A penetration tester is conducting an assessment on Comptia.org and runs the following command from a coffee shop while connected to the public Internet: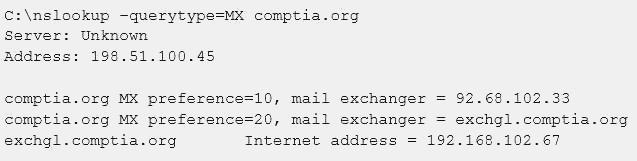
Which of the following should the penetration tester conclude about the command output?
Correct Answer:
B
An organization has established the following controls matrix: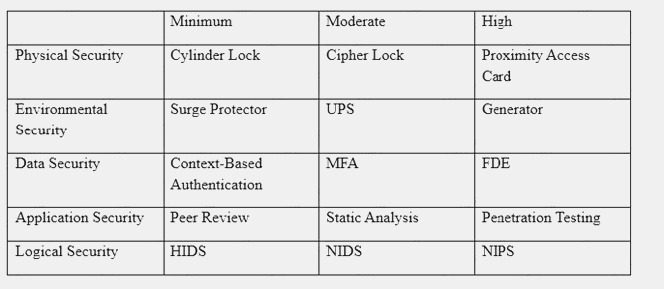
The following control sets have been defined by the organization and are applied in aggregate fashion:
Systems containing PII are protected with the minimum control set. Systems containing medical data are protected at the moderate level. Systems containing cardholder data are protected at the high level.
The organization is preparing to deploy a system that protects the confidentially of a database containing PII and medical data from clients. Based on the controls classification, which of the following controls would BEST meet these requirements?
Correct Answer:
D
During a recent audit of servers, a company discovered that a network administrator, who required
remote access, had deployed an unauthorized remote access application that communicated over common ports already allowed through the firewall. A network scan showed that this remote access application had already been installed on one third of the servers in the company. Which of the following is the MOST appropriate action that the company should take to provide a more appropriate solution?
Correct Answer:
C
A Secure Sockets Layer (SSL) virtual private network (VPN) would provide the network administrator who requires remote access a secure and reliable method of accessing the system over the Internet. Security Assertion Markup Language (SAML) standards for federation will provide cross-web service authentication and authorization.
Incorrect Answers:
A: Blocking the application would prevent the network administrator who requires remote access from accessing the system. While this will address the presence of the unauthorized remote access application, it will not address the network administrator’s need for remote access.
B: Installing the unauthorized remote access application on the rest of the servers would not be an “appropriate” solution. An appropriate solution would provide a secure form of remote access to the network administrator who requires remote access.
D: An access control list (ACL) is used for packer filtering and for selecting types of traffic to be analyzed, forwarded, or blocked by the firewall or device. The ACL may block traffic based on source and destination address, interface, port, protocol, thresholds and various other criteri
A. However,
network address translation (NAT) is not used for remote access. It is used to map private IPv4 addresses to a single public IPv4 address, allowing multiple internal hosts with private IPv4 addresses to access the internet via the public IPv4 address.
References:
BOOK pp. 28, 40-41, 110-112, 138. 335-336 htHYPERLINK
"https://en.wikipedia.org/wiki/Network_address_translation"tps://en.wikipedia.org/wiki/Network_ address_translation
Engineers at a company believe a certain type of data should be protected from competitors, but the data owner insists the information is not sensitive. An information security engineer is implementing controls to secure the corporate SAN. The controls require dividing data into four groups: nonsensitive, sensitive but accessible, sensitive but export-controlled, and extremely sensitive. Which of
the following actions should the engineer take regarding the data?
Correct Answer:
C
Company policy requires that all unsupported operating systems be removed from the network. The security administrator is using a combination of network based tools to identify such systems for the purpose of disconnecting them from the network. Which of the following tools, or outputs from the tools in use, can be used to help the security administrator make an approximate determination of the operating system in use on the local company network? (Select THREE).
Correct Answer:
AFG
Banner grabbing and operating system identification can also be defined as fingerprinting the TCP/IP stack. Banner grabbing is the process of opening a connection and reading the banner or response sent by the application.
The output displayed in option F includes information commonly examined to fingerprint the OS. Nmap provides features that include host discovery, as well as service and operating system detection.
Incorrect Answers:
B: A password cracker is used to recover passwords from data that have been stored in or transmitted by a computer system.
C: This answer is invalid as port 443 is used for HTTPS, not HTTP.
D: This web address link will not identify unsupported operating systems for the purpose of disconnecting them from the network.
E: The dig (domain information groper) command is a network administration command-line tool for
querying Domain Name System (DNS) name servers. References: https://en.wikipedia.org/wiki/Dig_(command) https://en.wikipedia.org/wiki/Password_cracking https://en.wikipediHYPERLINK
"https://en.wikipedia.org/wiki/List_of_TCP_and_UDP_port_numbers"a.org/wiki/List_of_TCP_and_U DP_port_numbers
http://luizfirmino.blogspot.co.za/2011/07/understand-banner-grabbHYPERLINK "http://luizfirmino.blogspot.co.za/2011/07/understand-banner-grabbing-usingos. html?view=classic"ing-using-os.html?view=classic
Gregg, Michael, and Billy Haines, CASP CompTIA Advanced Security Practitioner Study Guide, John Wiley & Sons, Indianapolis, 2012, pp. 174, 175

