Based on the given topology, what is the requirement on an Aruba switch to enable LLDP messages to be received by Switch 1 port 1/1/24. when Router 1 is enabled with LLDP?
Correct Answer:
C
LLDP Link Layer Discovery Protocol. LLDP is a vendor-neutral link layer protocol used by network devices for advertising their identity, capabilities, and neighbors on a local area network. is enabled by default on Aruba switches, but it can be disabled on a per-port basis using the no lldp command. To enable LLDP messages to be received by Switch 1 port 1/1/24, you need to enter the interface configuration mode for that port and use the lldp receive command. References:https://www.arubanetworks.com/techdocs/ArubaOS_86_Web_Help/Content/ar ubaos-solutions/lldp/lldp.htm
You are configuring a network with a stacked pair of 6300M switches used for distribution and layer 3 services. You create a new VLAN for users that will be used on multiple access stacks of CX6200 switches connected downstream of the distribution stack You will be creating multiple VLANs/subnets similar to this will be utilized in multiple access stacks
What is the correct way to configure the routable interface for the subnet to be associated with this VLAN?
Correct Answer:
D
The correct way to configure the routable interface for the subnet to be associated with this VLAN is to create an SVI Switched Virtual Interface (SVI) Switched Virtual Interface (SVI) is a virtual interface on a switch that represents a VLAN and provides Layer 3 routing functions for that VLAN . SVIs are used to enable inter-VLAN routing , provide gateway addresses for hosts in VLANs , apply ACLs or QoS policies to VLANs , etc. SVIs have some advantages over physical routed interfaces such as saving interface ports , reducing cable costs , simplifying network design , etc . SVIs are usually numbered according to their VLAN IDs (e.g., vlan 10) and assigned IP addresses within the subnet of their VLANs . SVIs can be created and configured by using commands such as interface vlan , ip address , no shutdown , etc . SVIs can be verified by using commands such as show ip interface brief , show vlan , show ip route , etc . in the subnet on the 6300M stack. An SVI is a virtual interface on a switch that represents a VLAN and provides Layer 3 routing functions for that VLAN. Creating an SVI in the subnet on the 6300M stack allows the switch to act as a gateway for the users in that VLAN and enable inter-VLAN routing between different subnets. Creating an SVI in the subnet on the 6300M stack also simplifies network design and management by reducing the number of physical interfaces and cables required for routing.
The other options are not correct ways to configure the routable interface for the subnet to be associated with this VLAN because:
✑ Create a physically routed interface in the subnet on the 6300M stack for each
downstream switch: This option is incorrect because creating a physically routedinterface in the subnet on the 6300M stack for each downstream switch would require using one physical port and cable per downstream switch, which would consume interface resources and increase cable costs. Creating a physically routed interface in the subnet on the 6300M stack for each downstream switch would also complicate network design and management by requiring separate routing configurations and policies for each interface.
✑ Create an SVl in the subnet on each downstream switch: This option is incorrect
because creating an SVI in the subnet on each downstream switch would not enable inter-VLAN routing between different subnets, as each downstream switch would act as a gateway for its own VLAN only. Creating an SVI in the subnet on each downstream switch would also create duplicate IP addresses in the same subnet, which would cause IP conflicts and routing errors.
✑ Create an SVl in the subnet on the 6300M stack, and assign the management
address of each downstream switch stack to a different IP address in the same subnet: This option is incorrect because creating an SVI in the subnet on the
6300M stack, and assigning the management address of each downstream switch stack to a different IP address in the same subnet would not enable inter-VLAN routing between different subnets, as each downstream switch would still act as a gateway for its own VLAN only. Creating an SVI in the subnet on the 6300M stack, and assigning the management address of each downstream switch stack to a different IP address in the same subnet would also create unnecessary IP addresses in the same subnet, which would waste IP space and complicate network management.
References: https://www.arubanetworks.com/techdocs/AOS-CX/10.05/HTML/5200- 7295/index.html https://www.arubanetworks.com/techdocs/AOS-CX/10.05/HTML/5200-7295/cx-noscg/l3-routing/l3-routing-overview.htm https://www.arubanetworks.com/techdocs/AOS-CX/10.05/HTML/5200-7295/cx-noscg/l3-routing/l3-routing-config.htm
DRAG DROP
What is the correct order of the TCP 3-Way Handshake sequence?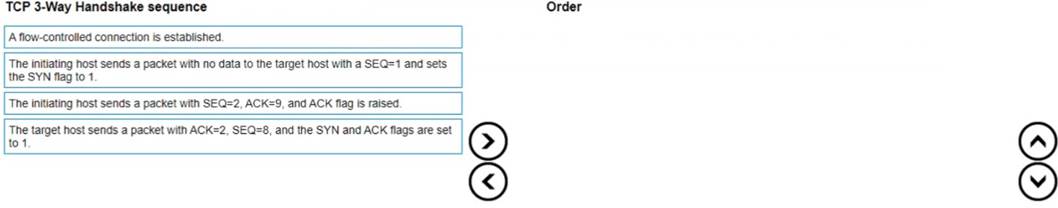
Solution:
TCP 3-Way Handshake sequence is:
✑ Step 1: The initiating host sends a packet with no data to the target host with a SEQ=1 and sets the SYN flag to 1.
✑ Step 2: The target host responds with a packet with ACK=2, SEQ=8, and the SYN and ACK flags set to 1.
