Which of the following items should be included in a vulnerability scan report? (Choose two.)
Correct Answer:
DE
A vulnerability scan report should include information about the affected hosts, such as their IP addresses, hostnames, operating systems, and services. It should also include a risk score for each vulnerability, which indicates the severity and potential impact of the vulnerability on the host and the organization. Official References: https://www.first.org/cvss/
A company is in the process of implementing a vulnerability management program. no-lich of the following scanning methods should be implemented to minimize the risk of OT/ICS devices malfunctioning due to the vulnerability identification process?
Correct Answer:
B
Passive scanning is a method of vulnerability identification that does not send any packets or probes to the target devices, but rather observes and analyzes the network traffic passively. Passive scanning can minimize the risk of OT/ICS devices malfunctioning due to the vulnerability identification process, as it does not interfere with the normal operation of the devices or cause any network disruption. Passive scanning can also detect vulnerabilities that active scanning may miss, such as misconfigured devices, rogue devices or unauthorized traffic. Official References:
✑ https://partners.comptia.org/docs/default-source/resources/comptia-cysa-cs0-002-exam-objectives
✑ https://www.comptia.org/blog/the-new-comptia-cybersecurity-analyst-your- questions-answered
✑ https://www.comptia.org/certifications/cybersecurity-analyst
A recent penetration test discovered that several employees were enticed to assist attackers by visiting specific websites and running downloaded files when prompted by phone calls. Which of the following would best address this issue?
Correct Answer:
A
Increasing training and awareness for all staff is the best way to address the issue of employees being enticed to assist attackers by visiting specific websites and running downloaded files when prompted by phone calls. This issue is an example of social engineering, which is a technique that exploits human psychology and behavior to manipulate people into performing actions or divulging information that benefit the attackers. Social engineering can take many forms, such as phishing, vishing, baiting, quid pro quo, or impersonation. The best defense against social engineering is to educate and train the staff on how to recognize and avoid common social engineering tactics, such as:
✑ Verifying the identity and legitimacy of the caller or sender before following their instructions or clicking on any links or attachments
✑ Being wary of unsolicited or unexpected requests for information or action, especially if they involve urgency, pressure, or threats
✑ Reporting any suspicious or anomalous activity to the security team or the appropriate authority
✑ Following the organization’s policies and procedures on security awareness and best practices
Official References:
✑ https://partners.comptia.org/docs/default-source/resources/comptia-cysa-cs0-002- exam-objectives
✑ https://www.comptia.org/certifications/cybersecurity-analyst
✑ https://www.comptia.org/blog/the-new-comptia-cybersecurity-analyst-your- questions-answered
Which of the following is the most important factor to ensure accurate incident response reporting?
Correct Answer:
A
A well-defined timeline of the events is the most important factor to ensure accurate incident response reporting, as it provides a clear and chronological account of what happened, when it happened, who was involved, and what actions were taken. A timeline helps to identify the root cause of the incident, the impact and scope of the damage, the effectiveness of the response, and the lessons learned for future improvement. A timeline also helps to communicate the incident to relevant stakeholders, such as management, legal, regulatory, or media entities. The other factors are also important for incident response reporting, but they are not as essential as a well-defined timeline. Official References:
✑ https://www.ibm.com/topics/incident-response
✑ https://www.crowdstrike.com/cybersecurity-101/incident-response/incident- response-steps/
HOTSPOT
The developers recently deployed new code to three web servers. A daffy automated external device scan report shows server vulnerabilities that are failure items according to PCI DSS.
If the venerability is not valid, the analyst must take the proper steps to get the scan clean. If the venerability is valid, the analyst must remediate the finding.
After reviewing the information provided in the network diagram, select the STEP 2 tab to
complete the simulation by selecting the correct Validation Result and Remediation Action for each server listed using the drop-down options.
INTRUCTIONS:
The simulation includes 2 steps.
