A security architect is designing a solution for a new customer who requires significant security capabilities in its environment. The customer has provided the architect with the following set of requirements:
* Capable of early detection of advanced persistent threats.
* Must be transparent to users and cause no performance degradation.
+ Allow integration with production and development networks seamlessly.
+ Enable the security team to hunt and investigate live exploitation techniques.
Which of the following technologies BEST meets the customer's requirements for security capabilities?
Correct Answer:
B
Deception software is a technology that creates realistic but fake assets (such as servers, applications, data, etc.) that mimic the real environment and lure attackers into interacting with them. By doing so, deception software can help detect advanced persistent threats (APTs) that may otherwise evade traditional security tools12
. Deception software can also provide valuable insights into the attacker’s tactics, techniques, and procedures (TTPs) by capturing their actions and behaviors on the decoys 13.
Deception software can meet the customer’s requirements for security capabilities because:
✑ It is capable of early detection of APTs by creating attractive targets for them and
alerting security teams when they are engaged12.
✑ It is transparent to users and causes no performance degradation because it does not interfere with legitimate traffic or resources13.
✑ It allows integration with production and development networks seamlessly because it can create decoys that match the network topology and configuration13.
✑ It enables the security team to hunt and investigate live exploitation techniques because it can record and analyze the attacker’s activities on the decoys13.
A security consultant has been asked to identify a simple, secure solution for a small business with a single access point. The solution should have a single SSID and no guest access. The customer
facility is located in a crowded area of town, so there is a high likelihood that several people will come into range every day. The customer has asked that the solution require low administrative overhead
and be resistant to offline password attacks. Which of the following should the security consultant recommend?
Correct Answer:
C
WPA3-Personal is a simple, secure solution for a small business with a single access point. It uses a new security protocol called Simultaneous Authentication of Equals (SAE), which replaces the Pre-Shared Key (PSK) exchange with a more secure way to do initial key exchange. SAE also provides forward secrecy, which means that even if the password is compromised, the attacker cannot decrypt past or future data. WPA3-Personal also uses AES-128 in CCM mode as the minimum encryption algorithm, which is resistant to offline password attacks. WPA3-Personal requires low administrative overhead and supports a single SSID with no guest access. Verified References:
✑ https://www.diffen.com/difference/WPA2_vs_WPA3
✑ https://www.thewindowsclub.com/wpa3-personal-enterprise-wi-fi-encryption
✑ https://www.teldat.com/blog/wpa3-wi-fi-network-security-wpa3-personal-wpa3- enterprise/
A security analyst is investigating a possible buffer overflow attack. The following output was found on a user’s workstation:
graphic.linux_randomization.prg
Which of the following technologies would mitigate the manipulation of memory segments?
Correct Answer:
B
https://eklitzke.org/memory-protection-and-aslr
ASLR (Address Space Layout Randomization) is a technology that can mitigate the manipulation of memory segments caused by a buffer overflow attack. ASLR randomizes the location of memory segments, such as the stack, heap, or libraries, making it harder for an attacker to predict or control where to inject malicious code or overwrite memory segments. NX bit (No-eXecute bit) is a technology that can mitigate the execution of malicious code injected by a buffer overflow attack. NX bit marks certain memory segments as non-executable, preventing an attacker from running code in those segments. DEP (Data Execution Prevention) is a technology that can mitigate the execution of malicious code injected by a buffer overflow attack. DEP uses hardware and software mechanisms to mark certain memory regions as data-only, preventing an attacker from running code in those regions. HSM (Hardware Security Module) is a device that can provide cryptographic functions and key storage, but it does not mitigate the manipulation of memory segments
caused by a buffer overflow attack. Verified References: https://www.comptia.org/blog/what-is-aslr https://partners.comptia.org/docs/default- source/resources/casp-content-guide
A security analyst is reading the results of a successful exploit that was recently conducted by third-party penetration testers. The testers reverse engineered a privileged executable. In the report, the planning and execution of the exploit is detailed using logs and outputs from the test However, the attack vector of the exploit is missing, making it harder to recommend remediation’s. Given the following output: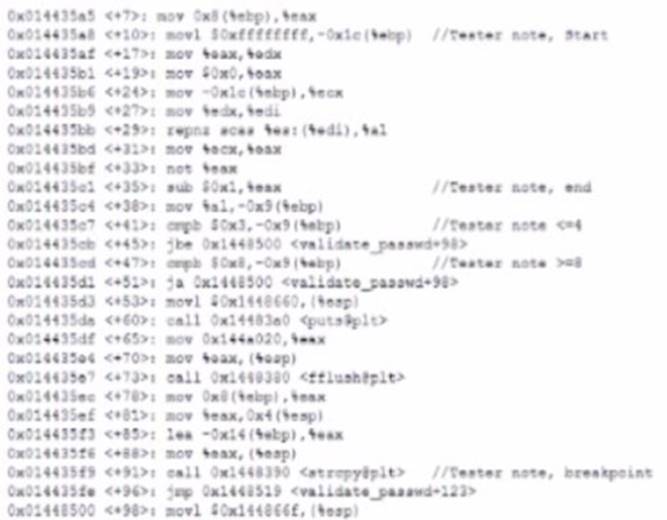
The penetration testers MOST likely took advantage of:
Correct Answer:
A
The Chief Information Security Officer (CISO) is working with a new company and needs a legal “document to ensure all parties understand their roles during an assessment. Which of the following should the CISO have each party sign?
Correct Answer:
D
Rules of engagement are legal documents that should be signed by all parties involved in an assessment to ensure they understand their roles and responsibilities. Rules of engagement define the scope, objectives, methods, deliverables, limitations, and expectations of an assessment project. They also specify the legal and ethical boundaries, communication channels, escalation procedures, and reporting formats for the assessment. Rules of engagement help to avoid misunderstandings, conflicts, or liabilities during or after an assessment.
References: [CompTIA CASP+ Study Guide, Second Edition, page 34]

