Refer to the exhibit.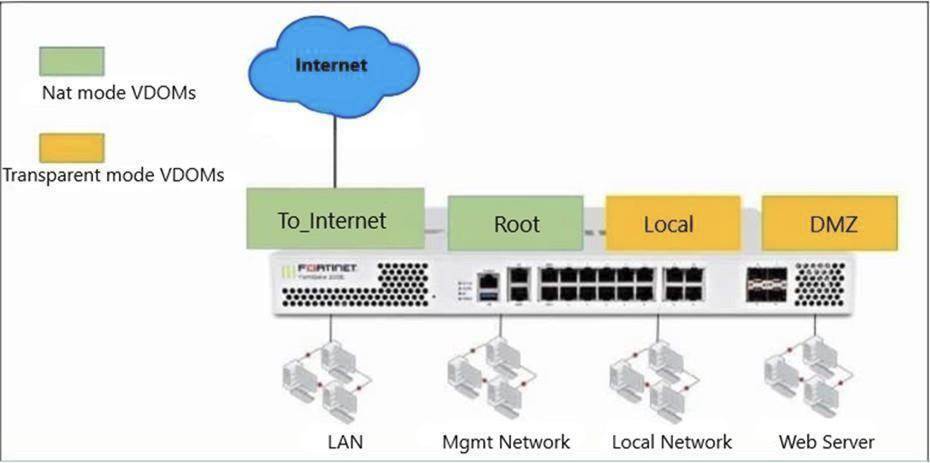
The Root and To_Internet VDOMs are configured in NAT mode. The DMZ and Local VDOMs are configured in transparent mode.
The Root VDOM is the management VDOM. The To_Internet VDOM allows LAN users to access the internet. The To_Internet VDOM is the only VDOM with internet access and is directly connected to ISP modem.
With this configuration, which statement is true?
Correct Answer:
A
In this scenario, multiple Virtual Domains (VDOMs) are used, and each VDOM operates either in NAT mode or transparent mode:
• Root VDOM (management) and To_Internet VDOM are in NAT mode.
• DMZ VDOM and Local VDOM are in transparent mode.
To allow traffic between different VDOMs (e.g., Local and Root), inter-VDOM links must be configured.
Since Local VDOM is in transparent mode, it functions at Layer 2, meaning it requires an inter-VDOM link to pass traffic through the Root VDOM, which operates in NAT mode at Layer 3.
Why the other options are less appropriate:
• B. A default static route is not required on the To_Internet VDOM:
A default route is required on the To_Internet VDOM to send traffic from LAN users to the internet.
• C. Inter-VDOM links are required to allow traffic between the Local and DMZ VDOMs:
Both Local and DMZ are in transparent mode and operate at Layer 2, so direct communication
would require inter-VDOM links if passing through another VDOM.
• D. Inter-VDOM links are not required between the Root and To_Internet VDOMs:
Even if the Root VDOM is only used for management, it still requires inter-VDOM links to communicate with other VDOMs (like To_Internet) in the Security Fabric.
Refer to the exhibit.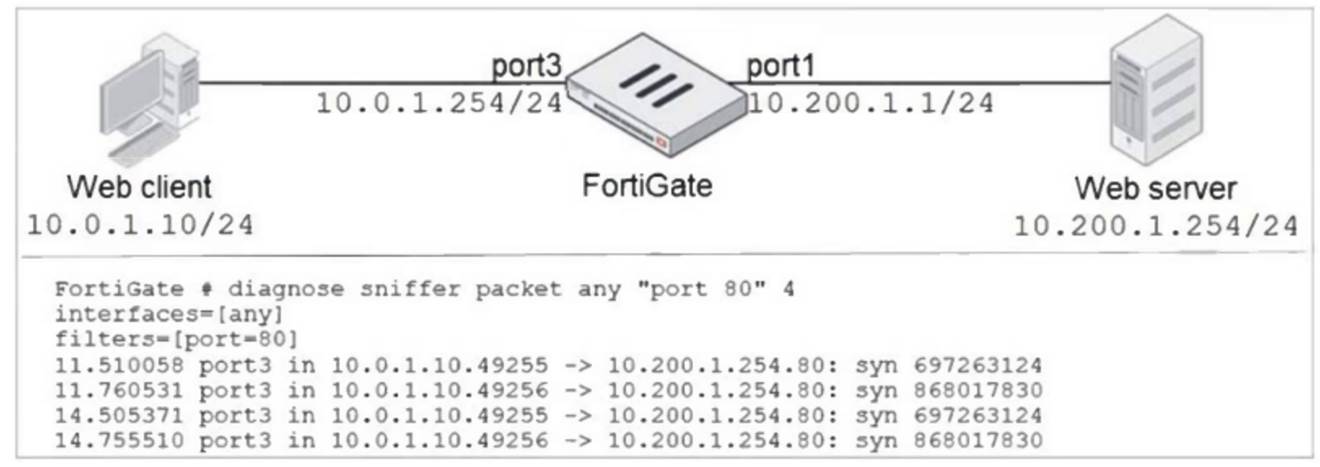
In the network shown in the exhibit, the web client cannot connect to the HTTP web server. The administrator runs the FortiGate built-in sniffer and gets the output shown in the exhibit.
