A security analyst is reviewing the following log: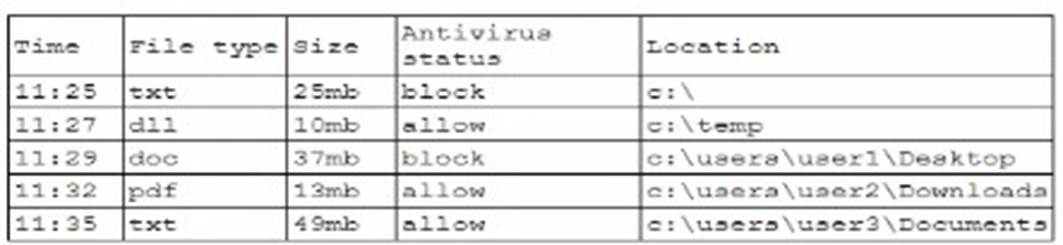
Which of the following possible events should the security analyst investigate further?
Correct Answer:
B
Based on the log provided, the most concerning event that should be investigated further is
the presence of a text file containing passwords that were leaked. Here's why:
✑ Sensitive Information Exposure: A text file containing passwords represents a significant security risk, as it indicates that sensitive credentials have been exposed in plain text, potentially leading to unauthorized access.
✑ Immediate Threat: Password leaks can lead to immediate exploitation by attackers, compromising user accounts and sensitive data. This requires urgent investi
A user submits a help desk ticket stating then account does not authenticate sometimes. An analyst reviews the following logs for the user:
Which of the following best explains the reason the user's access is being denied?
Correct Answer:
B
The logs reviewed for the user indicate that access is being denied due to time-based access restrictions. These restrictions are commonly implemented to limit access to systems during specific hours to enhance security. If a user attempts to authenticate outside of the allowed time window, access will be denied. This measure helps prevent unauthorized access during non-business hours, reducing the risk of security incidents.
References:
✑ CompTIA SecurityX Study Guide: Covers various access control methods, including time-based restrictions, as a means of enhancing security.
✑ NIST Special Publication 800-53, "Security and Privacy Controls for Information Systems and Organizations": Recommends the use of time-based access restrictions as part of access control policies.
✑ "Access Control and Identity Management" by Mike Chapple and Aaron French: Discusses the implementation and benefits of time-based access restrictions.
Which of the following best describes the challenges associated with widespread adoption of homomorphic encryption techniques?
Correct Answer:
D
Homomorphic encryption allows computations to be performed on encrypted data without decrypting it, providing strong privacy guarantees. However, the adoption of homomorphic encryption is challenging due to several factors:
✑ A. Incomplete mathematical primitives: This is not the primary barrier as the
theoretical foundations of homomorphic encryption are well-developed.
✑ B. No use cases to drive adoption: There are several compelling use cases for
homomorphic encryption, especially in privacy-sensitive fields like healthcare and finance.
✑ C. Quantum computers not yet capable: Quantum computing is not directly related
to the challenges of adopting homomorphic encryption.
✑ D. Insufficient coprocessor support: The computational overhead of homomorphic encryption is significant, requiring substantial processing power. Current general- purpose processors are not optimized for the intensive computations required by homomorphic encryption, limiting its practical deployment. Specialized hardware or coprocessors designed to handle these computations more efficiently are not yet widely available.
References:
✑ CompTIA Security+ Study Guide
✑ "Homomorphic Encryption: Applications and Challenges" by Rivest et al.
✑ NIST, "Report on Post-Quantum Cryptography"
A company wants to use loT devices to manage and monitor thermostats at all facilities The thermostats must receive vendor security updates and limit access to other devices within the organization Which of the following best addresses the company's requirements''
Correct Answer:
B
The best approach for managing and monitoring IoT devices, such as thermostats, is to operate them on a separate network with no access to other internal devices. This segmentation ensures that the IoT devices are isolated from the main network, reducing the risk of potential security breaches affecting other critical systems. Additionally, this setup allows for secure vendor updates without exposing the broader network to potential vulnerabilities inherent in IoT devices.
References:
✑ CompTIA SecurityX Study Guide: Recommends network segmentation for IoT devices to minimize security risks.
✑ NIST Special Publication 800-183, "Network of Things": Advises on the isolation of IoT devices to enhance security.
✑ "Practical IoT Security" by Brian Russell and Drew Van Duren: Discusses best practices for securing IoT devices, including network segmentation.
SIMULATION
An IPSec solution is being deployed. The configuration files for both the VPN concentrator and the AAA server are shown in the diagram.
Complete the configuration files to meet the following requirements:
• The EAP method must use mutual certificate-based authentication (With issued client certificates).
