Due to internal resource constraints, the management team has asked the principal security architect to recommend a solution that shifts partial responsibility for application- level controls to the cloud provider. In the shared responsibility model, which of the following levels of service meets this requirement?
Correct Answer:
D
A software development company is building a new mobile application for its social media platform. The company wants to gain its users' trust by re reducing the risk of on-path attacks between the mobile client and its servers and by implementing stronger digital trust. To support users’ trust, the company has released the following internal guidelines:
* Mobile clients should verify the identity of all social media servers locally.
* Social media servers should improve TLS performance of their certificate status.
+ Social media servers should inform the client to only use HTTPS.
Given the above requirements, which of the following should the company implement? (Select TWO).
Correct Answer:
BF
OCSP stapling and HSTS are the best options to meet the requirements of reducing the risk of on-path attacks and implementing stronger digital trust. OCSP stapling allows the social media servers to improve TLS performance by sending a signed certificate status along with the certificate, eliminating the need for the client to contact the CA separately. HSTS allows the social media servers to inform the client to only use HTTPS and prevent downgrade attacks. The other options are either irrelevant or less effective for the given scenario.
A large number of emails have been reported, and a security analyst is reviewing the following information from the emails: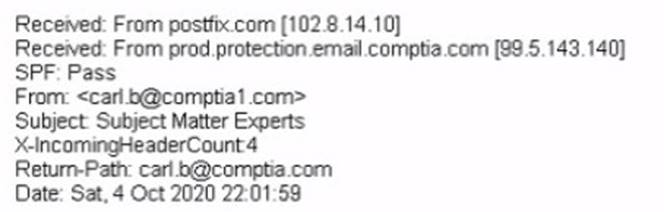
As part of the image process, which of the following is the FIRST step the analyst should take?
Correct Answer:
C
A system administrator at a medical imaging company discovers protected health information (PHI) on a general-purpose file server. Which of the following steps should the administrator take NEXT?
Correct Answer:
A
A security engineer has been informed by the firewall team that a specific Windows workstation is part of a command-and-control network. The only information the security engineer is receiving is that the traffic is occurring on a non-standard port (TCP 40322). Which of the following commands should the security engineer use FIRST to find the malicious process?
Correct Answer:
B
Netstat is a command-line tool that can be used to find the malicious process that is using a specific port on a Windows workstation. Netstat displays active TCP connections, ports on which the computer is listening, Ethernet statistics, the IP routing table, IPv4 statistics (for the IP, ICMP, TCP, and UDP protocols), and IPv6 statistics (for the IPv6, ICMPv6, TCP over IPv6, and UDP over IPv6 protocols). To find the process that is using a specific port, such as TCP 40322, the security engineer can use the following command:
netstat -ano | findstr :40322
This command will filter the netstat output by the port number and show the process identifier (PID) of the process that is using that port. The security engineer can then use the task manager or another tool to identify and terminate the malicious process by its PID. Verified References:
✑ https://docs.microsoft.com/en-us/windows-server/administration/windows-commands/netstat
✑ https://www.howtogeek.com/28609/how-can-i-tell-what-is-listening-on-a-tcpip-port- in-windows/

