A security architect recommends replacing the company’s monolithic software application with a containerized solution. Historically, secrets have been stored in the application's configuration files. Which of the following changes should the security architect make in the new system?
Correct Answer:
A
A secrets management tool is a tool that helps companies securely store, transmit, and manage sensitive digital authentication credentials such as passwords, keys, tokens, certificates, and other secrets. A secrets management tool can help prevent secrets sprawl, enforce business policies, and inject secrets into pipelines. A secrets management tool can also help protect secrets from unauthorized access, leakage, or compromise by using encryption, tokenization, access control, auditing, and rotation. A secrets management tool is a recommended solution for replacing the company’s monolithic software application with a containerized solution, because it can provide a centralized and consistent way to manage secrets across multiple containers and environments.
* B. Saving secrets in key escrow is not a recommended solution for replacing the company’s monolithic software application with a containerized solution, because it does not address the operational challenges of managing secrets for containers. Key escrow is a process of storing cryptographic keys with a trusted third party that can release them under certain conditions. Key escrow can be useful for backup or recovery purposes, but it does not provide the same level of security and automation as a secrets management tool.
* C. Storing the secrets inside the Dockerfiles is not a recommended solution for replacing the company’s monolithic software application with a containerized solution, because it exposes the secrets to anyone who can access the Dockerfiles or the images built from them. Storing secrets inside the Dockerfiles is equivalent to hardcoding them into the application code, which is a bad practice that violates the principle of least privilege and increases the risk of secrets leakage or compromise.
* D. Running all Dockerfiles in a randomized namespace is not a recommended solution for replacing the company’s monolithic software application with a containerized solution, because it does not address the issue of storing and managing secrets for containers. Running Dockerfiles in a randomized namespace is a technique to avoid name conflicts and collisions between containers, but it does not provide any security benefits for secrets.
A financial institution has several that currently employ the following controls:
* The severs follow a monthly patching cycle.
* All changes must go through a change management process.
* Developers and systems administrators must log into a jumpbox to access the servers hosting the data using two-factor authentication.
* The servers are on an isolated VLAN and cannot be directly accessed from the internal production network.
An outage recently occurred and lasted several days due to an upgrade that circumvented the approval process. Once the security team discovered an unauthorized patch was installed, they were able to resume operations within an hour. Which of the following should the security administrator recommend to reduce the time to resolution if a similar incident occurs in the future?
Correct Answer:
B
A security analyst is concerned that a malicious piece of code was downloaded on a Linux system. After some research, the analyst determines that the suspected piece of code is performing a lot of input/output (I/O) on the disk drive.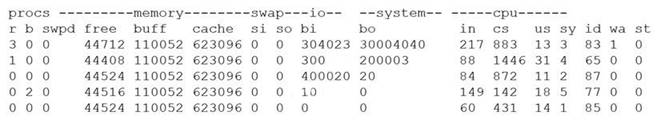
Based on the output above, from which of the following process IDs can the analyst begin an investigation?
Correct Answer:
D
The process ID 87 can be the starting point for an investigation of a possible buffer overflow attack, as it shows a high percentage of CPU utilization (99.7%) and a suspicious command name (graphic.linux_randomization.prg). A buffer overflow attack is a type of attack that exploits a vulnerability in an application or system that allows an attacker to write data beyond the allocated buffer size, potentially overwriting memory segments and executing malicious code. A high CPU utilization could indicate that the process is performing intensive or abnormal operations, such as a buffer overflow attack. A suspicious command name could indicate that the process is trying to disguise itself or evade detection, such as by mimicking a legitimate program or using random characters. The other process IDs do not show signs of a buffer overflow attack, as they have low CPU utilization and normal command names. Verified References: https://www.comptia.org/blog/what-is-buffer-overflow https://partners.comptia.org/docs/default-source/resources/casp-content-guide
A threat hunting team receives a report about possible APT activity in the network. Which of the following threat management frameworks should the team implement?
Correct Answer:
B
MITRE ATT&CK is a threat management framework that provides a comprehensive and detailed knowledge base of adversary tactics and techniques based on real-world observations. It can help threat hunting teams to identify, understand, and prioritize potential threats, as well as to develop effective detection and response strategies. MITRE ATT&CK covers the entire lifecycle of a cyberattack, from initial access to impact, and provides information on how to mitigate, detect, and hunt for each technique. It also includes threat actor profiles, software descriptions, and data sources that can be used for threat intelligence and analysis. Verified References:
✑ https://attack.mitre.org/
✑ https://resources.infosecinstitute.com/topic/top-threat-modeling-frameworks-stride- owasp-top-10-mitre-attck-framework/
✑ https://www.ibm.com/topics/threat-management
A security analyst sees that a hacker has discovered some keys and they are being made
available on a public website. The security analyst is then able to successfully decrypt the data using the keys from the website. Which of the following should the security analyst recommend to protect the affected data?
Correct Answer:
E