• The IKEv2 Cipher suite must be configured to the MOST secure authenticated mode of operation,
• The secret must contain at least one uppercase character, one lowercase character, one numeric character, and one special character, and it must meet a minimum length requirement of eight characters,
INSTRUCTIONS
Click on the AAA server and VPN concentrator to complete the configuration. Fill in the appropriate fields and make selections from the drop-down menus.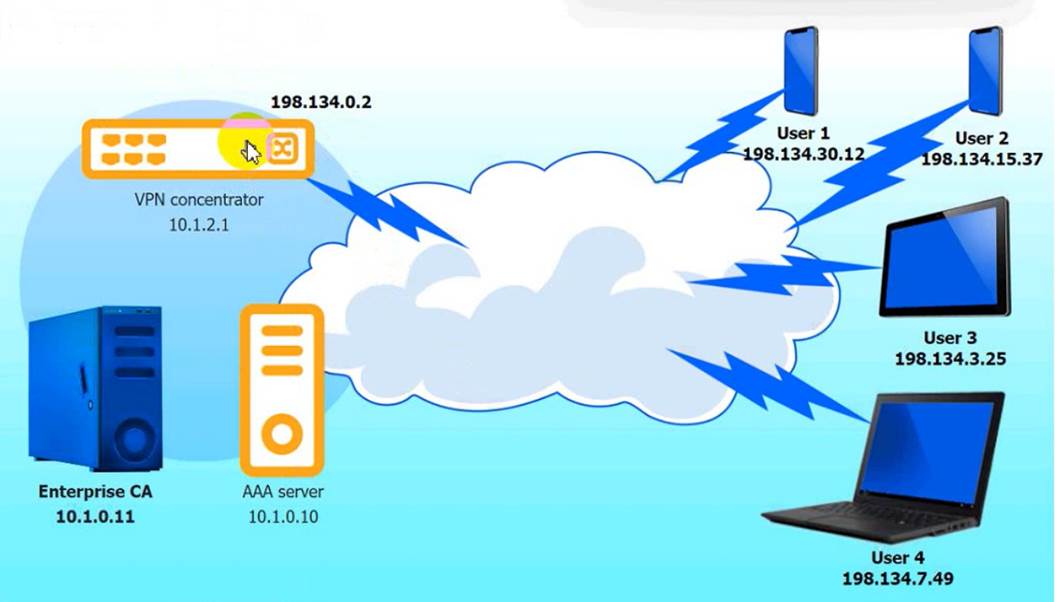
VPN Concentrator: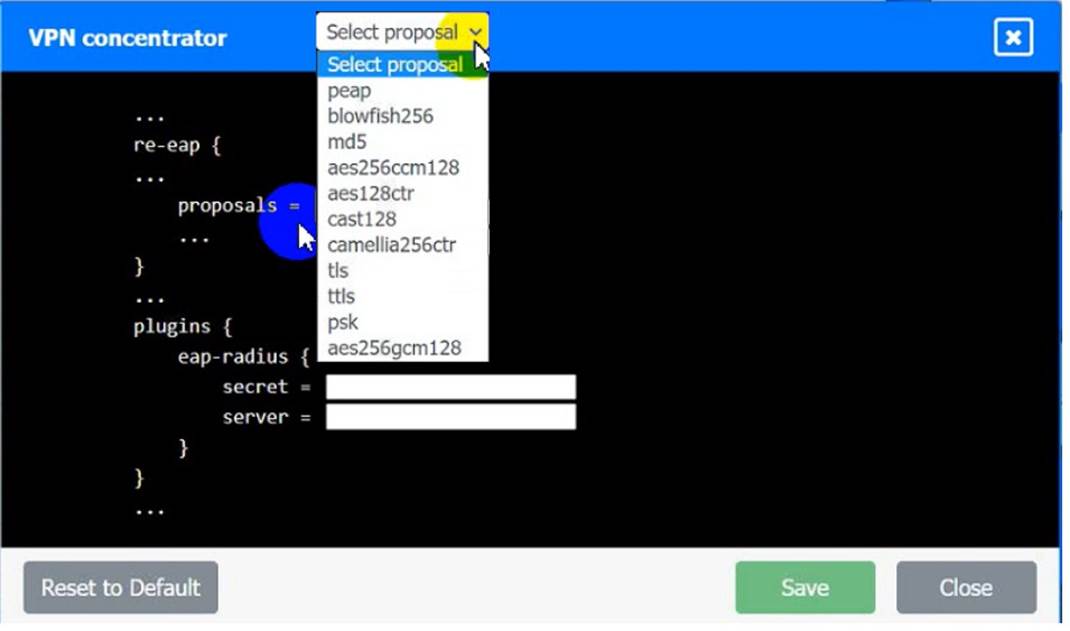
AAA Server: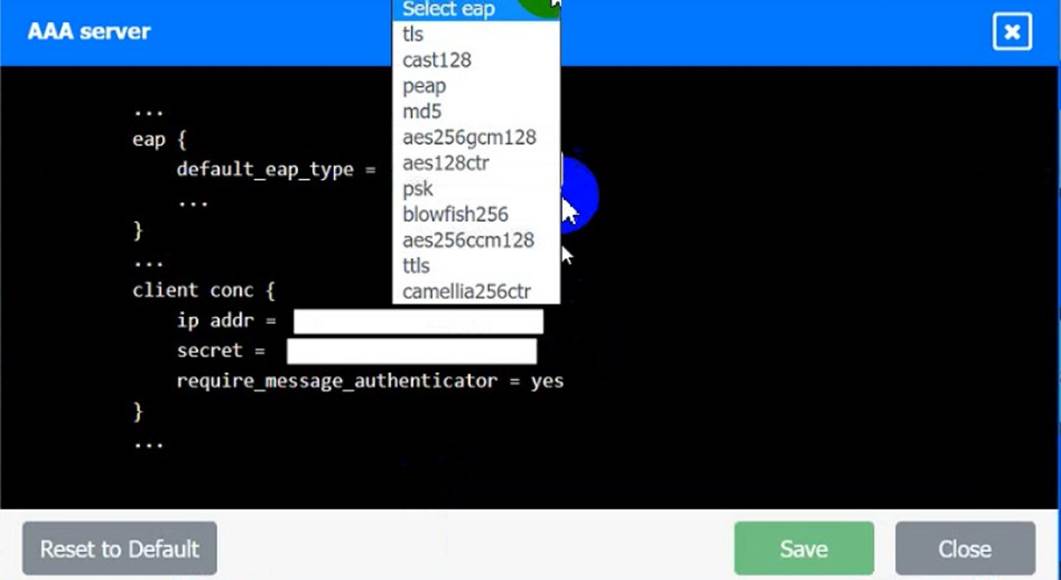
Solution:
VPN Concentrator: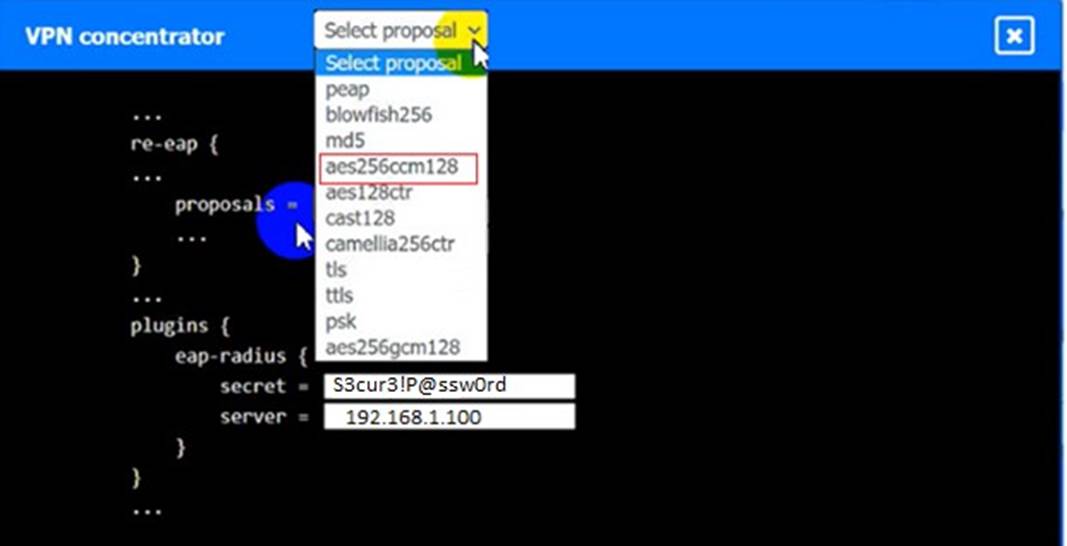
AAA Server: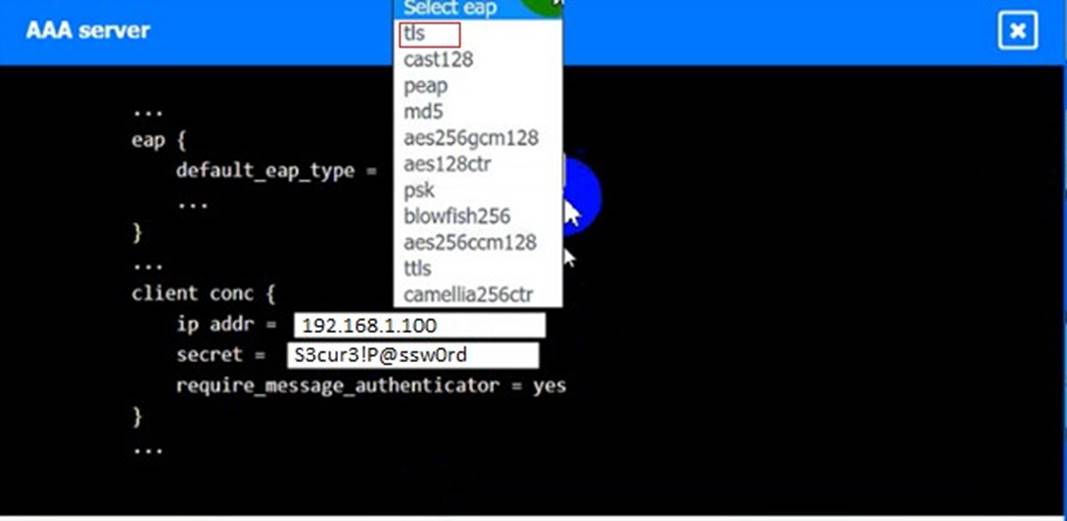
Does this meet the goal?
Correct Answer:
A

