- (Topic 8)
You provide an Azure API Management managed web service lo clients. The back end web service implements HTTP Strict Transport Security (HSTS).
Every request to the backend service must include a valid HTTP authorization header. You need to configure the Azure API Management instance with an authentication policy. Which two policies can you uses? Each correct answer presents a complete solution NOTE: Each correct selection is worth one point.
Correct Answer:
AB
DRAG DROP - (Topic 8)
You are developing a serverless Java application on Azure. You create a new Azure Key Vault to work with secrets from a new Azure Functions application.
The application must meet the following requirements:
✑ Reference the Azure Key Vault without requiring any changes to the Java code.
✑ Dynamically add and remove instances of the Azure Functions host based on the number of incoming application events.
✑ Ensure that instances are perpetually warm to avoid any cold starts.
✑ Connect to a VNet.
✑ Authentication to the Azure Key Vault instance must be removed if the Azure Function application is deleted.
You need to grant the Azure Functions application access to the Azure Key Vault.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.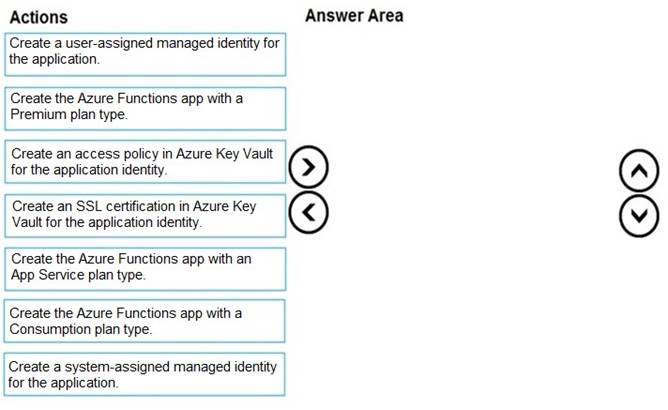
Solution:
Step 1: Create the Azure Functions app with a Consumption plan type. Use the Consumption plan for serverless.
Step 2: Create a system-assigned managed identity for the application. Create a system-assigned managed identity for your application.
Key Vault references currently only support system-assigned managed identities. User- assigned identities cannot be used.
Step 3: Create an access policy in Key Vault for the application identity.
Create an access policy in Key Vault for the application identity you created earlier. Enable the "Get" secret permission on this policy. Do not configure the "authorized application" or
applicationId settings, as this is not compatible with a managed identity.
Does this meet the goal?
Correct Answer:
A
HOTSPOT - (Topic 4)
You need to insert code at line LE03 of LoginEvent.cs to ensure that all authentication events are processed correctly.
How should you complete the code? To answer, select the appropriate options in the answer area.
NOTE:Each correct selection is worth one point.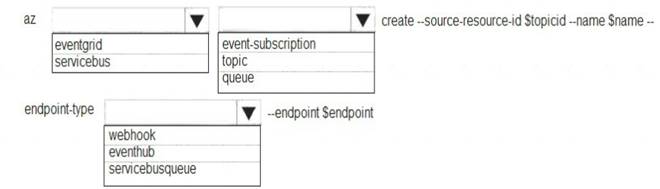
Solution:
Box 1: id
id is a unique identifier for the event.
Box 2: eventType
eventType is one of the registered event types for this event source.
Box 3: dataVersion
dataVersion is the schema version of the data object. The publisher defines the schema version.
Scenario: Authentication events are used to monitor users signing in and signing out. All authentication events must be processed by Policy service. Sign outs must be processed as quickly as possible.
The following example shows the properties that are used by all event publishers: [
{
"topic": string, "subject": string, "id": string, "eventType": string, "eventTime": string, "data":{
object-unique-to-each-publisher
},
"dataVersion": string, "metadataVersion": string
}
]
Does this meet the goal?
Correct Answer:
A
- (Topic 6)
You need to access data from the user claim object in the e-commerce web app. What should you do first?
Correct Answer:
C
Methods to Get User Identity and Claims in a .NET Azure Functions App include: ClaimsPrincipal from the Request Context
The ClaimsPrincipal object is also available as part of the request context and can be extracted from the HttpRequest.HttpContext.
User Claims from the Request Headers.
App Service passes user claims to the app by using special request headers. Reference:
https://levelup.gitconnected.com/four-alternative-methods-to-get-user-identity-and-claims-in-a-net-azurefunctions-app-df98c40424bb
- (Topic 8)
You are developing several Azure API Management (APIM) hosted APIs.
You must transform the APIs to hide private backend information and obscure the technology stack used to implement the backend processing.
You need to protect all APIs. What should you do?
Correct Answer:
A

