Which role does FortiSASE play in supporting zero trust network access (ZTNA) principles9
Correct Answer:
C
FortiSASE supports zero trust network access (ZTNA) principles by identifying attributes on the endpoint for security posture checks. ZTNA principles require continuous verification of user and device credentials, as well as their security posture, before granting access to network resources.
✑ Security Posture Check:
✑ Zero Trust Network Access (ZTNA):
References:
✑ FortiOS 7.2 Administration Guide: Provides information on ZTNA and endpoint security posture checks.
✑ FortiSASE 23.2 Documentation: Details on how FortiSASE implements ZTNA
principles.
A FortiSASE administrator is configuring a Secure Private Access (SPA) solution to share endpoint information with a corporate FortiGate.
Which three configuration actions will achieve this solution? (Choose three.)
Correct Answer:
ABC
To configure a Secure Private Access (SPA) solution to share endpoint information between FortiSASE and a corporate FortiGate, you need to take the following steps:
✑ Add the FortiGate IP address in the secure private access configuration on
FortiSASE:
✑ Use the FortiClient EMS cloud connector on the corporate FortiGate to connect to FortiSASE:
✑ Register FortiGate and FortiSASE under the same FortiCloud account:
References:
✑ FortiOS 7.2 Administration Guide: Provides details on configuring Secure Private Access and integrating with FortiGate.
✑ FortiSASE 23.2 Documentation: Explains how to set up and manage connections between FortiSASE and corporate FortiGate.
Refer to the exhibits.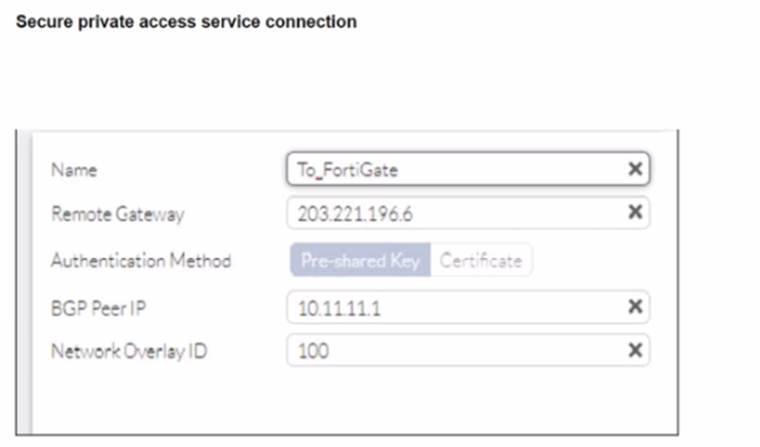
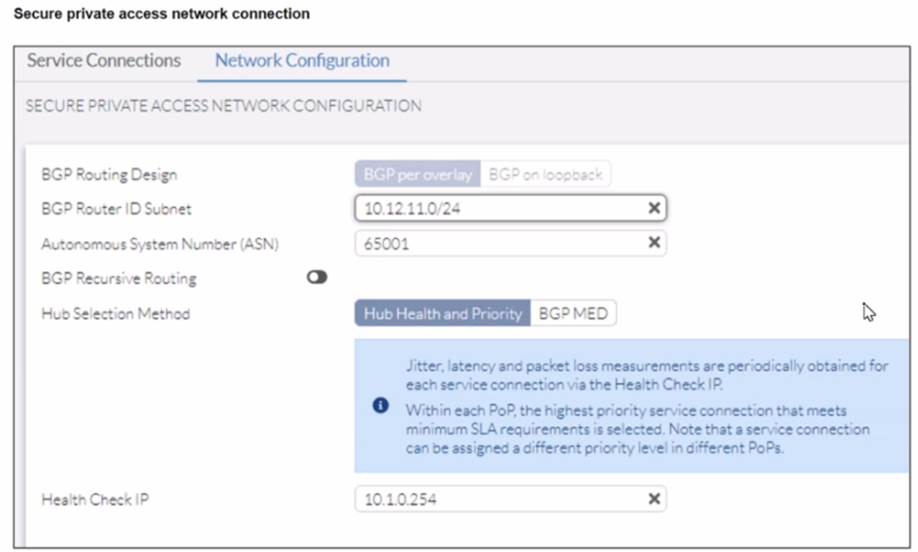
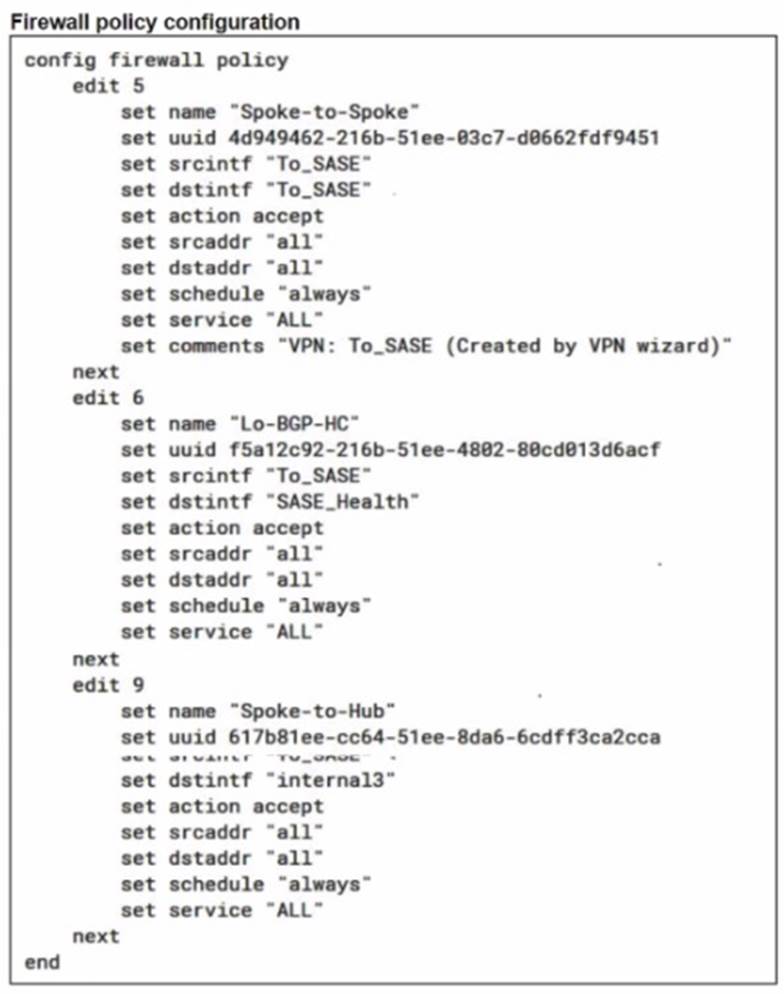
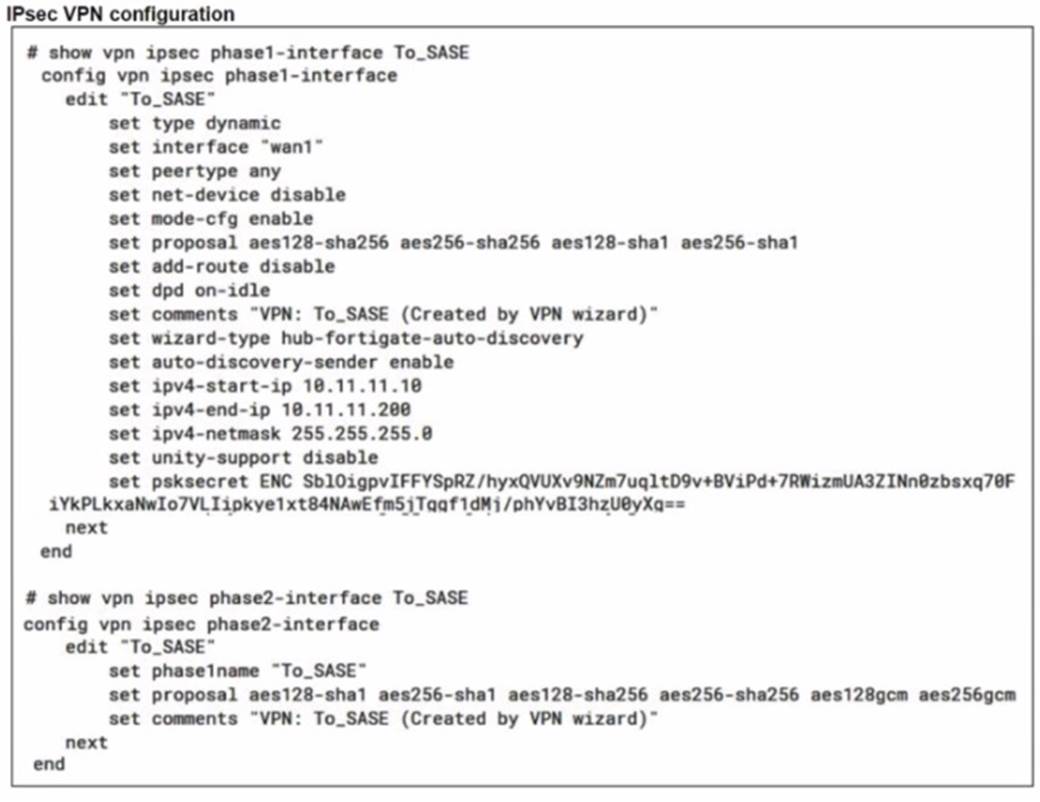
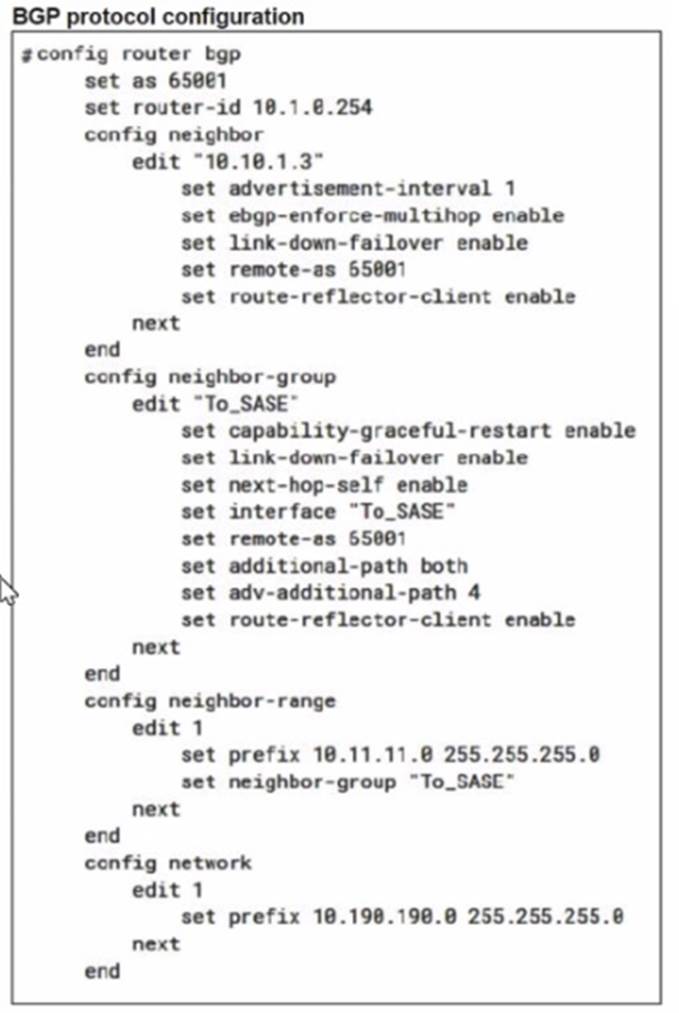
A FortiSASE administrator is trying to configure FortiSASE as a spoke to a FortiGate hub. The VPN tunnel does not establish
Based on the provided configuration, what configuration needs to be modified to bring the tunnel up?
Correct Answer:
C
The VPN tunnel between the FortiSASE spoke and the FortiGate hub is not establishing due to the configuration of mode config, which is not supported by FortiSASE spoke devices. Mode config is used to assign IP addresses to VPN clients dynamically, but this feature is not applicable to FortiSASE spokes.
✑ Mode Config in IPsec:
✑ Configuration Adjustment:
✑ Steps to Disable Mode Config:
References:
✑ FortiOS 7.2 Administration Guide: Provides details on configuring IPsec VPNs and mode config settings.
✑ FortiSASE 23.2 Documentation: Explains the supported configurations for FortiSASE spoke devices and VPN setups.
Which two advantages does FortiSASE bring to businesses with multiple branch offices? (Choose two.)
