- (Topic 3)
Which of the following best describes the purpose of an access control vestibule?
Correct Answer:
B
An access control vestibule, also known as a mantrap, is a physical security access control system that consists of a small space with two sets of interlocking doors. The first set of doors must close before the second set opens, preventing unauthorized individuals from following authorized individuals into facilities with controlled access. This activity, also known as tailgating, results in unauthorized access to the facility. An access control vestibule can help deter and detect tailgating attempts, as well as provide a containment area while authorization for physical access is verified.
References
Access Control Vestibules: Types and Peculiarities Mantrap (access control)
PE-3 (8): Access Control Vestibules
- (Topic 1)
A technician is installing a new fiber connection to a network device in a datacenter. The connection from the device to the switch also traverses a patch panel connection. The chain of connections is in the following order:
Device
LC/LC patch cable
Patch panel
Cross-connect fiber cable Patch panel
LC/LC patch cable Switch
The connection is not working. The technician has changed both patch cables with known working patch cables. The device had been tested and was working properly before being installed. Which of the following is the MOST likely cause of the issue?
Correct Answer:
A
The most likely cause of the issue where the fiber connection from a device to a switch is not working is that the TX/RX (transmit/receive) is reversed. When connecting fiber optic cables, it is important to ensure that the TX of one device is connected to the RX of the other device and vice versa. If the TX/RX is reversed, data cannot be transmitted successfully.
References:
✑ CompTIA Network+ Certification Study Guide, Exam N10-007, Fourth Edition, Chapter 5: Network Operations, Objective 5.1: Given a scenario, use appropriate documentation and diagrams to manage the network.
- (Topic 3)
A malicious user is using special software 10 perform an on-path attack. Which of the following best practices should be configured to mitigate this threat?
Correct Answer:
A
- (Topic 3)
A network technician receives a support ticket concerning multiple users who are unable access the company's shared drive. The switch interface that the shared drive Is connected to is displaying die following: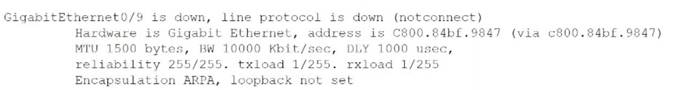
Which of the following is MOST likely the Issue?
Correct Answer:
A
The switchport is shut down, which means it is administratively disabled and cannot forward traffic. The image shows that the switchport status is “down” and the protocol status is “down”, indicating that there is no physical or logical connection. The cable is plugged in, as shown by the “connected” message under the interface name. The loopback is not set, as shown by the “loopback not set” message under the encapsulation type. The bandwidth configuration is correct, as shown by the “BW 10000 Kbit/sec” message under the MTU size. References: [CompTIA Network+ Certification Exam Objectives], Domain 3.0 Infrastructure, Objective 3.1: Given a scenario, use appropriate networking tools, Subobjective: Command line tools (ping, netstat, tracert, etc.)
- (Topic 3)
Which of the following network types is composed of computers that can all communicate with one another with equal permissions and allows users to directly share what is on or
attached to their computers?
Correct Answer:
B
A peer-to-peer network is a type of network in which each computer (or node) can communicate directly with any other node, without requiring a central server or authority. Each node can act as both a client and a server, and can share its own resources, such as files, printers, or internet connection, with other nodes. A peer-to-peer network allows users to directly access and exchange what is on or attached to their computers, with equal permissions and responsibilities

