A company hosts a platform-as-a-service solution with a web-based front end, through which customer interact with data sets. A security administrator needs to deploy controls to prevent application-focused attacks. Which of the following most directly supports the administrator's objective'
Correct Answer:
D
The best way to prevent application-focused attacks for a platform-as-a- service solution with a web-based front end is to create Web Application Firewall (WAF) policies for relevant programming languages. Here's why:
✑ Application-Focused Attack Prevention: WAFs are designed to protect web
applications by filtering and monitoring HTTP traffic between a web application and the Internet. They help prevent attacks such as SQL injection, cross-site scripting (XSS), and other application-layer attacks.
✑ Customizable Rules: WAF policies can be tailored to the specific programming
languages and frameworks used by the web application, providing targeted protection based on known vulnerabilities and attack patterns.
✑ Real-Time Protection: WAFs provide real-time protection, blocking malicious
requests before they reach the application, thereby enhancing the security posture of the platform.
✑ References:
After an incident response exercise, a security administrator reviews the following table: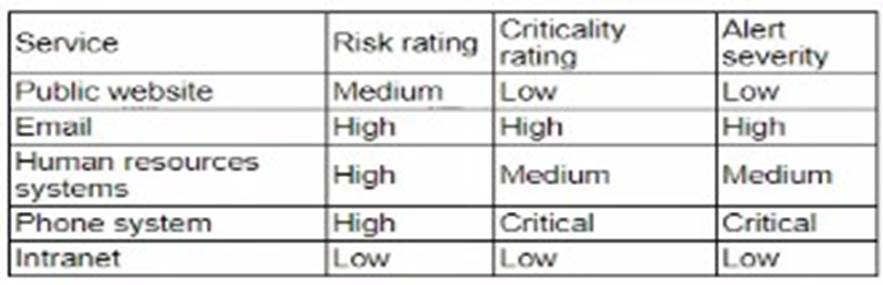
Which of the following should the administrator do to beat support rapid incident response in the future?
Correct Answer:
B
Enabling dashboards for service status monitoring is the best action to support rapid incident response. The table shows various services with different risk, criticality, and alert severity ratings. To ensure timely and effective incident response, real-time visibility into the status of these services is crucial.
Why Dashboards for Service Status Monitoring?
✑ Real-time Visibility: Dashboards provide an at-a-glance view of the current status of all critical services, enabling rapid detection of issues.
✑ Centralized Monitoring: A single platform to monitor the status of multiple services helps streamline incident response efforts.
✑ Proactive Alerting: Dashboards can be configured to show alerts and anomalies immediately, ensuring that incidents are addressed as soon as they arise.
✑ Improved Decision Making: Real-time data helps incident response teams make informed decisions quickly, reducing downtime and mitigating impact.
Other options, while useful, do not offer the same level of comprehensive, real-time visibility and proactive alerting:
✑ A. Automate alerting to IT support for phone system outages: This addresses one
service but does not provide a holistic view.
✑ C. Send emails for failed log-in attempts on the public website: This is a specific alert for one type of issue and does not cover all services.
✑ D. Configure automated isolation of human resources systems: This is a reactive measure for a specific service and does not provide real-time status monitoring.
References:
✑ CompTIA SecurityX Study Guide
✑ NIST Special Publication 800-61 Revision 2, "Computer Security Incident Handling Guide"
✑ "Best Practices for Implementing Dashboards," Gartner Research
SIMULATION
An IPSec solution is being deployed. The configuration files for both the VPN concentrator and the AAA server are shown in the diagram.
Complete the configuration files to meet the following requirements:
• The EAP method must use mutual certificate-based authentication (With issued client certificates).
