each other, except for some settings that identify the FortiGate to the network, such as the hostname.
✑ It does not use the FGCP protocol. FGCP stands for FortiGate Clustering Protocol, which is used to synchronize configuration and state information between FortiGate devices in a cluster or a high availability group. However, in this scenario, the FortiGate devices are not in a cluster or a high availability group, and they use standalone configuration synchronization instead of FGCP.

