A company is repeatedly being breached by hackers who valid credentials. The company’s Chief information Security Officer (CISO) has installed multiple controls for authenticating users, including biometric and token-based factors. Each successive control has increased overhead and complexity but has failed to stop further breaches. An external consultant is evaluating the process currently in place to support the authentication controls. Which of the following recommendation would MOST likely reduce the risk of unauthorized access?
Correct Answer:
A
A security analyst notices a number of SIEM events that show the following activity: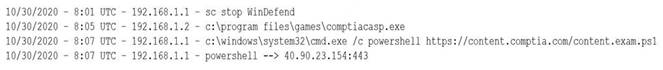
Which of the following response actions should the analyst take FIRST?
Correct Answer:
C
The SIEM events show that powershell.exe was executed on multiple endpoints with an outbound connection to 40.90.23.154, which is an IP address associated with malicious activity. This could indicate a malware infection or a command-and-control channel. The best response action is to configure the forward proxy to block 40.90.23.154, which would prevent further communication with the malicious IP address. Disabling powershell.exe on all endpoints may not be feasible or effective, as it could affect legitimate operations and not remove the malware. Restarting Microsoft Windows Defender may not detect or stop the malware, as it could have bypassed or disabled it. Disabling local administrator privileges on the endpoints may not prevent the malware from running or communicating, as it could have escalated privileges or used other methods. Verified References: https://www.comptia.org/blog/what-is-a-forward-proxy https://partners.comptia.org/docs/default-source/resources/casp-content-guide
A company plans to build an entirely remote workforce that utilizes a cloud-based infrastructure. The Chief Information Security Officer asks the security engineer to design connectivity to meet the following requirements:
Only users with corporate-owned devices can directly access servers hosted by the cloud provider.
The company can control what SaaS applications each individual user can access. User browser activity can be monitored.
Which of the following solutions would BEST meet these requirements?
Correct Answer:
B
A VPN (virtual private network) can provide secure connectivity for remote users to access servers hosted by the cloud provider. A CASB (cloud access security broker) can enforce policies and controls for accessing SaaS applications. A secure web gateway can monitor and filter user browser activity to prevent malicious or unauthorized traffic. Verified References: https://partners.comptia.org/docs/default- source/resources/casp-content-guide https://www.comptia.org/blog/what-is-a-vpn
A company was recently infected by malware. During the root cause analysis. the company determined that several users were installing their own applications. TO prevent further compromises, the company has decided it will only allow authorized applications to run on its systems. Which Of the following should the company implement?
Correct Answer:
D
A security architect needs to implement a CASB solution for an organization with a highly distributed remote workforce. One Of the requirements for the implementation includes the capability to discover SaaS applications and block access to those that are unapproved or identified as risky. Which of the following would BEST achieve this objective?
Correct Answer:
C
The best way to achieve the objective of discovering SaaS applications and blocking access to unapproved or identified as risky ones is to implement cloud infrastructure to proxy all user web traffic and control access according to centralized policy (C). This solution would allow the security architect to inspect all web traffic and enforce access control policies centrally. This solution also allows the security architect to detect and block risky SaaS applications.
Reference: CompTIA Advanced Security Practitioner (CASP+) Study Guide: Chapter 1:
Network Security Architecture and Design, Section 1.3: Cloud Security.

