- (Topic 4)
A company is preparing a hypervisor environment to implement a database cluster. One of the requirements is to share the disks between the nodes of the cluster to access the same LUN. Which of the following protocols Should the company use? (Select TWO)
Correct Answer:
CF
The correct answer is C and F. iSCSI and FC.
iSCSI and FC are protocols that the company can use to share the disks between the nodes of the cluster to access the same LUN. A LUN, or logical unit number, is a unique identifier for a block of storage space that can be accessed by a host system or a cluster of systems. iSCSI and FC are both block-level protocols that allow transferring data between the storage device and the host system or cluster over a network.
iSCSI stands for Internet Small Computer System Interface, which is a protocol that uses TCP/IP to send SCSI commands over an Ethernet network. iSCSI can provide a low-cost and flexible solution for sharing disks between the nodes of the cluster, as it does not require any special hardware or cables, and can use existing network infrastructure. iSCSI can also support encryption and authentication for security purposes .
FC stands for Fibre Channel, which is a protocol that uses optical fiber cables to send SCSI commands over a dedicated network. FC can provide a high-performance and reliable solution for sharing disks between the nodes of the cluster, as it offers high bandwidth, low latency, and error correction. FC can also support zoning and masking for security purposes .
CIFS, or Common Internet File System, is a file-level protocol that allows sharing files and folders over a network. CIFS does not support sharing disks or accessing LUNs at the block level.
FTP, or File Transfer Protocol, is a protocol that allows transferring files between two systems over a network. FTP does not support sharing disks or accessing LUNs at the block level.
NFS, or Network File System, is a file-level protocol that allows sharing files and folders over a network. NFS does not support sharing disks or accessing LUNs at the block level. RAID 10, or Redundant Array of Independent Disks 10, is a storage configuration that combines mirroring and striping to provide high performance and fault tolerance. RAID 10 is not a protocol that allows sharing disks or accessing LUNs over a network.
- (Topic 4)
A cloud administrator received a request to provision a set of cloud resources in an effort to switch to infrastructure as code to automate and optimize operations. The administrator decides to try to run some tests with the following definition: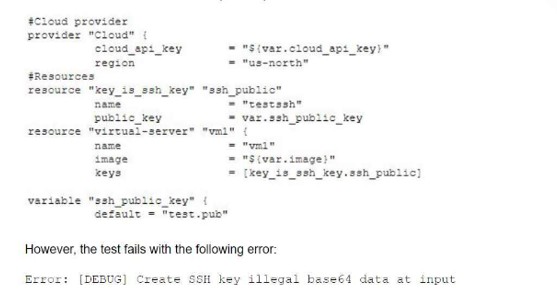
Which of the following is the most likely cause of the issue?
Correct Answer:
C
The error message indicates that the cloud provider is unable to find the public key file that is specified in the definition. The definition uses an environment variable called PUBLIC_KEY_PATH to refer to the location of the public key file. However, if this environment variable has not been set or exported in the shell, the cloud provider will not be able to resolve it and will fail to provision the resources. To fix this issue, the cloud administrator should set and export the environment variable for the public key path before running the definition. References: [CompTIA Cloud+ CV0-003 Certification Study Guide], Chapter 8, Objective 8.1: Given a scenario, implement cloud automation and orchestration.
- (Topic 4)
An organization deployed an application using a cloud provider's internal managed certificates. Developers are unable to retrieve data when calling the API from any machine.
The following error message is in the log:
12-04-2023-10:05:25, SSL Negotiation Error 12-04-2023-10:05:28,Invalid Certificate
12-04-2023-10:05:29, TLS Handshake Failed 12-04-2023-10:05:30,Connection Closed
Which of the following is the most likely cause of the error?
Correct Answer:
D
The error message indicates that the SSL/TLS handshake failed due to an invalid certificate. This means that the client machine does not trust the certificate authority (CA) that issued the certificate for the cloud provider’s API. A self-signed certificate or an insecure cipher would not cause this error, as they would be detected during the certificate validation process. The TLS version is not relevant, as the error occurs before the protocol negotiation. The most likely cause of the error is that the client machine does not have the root CA certificate installed in its trust store, or that the cloud provider’s certificate chain is incomplete or broken. To fix the error, the client machine needs to install the root CA certificate or the cloud provider needs to fix its certificate chain. References: The Official CompTIA Cloud+ Self-Paced Study Guide (CV0-003) eBook, Chapter 6, Section 6.2, page 2321
- (Topic 3)
A cloud engineer recently used a deployment script template to implement changes on a cloud-hosted web application. The web application communicates with a managed database on the back end. The engineer later notices the web application is no longer receiving data from the managed database. Which of the following is the MOST likely cause of the issue?
Correct Answer:
C
The most likely cause of the issue is C. Misconfiguration in the network ACL. A network ACL (access control list) is a set of rules that controls the inbound and outbound traffic for a subnet or a virtual network in a cloud environment. A misconfiguration in the network ACL can block the communication between the web application and the managed database, resulting in data loss or unavailability. For example, according to the Azure SQL Database documentation1, if you use a virtual network service endpoint to secure your database, you need to configure the network ACL to allow traffic from the web application subnet to the database subnet. Otherwise, the web application will not be able to connect
to the database. Similarly, according to the DigitalOcean tutorial2, if you use a managed database cluster, you need to add the web application’s IP address or Droplet to the cluster’s trusted sources list. Otherwise, the web application will not be able to access the database.
A misconfiguration in the user permissions, the routing traffic, or the firewall can also cause connectivity issues between the web application and the managed database, but they are less likely than a misconfiguration in the network ACL. A misconfiguration in the user permissions can prevent the web application from authenticating or authorizing with the database, but it will not affect the data transmission. A misconfiguration in the routing traffic can cause packets to be lost or delayed, but it will not block the communication entirely. A misconfiguration in the firewall can filter out unwanted traffic, but it will not affect the traffic that is allowed by the network ACL. Therefore, these are not the most likely causes of the issue. For more information on how to troubleshoot connectivity issues between a cloud- hosted web application and a managed database, you can refer to the AWS documentation3 or the Google Cloud documentation.
- (Topic 3)
A product-based company wants to transition to a method that provides the capability to enhance the product seamlessly and keep the development iterations to a shorter time frame. Which of the following would BEST meet these requirements?
Correct Answer:
C
CI/CD tools are software tools that enable continuous integration and continuous delivery or deployment, which are methods to frequently deliver software products to customers by introducing automation into the stages of software development. CI/CD tools can help a product-based company to transition to a method that provides the capability to enhance the product seamlessly and keep the development iterations to a shorter time frame, as they can offer the following benefits:
✑ Faster and more reliable delivery of software products, as CI/CD tools can automate the processes of building, testing, and deploying code changes, reducing manual errors and delays.
✑ Higher quality and performance of software products, as CI/CD tools can facilitate ongoing feedback, monitoring, and improvement of the code, ensuring that it meets the customer expectations and requirements.
✑ Greater collaboration and communication among the development teams, as CI/CD tools can integrate with various tools and platforms, such as version control systems, code repositories, testing frameworks, and cloud services, enabling a seamless workflow and visibility across the software lifecycle.
Some examples of popular CI/CD tools are Jenkins1, CircleCI2, GitLab CI/CD3, and AWS CodeBuild4.

