Which component of the AAA service security model provides identity verification?
Correct Answer:
C
The AAA service security model consists of three components: Authentication, Authorization, and Accounting.
•Authentication: This is the process of verifying the identity of a user or device. It ensures that only legitimate users can access the network or service.
•Authorization: This determines what an authenticated user is allowed to do or access within the network.
•Auditing/Accounting: This component tracks the actions of the user, including what resources they access and what changes they make.
Thus, the correct answer is C. Authentication. References :=
•Cisco AAA Overview
•Understanding AAA (Authentication, Authorization, and Accounting)
You need to connect a computer's network adapter to a switch using a 1000BASE-T cable. Which connector should you use?
Correct Answer:
D
•1000BASE-T Cable: This refers to Gigabit Ethernet over twisted-pair cables (Cat 5e or higher).
•Connector: RJ-45 connectors are used for Ethernet cables, including those used for 1000BASE-T.
•Coax: Used for cable TV and older Ethernet standards like 10BASE2.
•RJ-11: Used for telephone connections.
•OS2 LC: Used for fiber optic connections. References:
•Ethernet Standards and Cables: Ethernet Cable Guide
DRAG DROP
Move each cloud computing service model from the list on the left to the correct example on the right
Note: You will receive partial credit for each correct answer.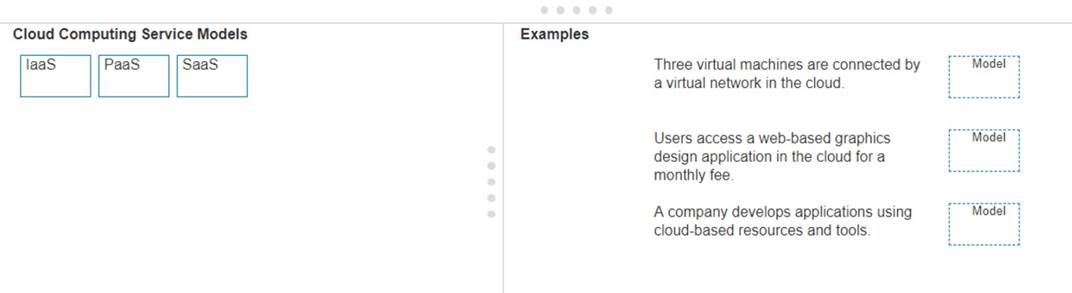
Solution:
✑ Three virtual machines are connected by a virtual network in the cloud.
✑ Users access a web-based graphics design application in the cloud for a monthly fee.
✑ A company develops applications using cloud-based resources and tools.
✑ IaaS (Infrastructure as a Service): Provides virtualized hardware resources that customers can use to build their own computing environments.
✑ PaaS (Platform as a Service): Offers a platform with tools and services to develop,
test, and deploy applications.
✑ SaaS (Software as a Service): Delivers fully functional applications over the internet that users can access and use without managing the underlying infrastructure.
References:
✑ Cloud Service Models: Understanding IaaS, PaaS, SaaS
✑ NIST Definition of Cloud Computing:NIST Cloud Computing
Does this meet the goal?
Correct Answer:
A
HOTSPOT
For each statement about bandwidth and throughput, select True or False. Note: You will receive partial credit for each correct selection.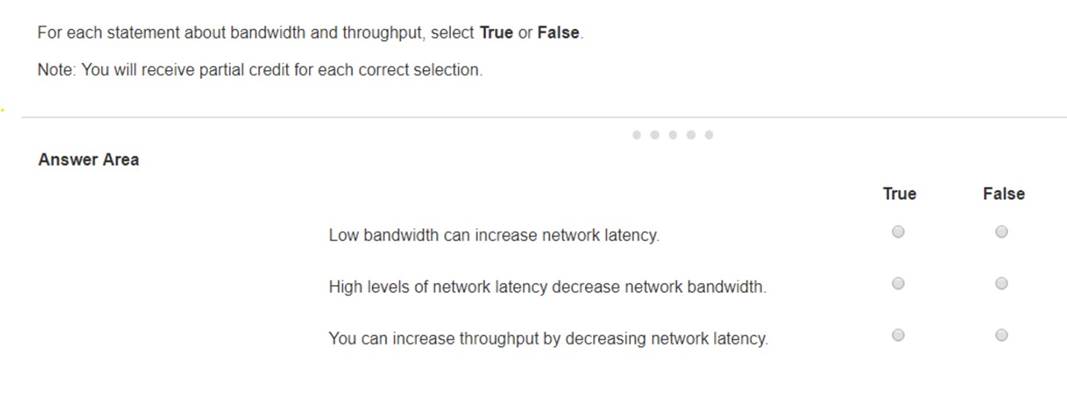
Solution:
✑ Statement 1: Low bandwidth can increase network latency.
✑ Statement 2: High levels of network latency decrease network bandwidth.
✑ Statement 3: You can increase throughput by decreasing network latency.
✑ Bandwidth vs. Latency: Bandwidth refers to the maximum rate at which data can be transferred over a network path. Latency is the time it takes for a data packet to travel from the source to the destination.
References:
✑ Network Performance Metrics: Cisco Network Performance
✑ Understanding Bandwidth and Latency: Bandwidth vs. Latency
Does this meet the goal?
Correct Answer:
A
A user initiates a trouble ticket stating that an external web page is not loading. You determine that other resources both internal and external are still reachable.
Which command can you use to help locate where the issue is in the network path to the external web page?
Correct Answer:
B
The tracert command is used to determine the route taken by packets across an IP network. When a user reports that an external web page is not loading, while other resources are accessible, it suggests there might be an issue at a certain point in the network path to the specific web page. The tracert command helps to diagnose where the breakdown occurs by displaying a list of routers that the packets pass through on their way to the destination. It can identify the network segment where the packets stop progressing, which is valuable for pinpointing where the connectivity issue lies. References := Cisco CCST Networking Certification FAQs – CISCONET Training Solutions, Command Prompt (CMD): 10 network-related commands you should know, Network Troubleshooting Commands Guide: Windows, Mac & Linux - Comparitech, How to Use the Traceroute and Ping Commands to Troubleshoot Network, Network Troubleshooting Techniques: Ping,
Traceroute, PathPing.
•tracert Command: This command is used to determine the path packets take to reach a destination. It lists all the hops (routers) along the way and can help identify where the delay or failure occurs.
•ping -t: This command sends continuous ping requests and is useful for determining if a host is reachable but does not provide path information.
•ipconfig /all: This command displays all current TCP/IP network configuration values and can be used to verify network settings but not to trace a network path.
•nslookup: This command queries the DNS to obtain domain name or IP address mapping, useful for DNS issues but not for tracing network paths.
References:
•Microsoft tracert Command: tracert Command Guide
•Troubleshooting Network Issues with tracert: Network Troubleshooting Guide

