A new web based application has been developed and deployed in production. A security engineer decides to use an HTTP interceptor for testing the application. Which of the following problems would MOST likely be uncovered by this tool?
Correct Answer:
A
A HTTP Interceptor is a program that is used to assess and analyze web traffic thus it can be used to indicate that input validation was only enabled on the client side.
Incorrect Answers:
B: Assessing and analyzing web traffic is not used to enumerate backend SQL database tables and column names.
C: HTTP methods such as Delete that the server has denied are not performed by the HTTP interceptor.
D: Application fuzzing is not performed by the HTTP interceptor tool. References:
Gregg, Michael, and Billy Haines, CASP CompTIA Advanced Security Practitioner Study Guide, John Wiley & Sons, Indianapolis, 2012, p. 181
Company A has noticed abnormal behavior targeting their SQL server on the network from a rogue IP
address. The company uses the following internal IP address ranges: 192.10.1.0/24 for the corporate site and 192.10.2.0/24 for the remote site. The Telco router interface uses the 192.10.5.0/30 IP range.
Instructions: Click on the simulation button to refer to the Network Diagram for Company A. Click on Router 1, Router 2, and the Firewall to evaluate and configure each device.
Task 1: Display and examine the logs and status of Router 1, Router 2, and Firewall interfaces.
Task 2: Reconfigure the appropriate devices to prevent the attacks from continuing to target the SQL server and other servers on the corporate network.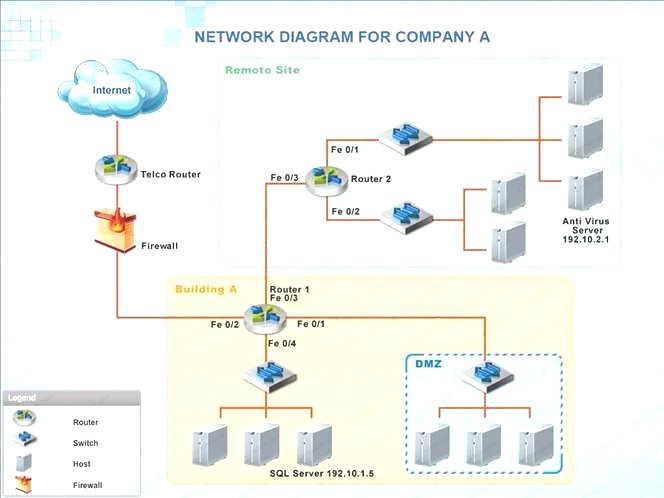

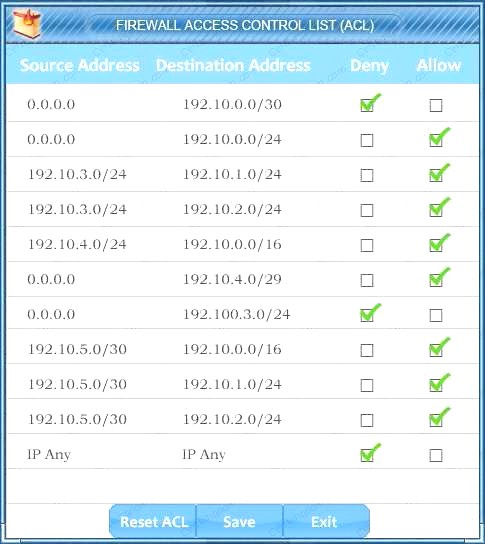
Correct Answer:
A
An organization has employed the services of an auditing firm to perform a gap assessment in preparation for an upcoming audit. As part of the gap assessment, the auditor supporting the
assessment recommends the organization engage with other industry partners to share information about emerging attacks to organizations in the industry in which the organization functions. Which of the following types of information could be drawn from such participation?
Correct Answer:
F
The risk subcommittee of a corporate board typically maintains a master register of the most prominent risks to the company. A centralized holistic view of risk is particularly important to the corporate Chief Information Security Officer (CISO) because:
Correct Answer:
A
News outlets are beginning to report on a number of retail establishments that are experiencing payment card data breaches. The data exfiltration is enabled by malware on a compromised computer. After the initial explogt, network mapping and fingerprinting is conducted to prepare for further explogtation. Which of the following is the MOST effective solution to protect against unrecognized malware infections?
Correct Answer:
B
In essence a whitelist screening will ensure that only acceptable applications are passed / or granted access.
Incorrect Answers:
A: Removing all local administrator permissions and changing to cloud aware is not going to keep unrecognized malware infections at bay.
C: Heuristic based IDS will only look for deviation of normal behavior of an application or service and thus is useful against unknown and polymorphic viruses.
D: Modifying the router configuration to pass all the network traffic via a new proxy server is not the same as protecting against unrecognized malware infections because the company’s malware detection program in use is still the same.
References:
Conklin, Wm. Arthur, Gregory White and Dwayne Williams, CASP CompTIA Advanced Security Practitioner Certification Study Guide (Exam CAS-001), McGraw-Hill, Columbus, 2012, p. 227 Gregg, Michael, and Billy Haines, CASP CompTIA Advanced Security Practitioner Study Guide, John Wiley & Sons, Indianapolis, 2012, p. 125

