- (Topic 3)
After installing a series of Cat 8 keystones, a data center architect notices higher than normal interference during tests. Which of the following steps should the architect
take to troubleshoot the issue?
Correct Answer:
A
Cat 8 keystones are shielded to prevent interference from external sources, but they also require proper grounding to avoid interference from within the cable. Wrapping the end connections with copper tape before terminating them is one way to ensure a good ground connection and reduce interference. Using passthrough modular crimping plugs, connecting the RX/TX wires to different pins, or running a speed test on a slow device are not relevant or effective steps to troubleshoot the issue.
References:
✑ CompTIA Network+ N10-008 Certification Study Guide, page 191
✑ CompTIA Network+ N10-008 Cert Guide, Deluxe Edition, page 362
✑ CAT8 RJ45 Keystone Problem : r/HomeNetworking2
✑ How to Terminate Cat8 Shielded Keystone Jacks3
- (Topic 3)
Which of the following options represents the participating computers in a network?
Correct Answer:
A
- (Topic 3)
Which of the following authentication protocols should be used when securing a basic wireless network? (Select two).
Correct Answer:
AF
WPA2 and EAP are two authentication protocols that can be used to secure a basic wireless network. WPA2 stands for Wi-Fi Protected Access 2 and it is a security standard that provides strong encryption and authentication for wireless networks. WPA2 supports two modes: personal and enterprise. In personal mode, WPA2 uses a pre-shared key (PSK) that is shared among all wireless devices. In enterprise mode, WPA2 uses an authentication server, such as a RADIUS server, to verify the identity of each wireless device. EAP stands for Extensible Authentication Protocol and it is a framework that allows different methods of authentication to be used over wireless networks. EAP works with WPA2 enterprise mode to provide more flexibility and security for wireless authentication. EAP supports various methods, such as EAP-TLS, EAP-FAST, PEAP, and LEAP, that use certificates, passwords, or tokens to authenticate wireless devices.
- (Topic 3)
While setting up a new workstation, a technician discovers that the network connection is only 100 full duplex (FD), although it is connected to a gigabit switch.
While reviewing the interface information in the switch CLI, the technician notes the port is operating at IOOFD but Shows many RX and TX errors. The technician moves the computer to another switchport and experiences the same issues.
Which of the following is MOST likely the cause of the low data rate and port errors?
Correct Answer:
B
- (Topic 1)
The following configuration is applied to a DHCP server connected to a VPN concentrator: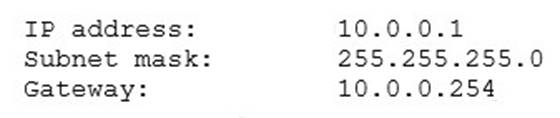
There are 300 non-concurrent sales representatives who log in for one hour a day to upload reports, and 252 of these representatives are able to connect to the VPN without any Issues. The remaining sales representatives cannot connect to the VPN over the course of the day. Which of the following can be done to resolve the issue without utilizing additional resources?
Correct Answer:
A
Decreasing the lease duration on the DHCP server will cause clients to renew their IP address leases more frequently, freeing up IP addresses for other clients to use. References: CompTIA Network+ Certification Study Guide, Chapter 3: IP Addressing.

