You want to store files that will be accessible by every user on your network. Which endpoint device do you need?
Correct Answer:
B
To store files that will be accessible by every user on a network, you would need aserver. A server is a computer system that provides data to other computers. It can serve data to systems on a local network (LAN) or a wide network (WAN) over the internet.In this context, a file server would be set up to store and manage files, allowing users on the network to access them from their own devices1.
References:=
✑ What is a Server?
✑ Understanding Servers and Their Functions
A server is a computer designed to process requests and deliver data to other computers over a local network or the internet. In this case, to store files that will be accessible by every user on the network, a file server is the appropriate endpoint device. It provides a centralized location for storing and managing files, allowing users to access and share files easily.
✑ A. Access point: Provides wireless connectivity to a network.
✑ C. Hub: A basic networking device that connects multiple Ethernet devices together, making them act as a single network segment.
✑ D. Switch: A networking device that connects devices on a computer network by using packet switching to forward data to the destination device.
Thus, the correct answer is B. Server.
References:=
✑ File Server Overview (Cisco)
✑ Server Roles in Networking (Cisco)
Which wireless security option uses a pre-shared key to authenticate clients?
Correct Answer:
A
WPA2-Personal, also known as WPA2-PSK (Pre-Shared Key), is the wireless security option that uses a pre-shared key to authenticate clients. This method is designed for home and small office networks and doesn??t require an authentication server. Instead, every user on the network uses the same key or passphrase to connect1.
References :=
•What is a Wi-Fi Protected Access Pre-Shared Key (WPA-PSK)?
•Exploring WPA-PSK and WiFi Security
=========================
•WPA2-Personal: This wireless security option uses a pre-shared key (PSK) for authentication. Each client that connects to the network must use this key to gain access. It is designed for home and small office networks where simplicity and ease of use are important.
•WPA2-Enterprise: Unlike WPA2-Personal, WPA2-Enterprise uses 802.1x authentication with an authentication server (such as RADIUS) and does not rely on a pre-shared key.
•802.1x: This is a network access control protocol for LANs, particularly wireless LANs. It provides an authentication mechanism to devices wishing to attach to a LAN or WLAN.
•802.1q: This is a networking standard that supports VLAN tagging on Ethernet networks and is not related to wireless security.
References:
•Cisco Documentation on WPA2 Security: Cisco WPA2
•Understanding Wireless Security: Wireless Security Guide
DRAG DROP
Move each network type from the list on the left to the correct example on the right.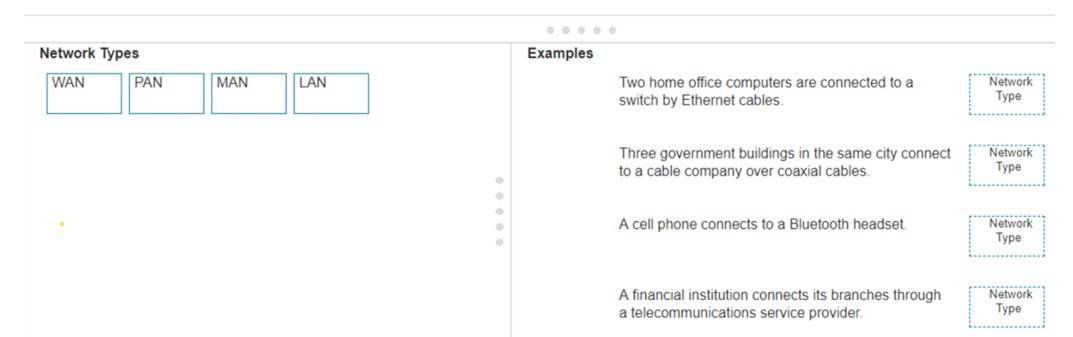
Solution:
✑ Two home office computers are connected to a switch by Ethernet cables.
✑ Three government buildings in the same city connect to a cable company over coaxial cables.
✑ A cell phone connects to a Bluetooth headset.
✑ A financial institution connects its branches through a telecommunications service provider.
✑ LAN (Local Area Network): Used for connecting devices within a small geographical area such as a single building or home.
✑ MAN (Metropolitan Area Network): Covers a larger geographical area than a LAN,
typically a city or campus.
✑ PAN (Personal Area Network): Connects devices within the range of an individual person, such as connecting a phone to a Bluetooth headset.
✑ WAN (Wide Area Network): Spans large geographical areas, connecting multiple LANs across cities, countries, or continents.
References:
✑ Network Types Overview: Cisco Networking Basics
✑ Understanding Different Network Types: Network Types Guide
Does this meet the goal?
Correct Answer:
A
Which protocol allows you to securely upload files to another computer on the internet?
Correct Answer:
A
SFTP, or Secure File Transfer Protocol, is a protocol that allows for secure file transfer capabilities between networked hosts. It is a secure extension of the File Transfer Protocol (FTP). SFTP encrypts both commands and data, preventing passwords and sensitive information from being transmitted openly over the network. It is typically used for secure file transfers over the internet and is built on the Secure Shell (SSH) protocol1. References :=
•What Is SFTP? (Secure File Transfer Protocol)
•How to Use SFTP to Safely Transfer Files: A Step-by-Step Guide
•Secure File Transfers: Best Practices, Protocols And Tools
The Secure File Transfer Protocol (SFTP) is a secure version of the File Transfer Protocol (FTP) that uses SSH (Secure Shell) to encrypt all commands and data. This ensures that sensitive information, such as usernames, passwords, and files being transferred, are securely transmitted over the network.
•ICMP (Internet Control Message Protocol) is used for network diagnostics and is not designed for file transfer.
•NTP (Network Time Protocol) is used to synchronize clocks between computer systems and is not related to file transfer.
•HTTP (HyperText Transfer Protocol) is used for transmitting web pages over the internet and does not inherently provide secure file transfer capabilities.
Thus, the correct protocol that allows secure uploading of files to another computer on the internet is SFTP.
References :=
•Cisco Learning Network
•SFTP Overview (Cisco)

