Refer to the exhibit.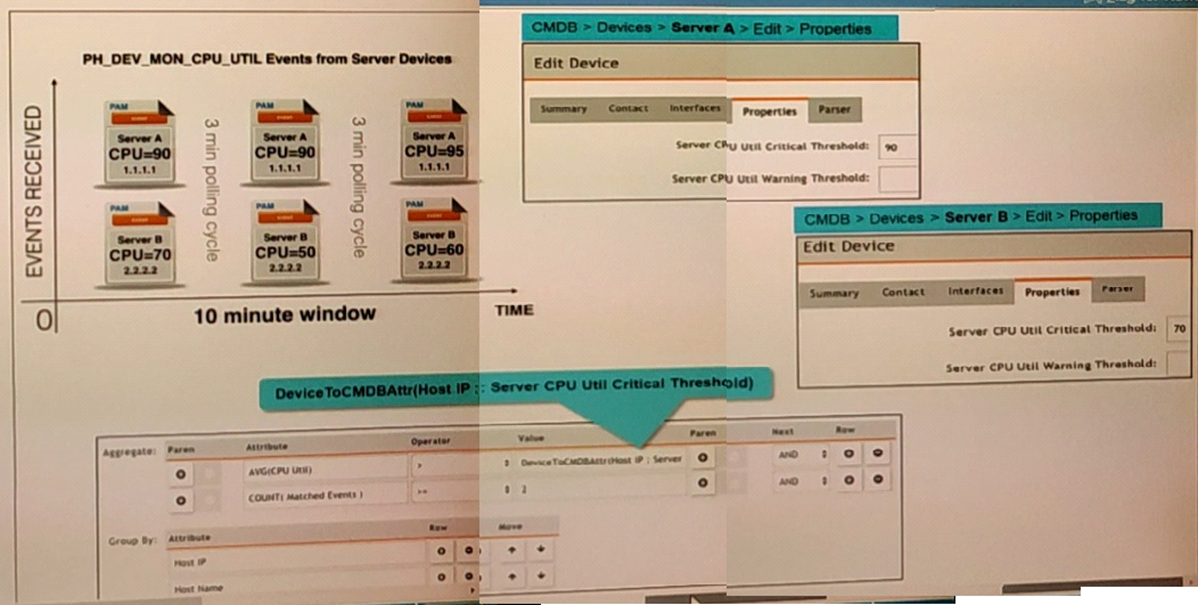
Three events are collected over a 10-minutc time period from two servers Server A and Server B. Based on the settings being used for the rule subpattern. how many incidents will the servers generate?
Correct Answer:
A
What is a prerequisite for FortiSIEM Linux agent installation?
Correct Answer:
B
Explanation
FortiSIEM Linux Agent: The FortiSIEM Linux agent is used to collect logs and performance metrics from Linux servers and send them to the FortiSIEM system.
Prerequisite for Installation: Theauditdservice, which is the Linux Audit Daemon, must be installed and running on the Linux server to capture and log security-related events. auditd Service: This service collects and logs security events on Linux systems, which are essential for monitoring and analysis by FortiSIEM.
auditd Service: This service collects and logs security events on Linux systems, which are essential for monitoring and analysis by FortiSIEM.
Importance of auditd: Without the auditd service, the FortiSIEM Linux agent will not be able to collect the necessary event data from the Linux server.
References: FortiSIEM 6.3 User Guide, Linux Agent Installation section, which lists the prerequisites and steps for installing the FortiSIEM Linux agent.
If an incident??s status is Cleared, what does this mean?
Correct Answer:
B
To determine whether or not syslog is being received from a network device, which is the best command from the backend?
Correct Answer:
A
In the advanced analytical rules engine in FortiSIEM, multiple subpatterms can be referenced using which three operation?(Choose three.)
Correct Answer:
CDE
Advanced Analytical Rules Engine: FortiSIEM's rules engine allows for complex event correlation using multiple subpatterns.
Operations for Referencing Subpatterns:
FOLLOWED_BY: This operation is used to indicate that one event follows another within a specified time window.
OR: This logical operation allows for the inclusion of multiple subpatterns, where the rule triggers if any of the subpatterns match.
AND: This logical operation requires all referenced subpatterns to match for the rule to trigger.
Usage: These operations allow for detailed and precise event correlation, helping to detect complex patterns and incidents.
References: FortiSIEM 6.3 User Guide, Advanced Analytics Rules Engine section, which explains the use of different operations to reference subpatterns in rules.