• The IKEv2 Cipher suite must be configured to the MOST secure authenticated mode of operation,
• The secret must contain at least one uppercase character, one lowercase character, one numeric character, and one special character, and it must meet a minimum length requirement of eight characters,
INSTRUCTIONS
Click on the AAA server and VPN concentrator to complete the configuration. Fill in the appropriate fields and make selections from the drop-down menus.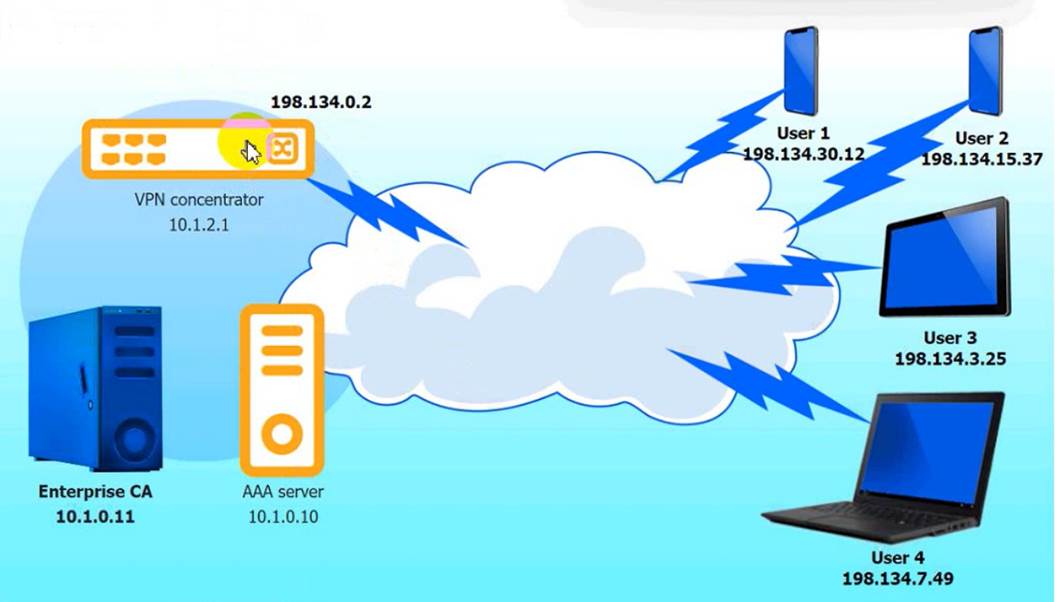
VPN Concentrator: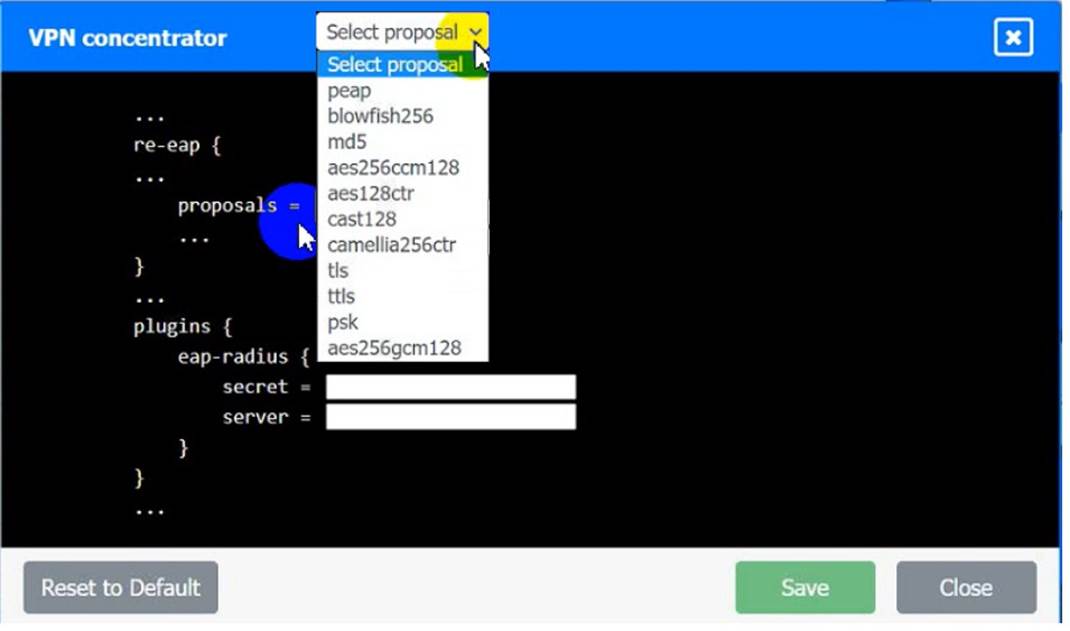
AAA Server: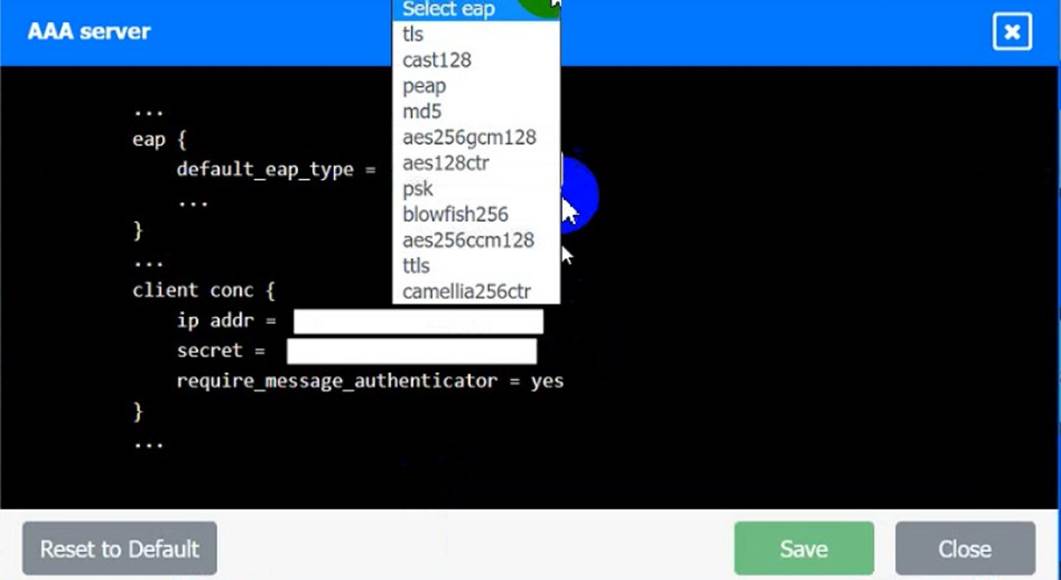
Solution:
VPN Concentrator: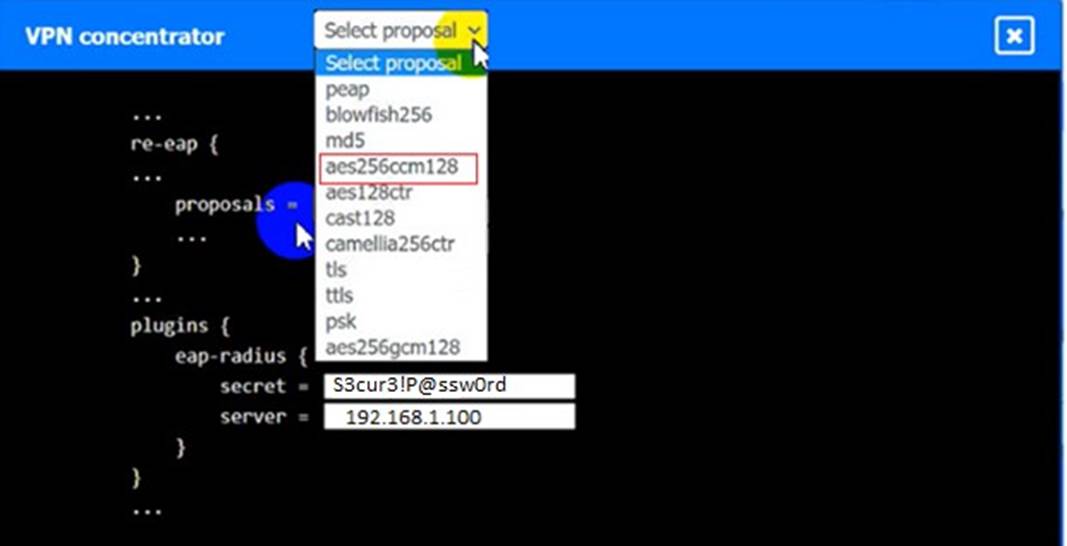
AAA Server: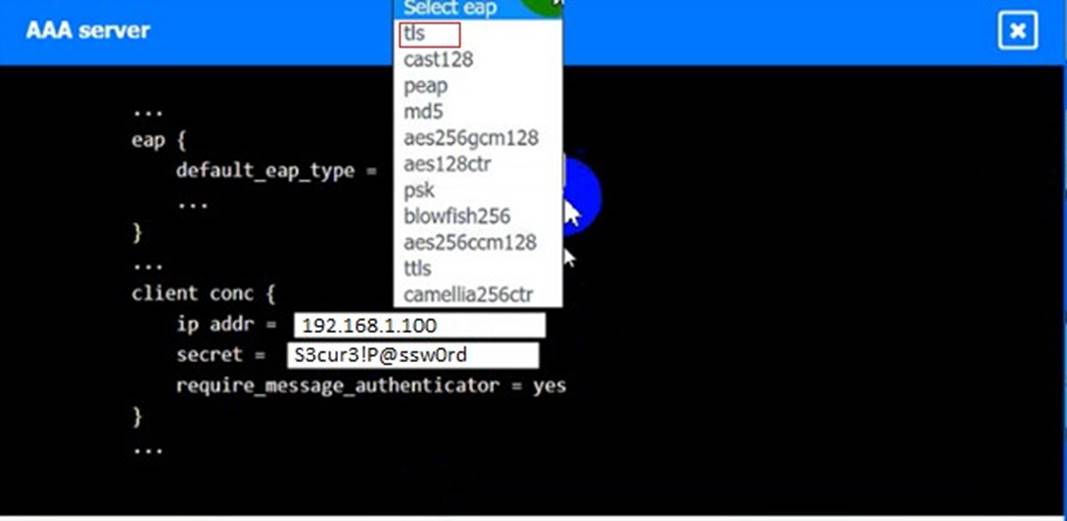
Does this meet the goal?