Step1:Review the information provided in the network diagram and then move to the STEP 2 tab.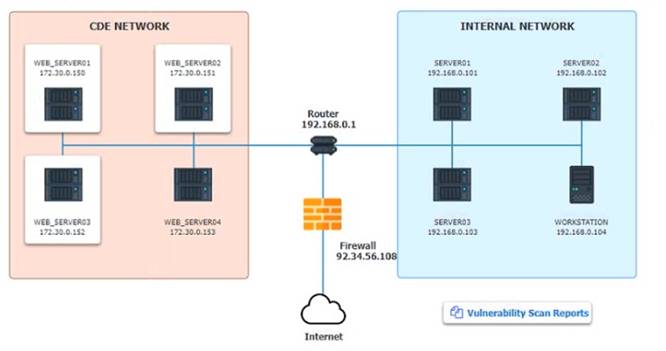
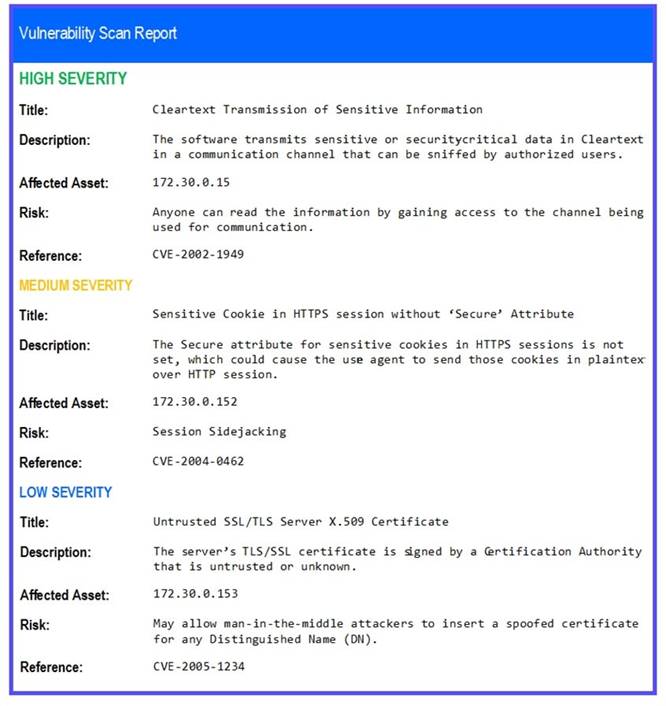
STEP 2: Given the Scenario, determine which remediation action is required to address the vulnerability.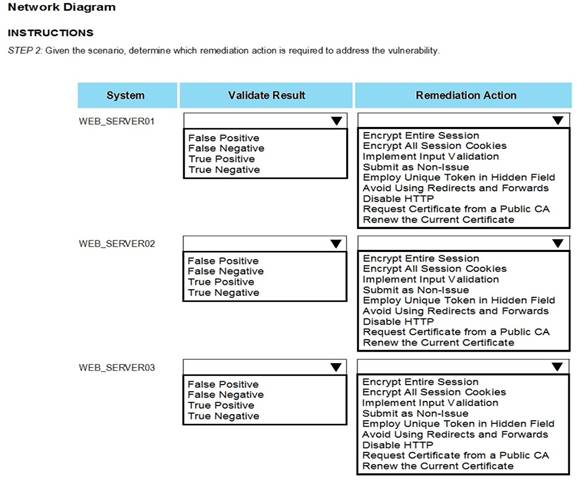
Solution: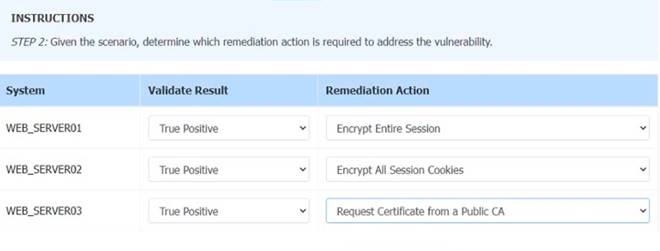
Does this meet the goal?
Correct Answer:
A

