A large hospital has implemented BYOD to allow doctors and specialists the ability to access patient medical records on their tablets. The doctors and specialists access patient records over the hospital’s guest WiFi network which is isolated from the internal network with appropriate security controls. The patient records management system can be accessed from the guest network and require two factor authentication. Using a remote desktop type interface, the doctors and specialists can interact with the hospital’s system. Cut and paste and printing functions are disabled to prevent the copying of data to BYOD devices. Which of the following are of MOST concern? (Select TWO).
Correct Answer:
AD
Privacy could be compromised because patient records can be from a doctor’s personal device. This can then be shown to persons not authorized to view this information. Similarly, the doctor’s personal device could have malware on it.
Incorrect Answers:
B: Device encryption is a BYOD concern, but the question asks “Which of the following are of MOST concern?” Patient privacy and Malware threats would be of more concern.
C: The guest WiFi network is isolated from the internal network with appropriate security controls and the doctors and specialists can interact with the hospital’s system via a remote desktop type interface.
E: Remote wiping is a BYOD concern, but the question asks “Which of the following are of MOST concern?” Patient privacy and Malware threats would be of more concern.
References:
http://www.gwava.com/blog/top-10-byod-business-concerns
In a situation where data is to be recovered from an attacker’s location, which of the following are the FIRST things to capture? (Select TWO).
Correct Answer:
CE
An exact copy of the attacker’s system must be captured for further investigation so that the original data can remain unchanged. An analyst will then start the process of capturing data from the most volatile to the least volatile.
The order of volatility from most volatile to least volatile is as follows: Data in RAM, including CPU cache and recently used data and applications Data in RAM, including system and network processes
Swap files (also known as paging files) stored on local disk drives Data stored on local disk drives
Logs stored on remote systems Archive media
Incorrect Answers:
A: Removable media is not regarded as volatile data.
B: Passwords written on scrap paper is not regarded as volatile data. D: Documents on the printer is not regarded as volatile data.
F: Data stored on the system hard drive is lower in the order of volatility compared to system memory.
References:
Gregg, Michael, and Billy Haines, CASP CompTIA Advanced Security Practitioner Study Guide, John Wiley & Sons, Indianapolis, 2012, pp. 250-254
http://blogs.getcertifiedgetahead.com/security-forensic-pHYPERLINK "http://blogs.getcertifiedgetahead.com/security-forensic-performance-basedquestion/" erformaHYPERLINK "http://blogs.getcertifiedgetahead.com/security-forensicperformance- based-question/"nce-based-question/
A security incident responder discovers an attacker has gained access to a network and has overwritten key system files with backdoor software. The server was reimaged and patched offline. Which of the following tools should be implemented to detect similar attacks?
Correct Answer:
CD
A systems administrator has installed a disk wiping utility on all computers across the organization and configured it to perform a seven-pass wipe and an additional pass to overwrite the disk with zeros. The company has also instituted a policy that requires users to erase files containing sensitive information when they are no longer needed.
To ensure the process provides the intended results, an auditor reviews the following content from a randomly selected decommissioned hard disk: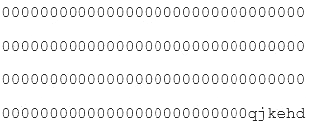
Which of the following should be included in the auditor’s report based in the above findings?
Correct Answer:
A
An investigator wants to collect the most volatile data first in an incident to preserve the data that runs the highest risk of being lost. After memory, which of the following BEST represents the remaining order of volatility that the investigator should follow?
Correct Answer:
C
The order in which you should collect evidence is referred to as the Order of volatility. Generally, evidence should be collected from the most volatile to the least volatile. The order of volatility from most volatile to least volatile is as follows:
Data in RAM, including CPU cache and recently used data and applications Data in RAM, including system and network processes
Swap files (also known as paging files) stored on local disk drives Data stored on local disk drives
Logs stored on remote systems Archive media
Incorrect Answers:
A: System and network processes are more volatile than file system information and swap files. B: System and network processes are more volatile than raw disk blocks.
D: System and network processes are more volatile than raw disk blocks and swap files. References:
http://blogs.getcertifiedgetahead.com/security-forensic-performance-baseHYPERLINK "http://blogs.getcertifiedgetahead.com/security-forensic-performance-based-question/"d-question/

