- (Topic 3)
Audit and system logs are being forwarded to a syslog solution. An administrator observes that two application servers have not generated any logs for a period of three days, while
others continue to send logs normally. Which of the following BEST explains what is occurring?
Correct Answer:
B
One possible explanation for why two application servers have not generated any logs for a period of three days, while others continue to send logs normally, is that the application servers were migrated to the cloud as laaS (Infrastructure as a Service) instances. laaS is a cloud service model that provides virtualized computing resources over the internet, such as servers, storage, network, and operating systems. When an application server is migrated to the cloud as an laaS instance, it may require some configuration changes to enable the syslog forwarding to the same destination as before. For example, the laaS instance may have a different IP address, hostname, firewall rules, or network settings than the original server. If these changes are not properly made, the laaS instance may not be able to communicate with the syslog solution and send logs as expected.
- (Topic 3)
A cloud engineer has deployed a virtual storage appliance into a public cloud environment. The storage appliance has a NAT to a public IP address. An administrator later notices there are some strange files on the storage appliance and a large spike in network traffic on the machine. Which of the following is the MOST likely cause?
Correct Answer:
A
One possible cause for the strange files and the large spike in network traffic on the storage appliance is that the default password is still configured on the appliance. A default password is a password that is set by the manufacturer or vendor of a device or software, and it is often easy to guess or find online. If the cloud engineer did not change the default password after deploying the virtual storage appliance, it could allow unauthorized users to access the appliance remotely and upload or download files, which could explain the symptoms observed by the administrator. This is a serious security risk that could compromise the confidentiality, integrity, and availability of the data stored on the appliance.
- (Topic 2)
A cloud architect is reviewing four deployment options for a new application that will be hosted by a public cloud provider. The application must meet an SLA that allows for no
more than five hours of downtime annually. The cloud architect is reviewing the SLAs for the services each option will use: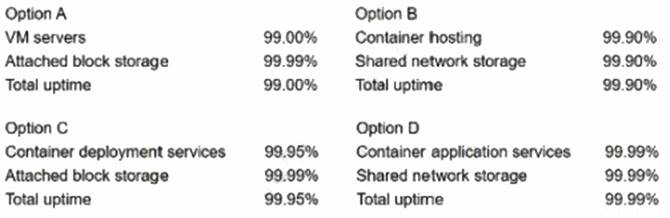
Based on the information above, which of the following minimally complies with the SLA requirements?
Correct Answer:
B
Option B is what minimally complies with the SLA (Service Level Agreement) requirements of allowing for no more than five hours of downtime annually for a new application that will be hosted by a public cloud provider. An SLA is a contract or agreement that defines the level of service or performance that a customer expects from a provider, such as availability, reliability, scalability, security, etc. An SLA can help to measure and monitor the quality and satisfaction of service or performance, as well as identify any penalties or rewards for meeting or failing to meet the SLA. Option B minimally complies with the SLA requirements by using services that have availability percentages that are equal to or higher than 99.95%, which translates to no more than five hours of downtime annually. Option B uses services such as:
✑ Compute: This is a service that provides computing resources such as servers, processors, memory, etc., to run applications or functions. Option B uses compute service with availability percentage of 99.95%, which means that it guarantees to be available for 99.95% of the time in a year, and allows for no more than five hours of downtime in a year.
✑ Storage: This is a service that provides storage resources such as disks, volumes, files, etc., to store data or information. Option B uses storage service with availability percentage of 99.99%, which means that it guarantees to be available for 99.99% of the time in a year, and allows for no more than one hour of downtime in a year.
✑ Database: This is a service that provides database resources such as tables, records, queries, etc., to store and retrieve data or information. Option B uses database service with availability percentage of 99.95%, which means that it guarantees to be available for 99.95% of the time in a year, and allows for no more than five hours of downtime in a year.
- (Topic 4)
A cloud administrator needs to verify domain ownership with a third party. The third party has provided a secret that must be added to the DNS server. Which of the following DNS records does the administrator need to update to include the secret?
Correct Answer:
B
TXT is a type of DNS record that can store arbitrary text data, such as a secret, a verification code, or a configuration parameter. TXT records are often used to verify domain ownership with a third party, such as a certificate authority, an email service provider, or a cloud service provider. The third party can check the TXT record of the domain and compare it with the secret they provided to confirm the identity and authority of the domain owner .
- (Topic 2)
An organization suffered a critical failure of its primary datacenter and made the decision to switch to the DR site. After one week of using the DR site, the primary datacenter is now ready to resume operations.
Which of the following is the MOST efficient way to bring the block storage in the primary datacenter up to date with the DR site?
Correct Answer:
A
Reference: https://www.ibm.com/docs/en/cloud-pak-system-w3550/2.3.3?topic=system- administering-block-storage-replication
Setting up replication is the most efficient way to bring the block storage in the primary datacenter up to date with the DR site after a critical failure. Replication is a process of copying data from one location to another in real-time or near real-time. Replication can be synchronous or asynchronous, depending on the latency and bandwidth requirements. Replication can ensure data consistency and availability across multiple sites and facilitate faster recovery.