Correct Answer:
A
A user reports application access issues to the help desk. The help desk reviews the logs for the user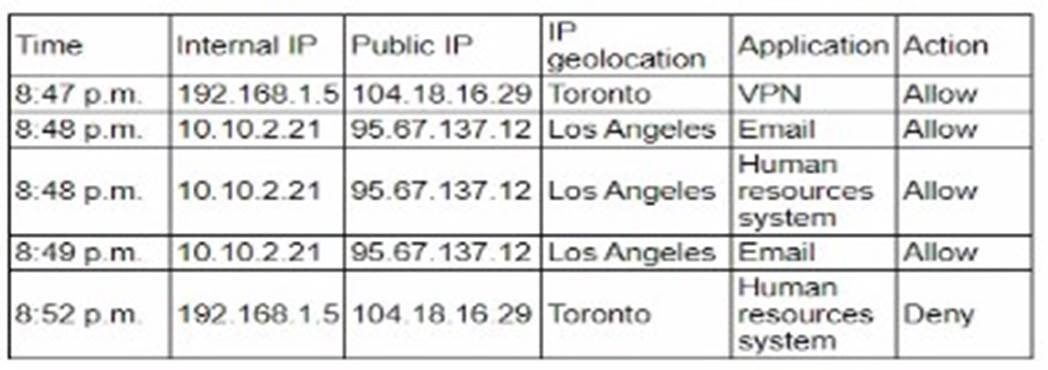
Which of the following is most likely The reason for the issue?
Correct Answer:
A
Based on the provided logs, the user has accessed various applications from different geographic locations within a very short timeframe. This pattern is indicative of the "impossible travel" security rule, a common feature in Single Sign-On (SSO) systems designed to detect and prevent fraudulent access attempts.
Analysis of Logs:
✑ At 8:47 p.m., the user accessed a VPN from Toronto.
✑ At 8:48 p.m., the user accessed email from Los Angeles.
✑ At 8:48 p.m., the user accessed the human resources system from Los Angeles.
✑ At 8:49 p.m., the user accessed email again from Los Angeles.
✑ At 8:52 p.m., the user attempted to access the human resources system from Toronto, which was denied.
These rapid changes in location are physically impossible and typically trigger security measures to prevent unauthorized access. The SSO system detected these inconsistencies and likely flagged the activity as suspicious, resulting in access denial. References:
✑ CompTIA SecurityX Study Guide
✑ NIST Special Publication 800-63B, "Digital Identity Guidelines"
✑ "Impossible Travel Detection," Microsoft Documentation
An audit finding reveals that a legacy platform has not retained loos for more than 30 days The platform has been segmented due to its interoperability with newer technology. As a temporary solution, the IT department changed the log retention to 120 days. Which of the following should the security engineer do to ensure the logs are being properly retained?
Correct Answer:
C
To ensure that logs from a legacy platform are properly retained beyond the default retention period, configuring the SIEM to aggregate the logs is the best approach. SIEM solutions are designed to collect, aggregate, and store logs from various sources, providing centralized log management and retention. This setup ensures that logs are retained according to policy and can be easily accessed for analysis and compliance purposes. References:
✑ CompTIA SecurityX Study Guide: Discusses the role of SIEM in log management and retention.
✑ NIST Special Publication 800-92, "Guide to Computer Security Log Management": Recommends the use of centralized log management solutions, such as SIEM, for effective log retention and analysis.
✑ "Security Information and Event Management (SIEM) Implementation" by David Miller: Covers best practices for configuring SIEM systems to aggregate and retain logs from various sources.