Correct Answer:
AD
FortiSASE brings the following advantages to businesses with multiple branch offices:
✑ Centralized Management for Simplified Administration:
✑ Eliminates the Need for On-Premises Firewalls:
References:
✑ FortiOS 7.2 Administration Guide: Provides information on the benefits of centralized management and cloud-based security solutions.
✑ FortiSASE 23.2 Documentation: Explains the advantages of using FortiSASE for businesses with multiple branch offices, including reduced need for on-premises firewalls.
Refer to the exhibit.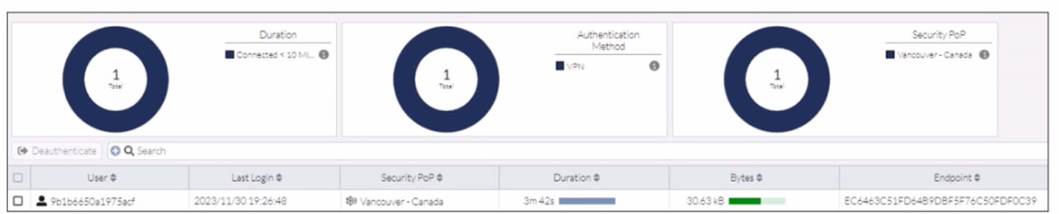
In the user connection monitor, the FortiSASE administrator notices the user name is showing random characters. Which configuration change must the administrator make to get proper user information?
Correct Answer:
A
In the user connection monitor, the random characters shown for the username indicate that log anonymization is enabled. Log anonymization is a feature that hides the actual user information in the logs for privacy and security reasons. To display proper user information, you need to disable log anonymization.
✑ Log Anonymization:
✑ Disabling Log Anonymization:
References:
✑ FortiSASE 23.2 Documentation: Provides detailed steps on enabling and disabling log anonymization.
✑ Fortinet Knowledge Base: Explains the impact of log anonymization on user monitoring and logging.

