HOTSPOT - (Topic 3)
You need to retrieve the database connection string.
Which values should you use? To answer, select the appropriate options in the answer area.
NOTE:Each correct selection is worth one point.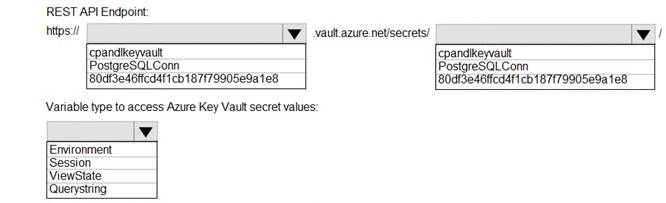
Solution:
Azure database connection string retrieve REST API vault.azure.net/secrets/ Box 1: cpandlkeyvault
We specify the key vault, cpandlkeyvault.
Scenario: The database connection string is stored in Azure Key Vault with the following attributes:
Azure Key Vault name: cpandlkeyvault Secret name: PostgreSQLConn
Id: 80df3e46ffcd4f1cb187f79905e9a1e8
Box 2: PostgreSQLConn
We specify the secret, PostgreSQLConn
Example, sample request: https://myvault.vault.azure.net//secrets/mysecretname/4387e9f3d6e14c459867679a90fd0f 79?api-version=7.1
Box 3: Querystring
Does this meet the goal?
Correct Answer:
A
- (Topic 8)
You are developing a solution that will use Azure messaging services.
You need to ensure that the solution uses a publish-subscribe model and eliminates the need for constant polling.
What are two possible ways to achieve the goal? Each correct answer presents a complete solution.
NOTE:Each correct selection is worth one point.
Correct Answer:
AC
It is strongly recommended to use available messaging products and services that support a publish-subscribe model, rather than building your own. In Azure, consider using Service Bus or Event Grid. Other technologies that can be used for pub/sub messaging include Redis, RabbitMQ, and Apache Kafka.
Reference:
https://docs.microsoft.com/en-us/azure/architecture/patterns/publisher-subscriber
- (Topic 8)
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this question, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You are developing a solution that will be deployed to an Azure Kubernetes Service (AKS) cluster. The solution will include a custom VNet, Azure Container Registry images, and an Azure Storage account.
The solution must allow dynamic creation and management of all Azure resources within the AKS cluster.
You need to configure an AKS cluster for use with the Azure APIs.
Solution: Enable the Azure Policy Add-on for Kubernetes to connect the Azure Policy service to the GateKeeper admission controller for the AKS cluster. Apply a built-in policy to the cluster.
Does the solution meet the goal?
Correct Answer:
B
Instead create an AKS cluster that supports network policy. Create and apply a network to allow traffic only from within a defined namespace
References:
https://docs.microsoft.com/en-us/azure/aks/use-network-policies
- (Topic 8)
You ate developing a web application that uses the Microsoft identity platform to authenticate users and resources. The web application calls several REST APIs.
The APIs require an access token from the Microsoft identity platform. You need to request a token.
Which three properties should you use? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
Correct Answer:
ABE
HOTSPOT - (Topic 8)
You are developing an Azure Function App by using Visual Studio. The app will process orders input by an Azure Web App. The web app places the order information into Azure Queue Storage.
You need to review the Azure Function App code shown below.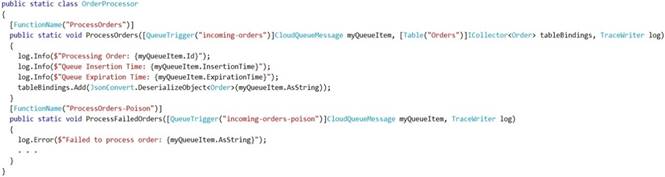
NOTE:Each correct selection is worth one point.
Solution:
Box 1: No
ExpirationTime - The time that the message expires.
InsertionTime - The time that the message was added to the queue.
Box 2: Yes
maxDequeueCount - The number of times to try processing a message before moving it to the poison queue. Default value is 5.
Box 3: Yes
When there are multiple queue messages waiting, the queue trigger retrieves a batch of messages and invokes function instances concurrently to process them. By default, the batch size is 16. When the number being processed gets down to 8, the runtime gets another batch and starts processing those messages. So the maximum number of concurrent messages being processed per function on one virtual machine (VM) is 24.
Box 4: Yes References:
https://docs.microsoft.com/en-us/azure/azure-functions/functions-bindings-storage-queue
Does this meet the goal?
Correct Answer:
A

