- (Topic 3)
A network administrator needs to create an SVI on a Layer 3-capable device to separate voice and data traffic. Which of the following best explains this use case?
Correct Answer:
C
An SVI, or switched virtual interface, is a logical interface that is created on a Layer 3- capable device, such as a multilayer switch or a router. An SVI is associated with a VLAN and can be used to route traffic between different VLANs on the same device or across multiple devices. An SVI can also provide management access, security features, and quality of service (QoS) for the VLAN. An SVI is different from a physical interface, which is a port that connects to a physical device or network. A physical interface can be used for trunking, which is a method of carrying multiple VLANs over a single link, or for connecting to a single VLAN. An SVI is also different from a subinterface, which is a logical division of a physical interface that can be assigned to different VLANs.
References:
✑ VLANs and Trunking – N10-008 CompTIA Network+ : 2.11
✑ Switched Virtual Interfaces – N10-008 CompTIA Network+ : 2.22
- (Topic 3)
A systems operator is granted access to a monitoring application, configuration application,
and timekeeping application. The operator is denied access to the financial and project management applications by the system's security configuration. Which of the following BEST describes the security principle in use?
Correct Answer:
D
- (Topic 3)
A network technician is troubleshooting internet connectivity issues with users in a subnet. From a host, the technician runs and then attempts to navigate to a website using a web browser.
The technician receives the following output: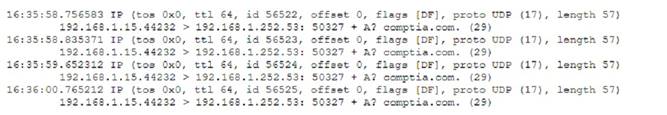
Afterward, the browser displays an error. Which of the following explains this issue?
Correct Answer:
B
The issue is that the host is configured with incorrect DNS settings. DNS (Domain Name System) is a service that resolves domain names to IP addresses. For example, the domain name www.comptia.org is resolved to the IP address 104.18.25.140 by a DNS
server. If the host has incorrect DNS settings, such as an invalid or unreachable DNS server address, it will not be able to resolve domain names to IP addresses, and therefore it will not be able to access websites by their names. The output in the image shows that the host can ping the IP address of www.comptia.org, but it cannot ping the domain name itself, indicating a DNS problem. References: CompTIA Network+ N10-008 Certification Study Guide, page 154; The Official CompTIA Network+ Student Guide (Exam N10-008), page 6-8.
- (Topic 3)
Which of the following describes when an active exploit is used to gain access to a network?
Correct Answer:
A
Penetration testing is a type of security testing that is used to assess the security of a system or network by actively exploiting known vulnerabilities. It is used to simulate an attack on the system and identify any weaknesses that may be exploited by malicious actors. As stated in the CompTIA Security+ Study Guide, "penetration testing is a type of security assessment that attempts to gain unauthorized access to networks and systems by exploiting security vulnerabilities."
- (Topic 3)
A company needs a redundant link to provide a channel to the management network in an incident response scenario. Which of the following remote access methods provides the BEST solution?
Correct Answer:
A
Out-of-band access is a remote access method that provides a separate, independent channel for accessing network devices and systems. Out-of-band access uses a dedicated network connection or a separate communication channel, such as a dial- up or cellular connection, to provide access to network devices and systems. This allows an administrator to access the management network even if the primary network connection is unavailable or impaired. Out-of-band access is a good solution for providing a redundant link to the management network in an incident response scenario because it can be used to access the network even if the primary connection is unavailable or impaired.