What should the administrator do next, to troubleshoot the problem?
Correct Answer:
A
An employee needs to connect to the office through a high-latency internet connection.
Which SSL VPN setting should the administrator adjust to prevent SSL VPN negotiation failure?
Correct Answer:
C
For a high-latency internet connection, the SSL VPN setting that should be adjusted is:
* C. SSL VPN dtls-hello-timeout: This setting determines how long the FortiGate will wait for a DTLS
hello message from the client. For high-latency connections, increasing this timeout will prevent SSL
VPN negotiation failures caused by delays in receiving the DTLS hello message.
The other options are not suitable:
* A. SSL VPN idle-timeout: This setting controls the idle time allowed before a session is terminated,
which is not relevant to the initial connection establishment.
* B. SSL VPN login-timeout: This setting controls the maximum time allowed for a user to log in, but
does not affect connection negotiation.
* D. SSL VPN session-ttl: This setting controls the total time-to-live for an SSL VPN session but does
not directly address issues caused by high latency.
References
FortiOS 7.4.1 Administration Guide - SSL VPN Configuration, page 1415.
When FortiGate performs SSL/SSH full inspection, you can decide how it should react when it detects an invalid certificate.
Which three actions are valid actions that FortiGate can perform when it detects an invalid certificate? (Choose three.)
Correct Answer:
ADE
When FortiGate performs SSL/SSH full inspection and detects an invalid certificate, there are three valid actions it can take: Allow & Warning: This action allows the session but generates a warning.
Allow & Warning: This action allows the session but generates a warning.  Block & Warning: This action blocks the session and generates a warning.
Block & Warning: This action blocks the session and generates a warning.  Block: This action blocks the session without generating a warning.
Block: This action blocks the session without generating a warning.
Actions such as "Trust & Allow" or just "Allow" without additional configurations are not applicable in the context of handling invalid certificates.
References: FortiOS 7.4.1 Administration Guide: Configuring SSL/SSH inspection profile
FortiOS 7.4.1 Administration Guide: Configuring SSL/SSH inspection profile
View the exhibit.
A user at 192.168.32.15 is trying to access the web server at 172.16.32.254.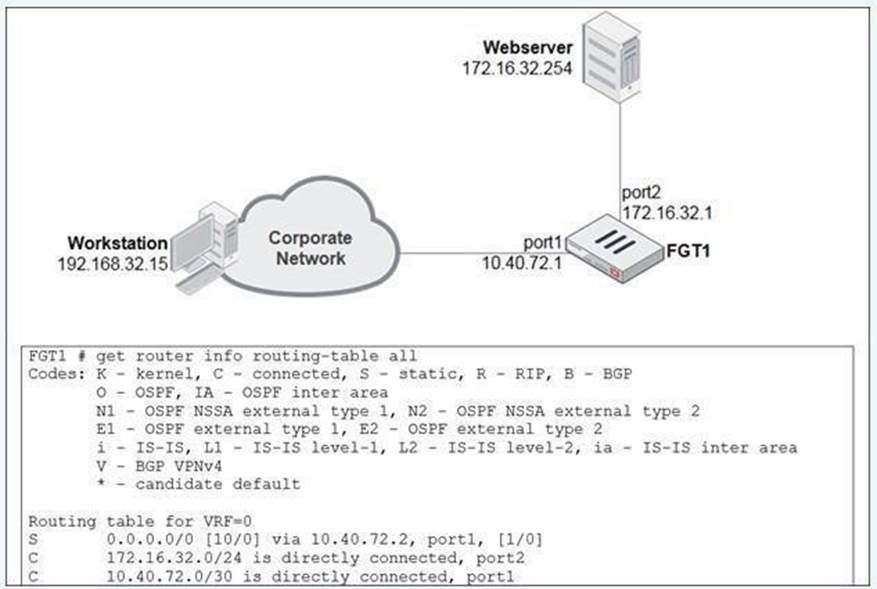
Which two statements best describe how the FortiGate will perform reverse path forwarding (RPF)
checks on this traffic? (Choose two.)
Correct Answer:
BC
When FortiGate performs reverse path forwarding (RPF) checks, it can operate in two modes: Strict
RPF and Loose RPF. Here??s how these two checks work:
In strict RPF, FortiGate checks whether the best route back to the source IP of the packet (in this
case, 192.168.32.15) goes through the same interface on which the packet was received. If the best
return path uses a different interface, the packet is denied. Based on the scenario:
o C. Strict RPF check will allow the traffic:
If the return path for 192.168.32.15 matches the interface where the traffic was received, the strict RPF check will allow the traffic.
• Loose RPF Check:
In loose RPF, FortiGate only checks if there is any route back to the source IP of the packet, regardless of the interface. This is a more permissive check, and if a route exists, the packet will be allowed.
o B. Loose RPF check will allow the traffic:
Since loose RPF requires only that a valid route to the source exists, the traffic is allowed.
Why the other options are less appropriate:
• A. Strict RPF check will deny the traffic:
This would only happen if the return route didn??t match the incoming interface, which is not indicated
here.
• D. Loose RPF check will deny the traffic:
Loose RPF is more permissive, so it will not deny the traffic as long as a valid route to the source IP exists.