✑ Step 3: The initiating host sends a packet with SEQ=2, ACK=9, and the ACK flag set to 1.
✑ Step 4: A normal-controlled connection is established. References: https://en.wikipedia.org/wiki/Transmission_Control_Protocol
https://www.cisco.com/c/en/us/support/docs/ip/routing-information-protocol-rip/13788- 3.html
Does this meet the goal?
Correct Answer:
A
You need to configure wireless access for several classes of loT devices, some of which operate only with 802 11b. Each class must have a unique PSK and will require a different security policy applied as a role There will be 15-20 different classes of devices and performance should be optimized
Which option fulfills these requirements''
Correct Answer:
D
The option that fulfills the requirements is to create individual SSIDs with unique PSK for each loT class, using 2.4 GHz and 5 GHz band. This option provides the following benefits:
✑ Each loT class has a unique PSK that can be used to apply a different security
policy as a role. This enhances the security and flexibility of the WLAN network.
✑ Individual SSIDs allow for better isolation and management of different loT classes. This improves the performance and scalability of the WLAN network.
✑ Using both 2.4 GHz and 5 GHz bands allows for backward compatibility with loT devices that operate only with 802.11b, which uses the 2.4 GHz band1. It also allows for higher throughput and less interference for loT devices that support 802.11a, 802.11g, 802.11n, or 802.11ac, which use the 5 GHz band2.
The other options do not fulfill the requirements because:
✑ Single SSID with MPSK for each loT class using 5 GHz and 6 GHz bands: This option does not support loT devices that operate only with 802.11b, which uses the 2.4 GHz band1. It also does not optimize the performance of the WLAN network, as a single SSID may cause co-channel interference and congestion among different loT classes.
✑ Single SSID with MPSK for each loT class using 2.4 GHz and 5 GHz bands: This option does not optimize the performance of the WLAN network, as a single SSID may cause co-channel interference and congestion among different loT classes.
✑ Individual SSIDs with unique PSK for each loT class, using 5 GHz and 6 GHz bands: This option does not support loT devices that operate only with 802.11b, which uses the 2.4 GHz band1.
References: 1 https://en.wikipedia.org/wiki/IEEE_802.11b-19992 https://www.lifewire.com/wireless-standards-802-11a-802-11b-g-n-and-802-11ac-816553
DRAG DROP
Match each AAA service with its correct definition (Matches may be used more than once or not at all)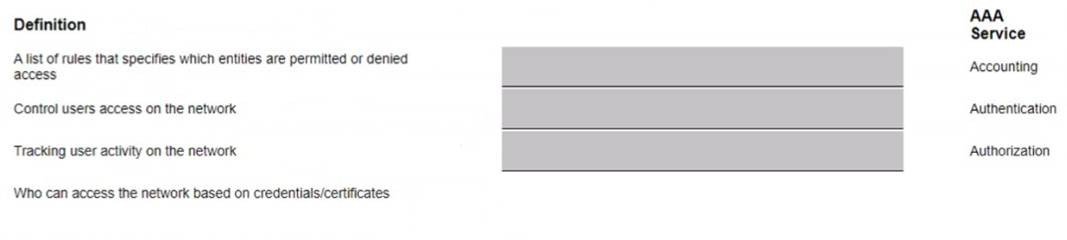
Solution:
AAA Authentication, Authorization, and Accounting (AAA) Authentication, Authorization, and Accounting (AAA) is a framework that provides security services for network access control . AAA consists of three components:
✑ Authentication: The process of verifying the identity of a user or device that wants
to access the network based on credentials such as username and password , certificates , tokens , etc . Authentication can use different protocols such as PAP , CHAP , EAP , RADIUS , TACACS+ , etc .
✑ Authorization: The process of granting or denying access to network resources
based on the identity and privileges of a user or device . Authorization can use different methods such as ACLs , RBAC , MAC , DAC , etc .
✑ Accounting: The process of recording and reporting the activities and usage of
network resources by users or devices . Accounting can use different formats such as syslog , SNMP , NetFlow , etc .service. Here is my Answer:
The correct match for each AAA service with its definition is:
✑ Accounting: C. Tracking user activity on the network
✑ Authentication: D. Who can access the network based on credentials/certificates
✑ Authorization: B. Control users access on the network The other options are not correct matches because:
✑ A list of rules that specifies which entities are permitted or denied access: This option is a definition of an access control list (ACL) Access Control List (ACL) Access Control List (ACL) is a list of rules that specifies which entities are
permitted or denied access to a network resource such as a router , switch , firewall , server , etc . ACLs can be based on different criteria such as source and destination IP addresses , port numbers , protocol types , time of day , etc . ACLs can be applied to different interfaces or directions such as inbound or outbound . ACLs can be verified by using commands such as show access-lists , show ip access-lists , debug ip packet , etc . , not an AAA service.
✑ Who can access the network based on credentials/certificates: This option is a
definition of authentication, not authorization. Authorization is the process of granting or denying access to network resources based on the identity and privileges of a user or device, not based on credentials/certificates.
References: https://en.wikipedia.org/wiki/AAA_(computer_security) https://www.cisco.com/c/en/us/support/docs/security-vpn/remote-authentication-dial-user- service-radius/13838-10.html
Does this meet the goal?
Correct Answer:
A

